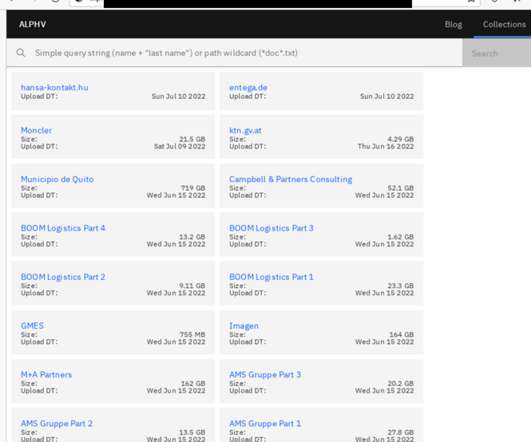
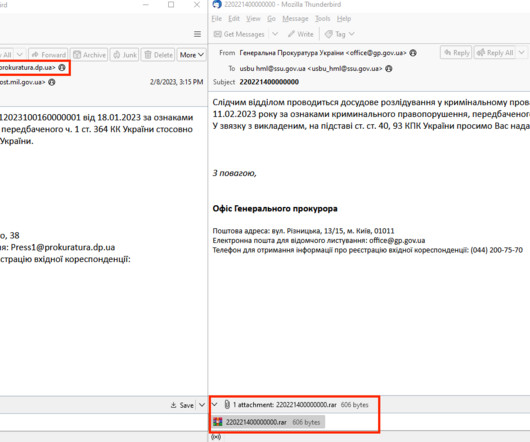
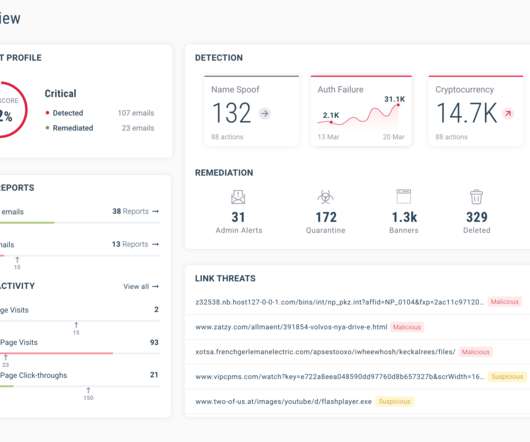
Cybercriminals launched “Leaksmas” event in the Dark Web exposing massive volumes of leaked PII and compromised data
Security Affairs
DECEMBER 28, 2023
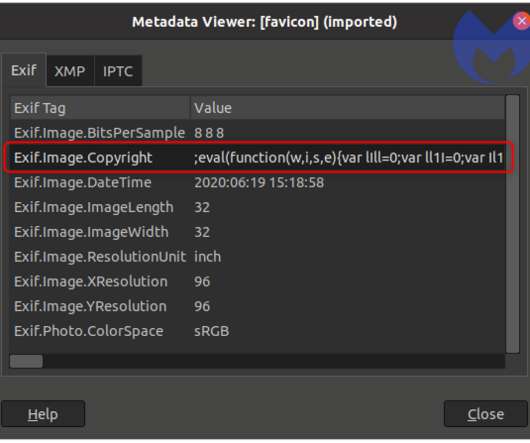
Mitigating this damage is particularly challenging due to the intricate interconnection between personal data and digital identity. It will inevitably result in them facing a host of adverse effects, such as account takeovers (ATO), business email compromises (BEC), identity theft, and financial fraud.









































Let's personalize your content