HackerOne awarded over $300 million bug hunters
Security Affairs
OCTOBER 30, 2023
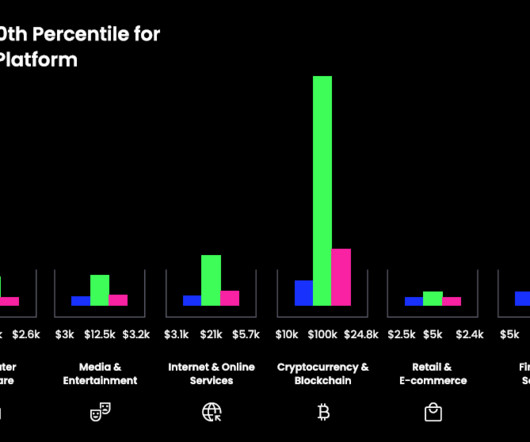
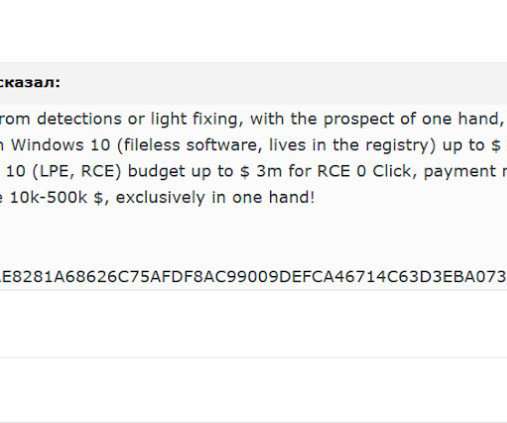
HackerOne announced that it has awarded over $300 million bug hunters as part of its bug bounty programs since the launch of its platform. Most of bug hunters (61%) are experimenting Generative AI (GenAI) and believe it is essential to develop a new generation of hacking tools that can help them find more vulnerabilities.






















Let's personalize your content