The Five Biggest Trends Driving Software Licensing and Entitlement Management
Thales Cloud Protection & Licensing
JANUARY 9, 2023
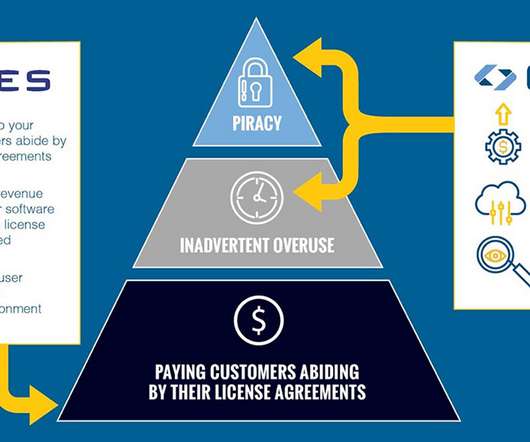
The Five Biggest Trends Driving Software Licensing and Entitlement Management. They found five major trends that are pushing the Software Licensing Management and Entitlement Management markets forward now and over the next seven years. It prides itself on its cutting-edge research tools and pioneering research software.






















Let's personalize your content