How we built the new Find My Device network with user security and privacy in mind
Google Security
APRIL 8, 2024
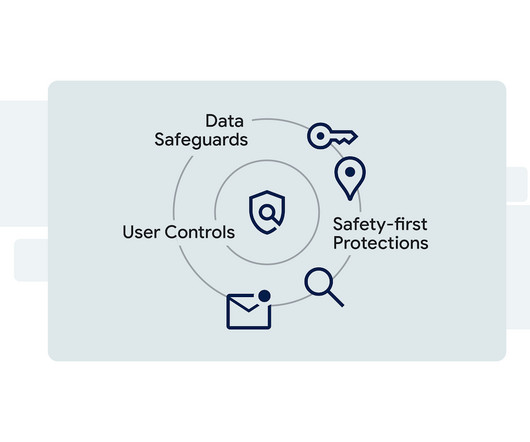
During development, it was important for us to ensure the new Find My Device was secure by default and private by design. Next, we developed multi-layered protections across three main areas: data safeguards, safety-first protections, and user controls. Imagine you drop your keys at a cafe.















































Let's personalize your content