Ransomware turncoat leaks Conti data, lifts the lid on the ransomware business
Malwarebytes
AUGUST 10, 2021
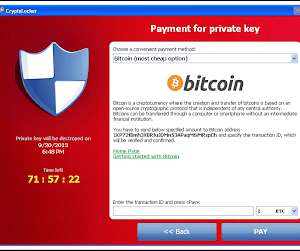
Last week, The Record broke the news that a self-described “pen tester” for the infamous Conti ransomware gang, who goes by the handle m1Geelka, had leaked manuals, technical guides, and software on the underground forum XSS. m1Geelka’s rant starts: Dumb divorce, not work.





















Let's personalize your content