Privacy Device Designed to Defend Against Illegal Wireless Tracking
SecureWorld News
FEBRUARY 10, 2023
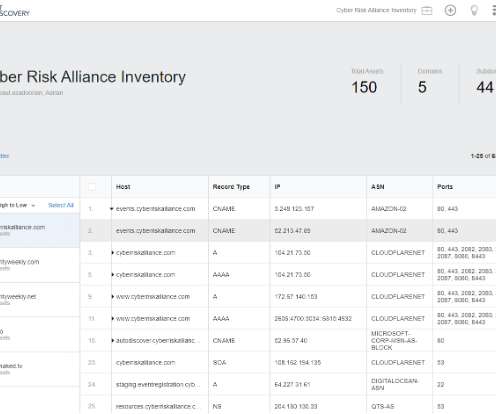
RELATED: Tech CEO Fined $410K for Selling Illegal Spyware ] One company that is helping fight against the illegal use of BLE trackers is Berkeley Varitronics Systems (BVS). BVS has been at the forefront of the wireless security industry for 50 years, designing, building, and shipping thousands of innovative security products.
















Let's personalize your content