Threat Model Thursday: 5G Infrastructure
Adam Shostack
JULY 1, 2021
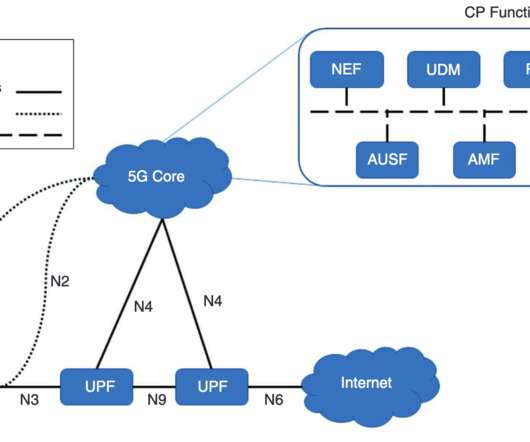
Are end user devices in scope? “Telesurgical devices” are explicitly mentioned, are they in scope? Why anyone would run a telesurgical device over a long-range radio, rather than switching to more reliable fiber as soon as economically feasible is beyond me. (Why Or neither, because end devices are not trusted?).
















































Let's personalize your content