CVE-2024-21378 — Remote Code Execution in Microsoft Outlook
NetSpi Technical
MARCH 11, 2024
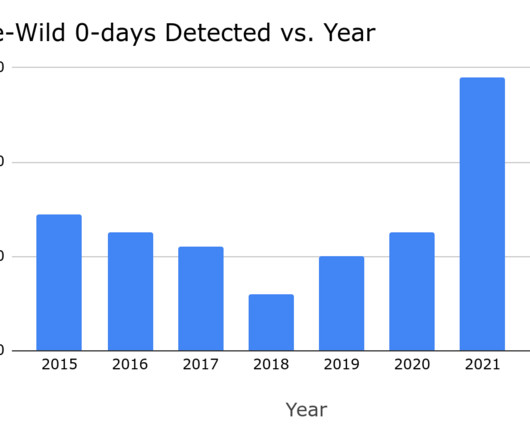
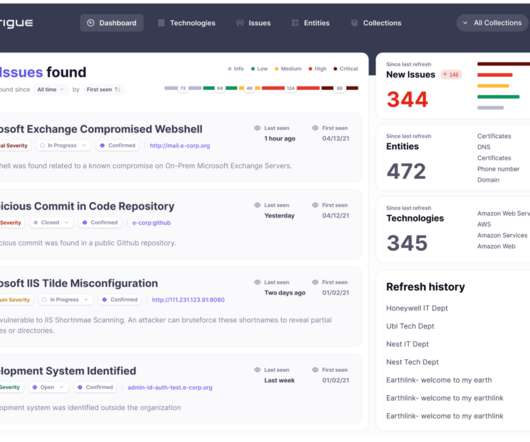
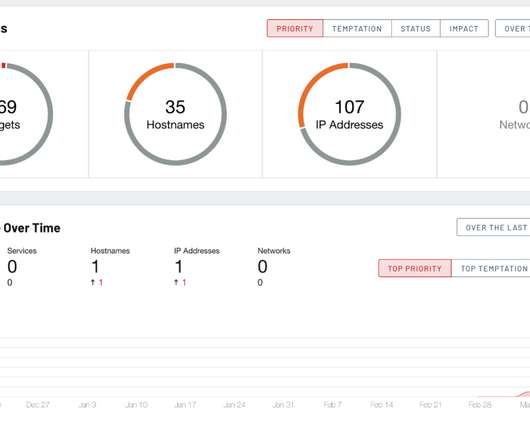
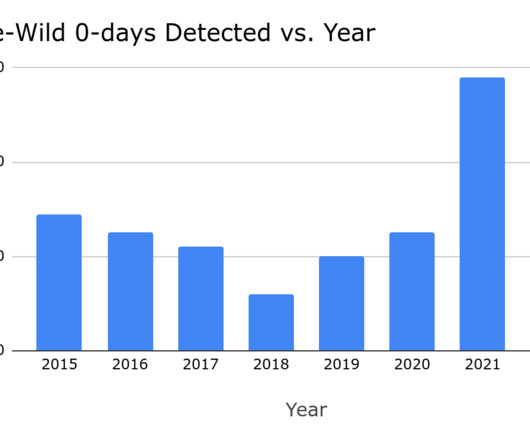
In-Depth Review Setting the Stage Colloquially, we consider this to be the fourth iteration of a series of attacks based on the premise of using compromised credentials to sync objects through Exchange. In 2023 NetSPI discovered that Microsoft Outlook was vulnerable to authenticated remote code execution (RCE) via synced form objects.













































Let's personalize your content