News alert: Picus Security attack simulations report reveals organizations prevent 6 of 10 attacks
The Last Watchdog
AUGUST 8, 2023
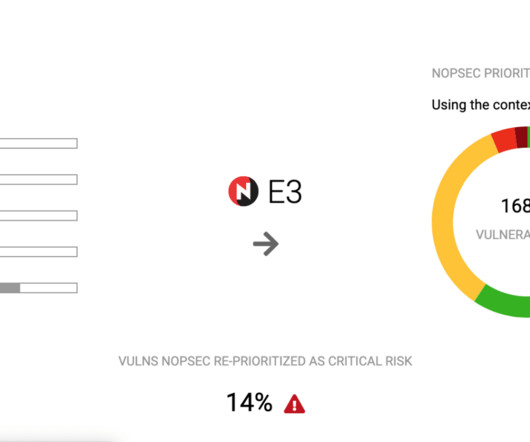
8, 2023 – Picus Security , the pioneer of Breach and Attack Simulation (BAS) technology, has released The Blue Report 2023. According to the report, security teams make four trade-offs in deciding: •Which attacks to prioritize. However, some attack types are prevented far more effectively than others.



















































Let's personalize your content