Is it OK to train an AI on your images, without permission?
Malwarebytes
MAY 2, 2023
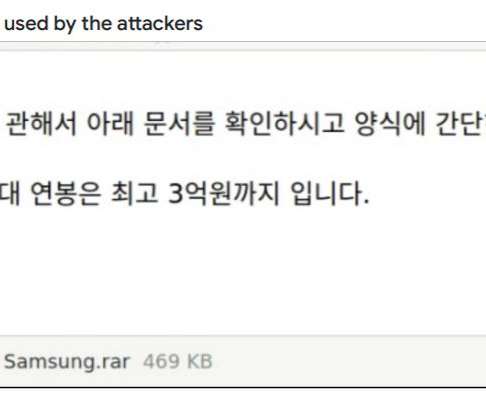
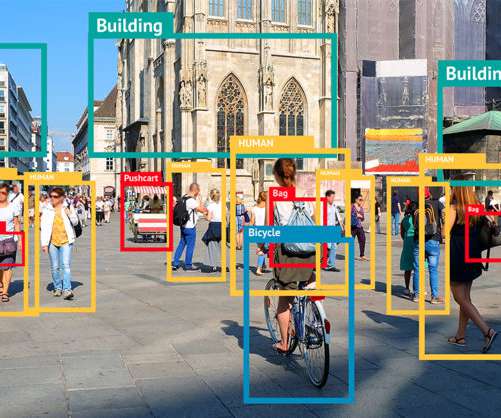
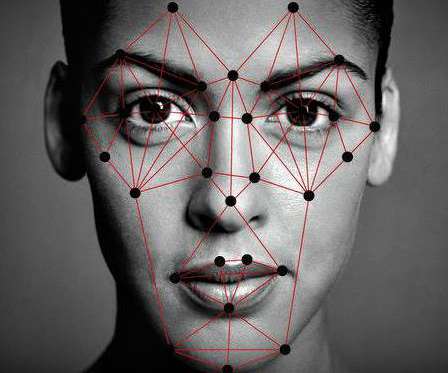
These generators are increasingly popular text-to-image services, where you enter a suggestion (“A superhero in the ocean, in the style of Van Gogh”) and it produces a visual to match. Visual artists don’t want their work being sucked up by AI tools (that make someone else money) without permission.











































Let's personalize your content