How Coinbase Phishers Steal One-Time Passwords
Krebs on Security
OCTOBER 13, 2021
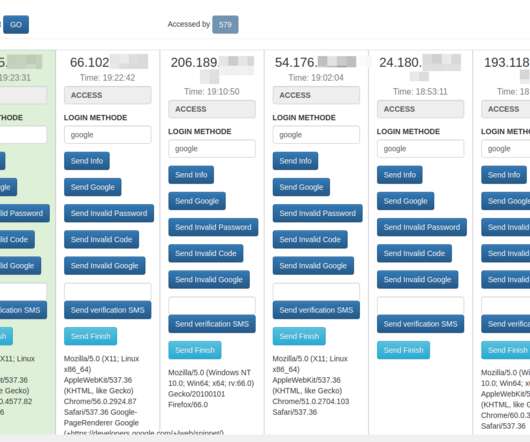
A recent phishing campaign targeting Coinbase users shows thieves are getting cleverer about phishing one-time passwords (OTPs) needed to complete the login process. A Google-translated version of the now-defunct Coinbase phishing site, coinbase.com.password-reset[.]com. The Coinbase phishing panel. million Italians.













Let's personalize your content