GUEST ESSAY: The drivers behind persistent ransomware — and defense tactics to deploy
The Last Watchdog
SEPTEMBER 7, 2022
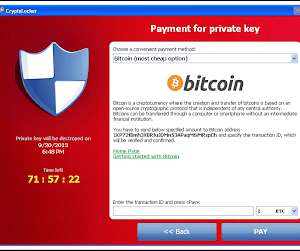
From sharing emerging threat intelligence to developing new solutions and best practices to prevent and overcome attacks, it’s possible to reduce the impact of ransomware when it happens. The increase in remote workforces and difficulty enforcing security controls with expanding perimeters has played a role in the rise of ransomware.


































Let's personalize your content