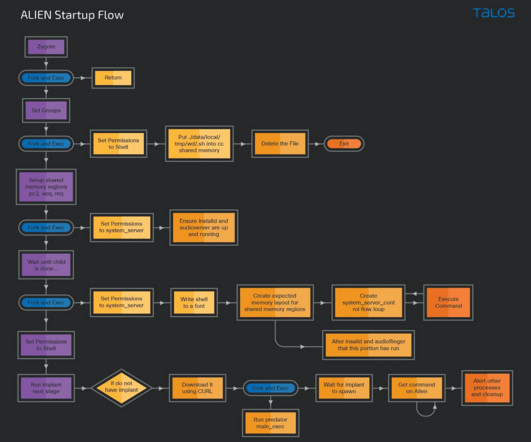
Researchers analyzed the PREDATOR spyware and its loader Alien
Security Affairs
MAY 29, 2023
“New analysis from Talos uncovered the inner workings of PREDATOR and the mechanisms it uses to communicate with the other spyware component deployed along with it known as “ALIEN.” . Alien also upgrades the existing Predator payload to a newer version if available. ALIEN calls the main_exec() function to launch PREDATOR.
















Let's personalize your content