Topic-specific example 11/11: secure development
Notice Bored
OCTOBER 22, 2021
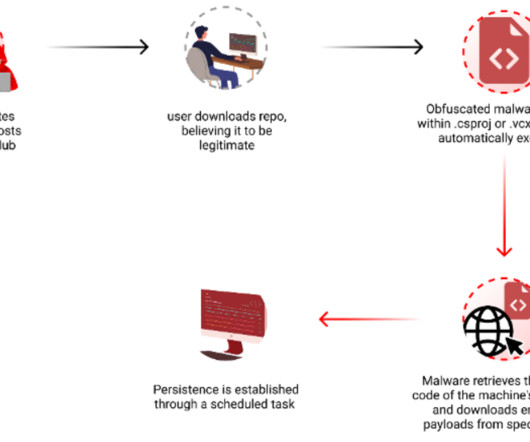
The final topic-specific policy example from ISO/IEC 27002:2022 is another potential nightmare for the naïve and inexperienced policy author. Despite the context, the title of the standard's policy example ("secure development") doesn't explicitly refer to software or IT. Yes, even security policies get developed!
















































Let's personalize your content