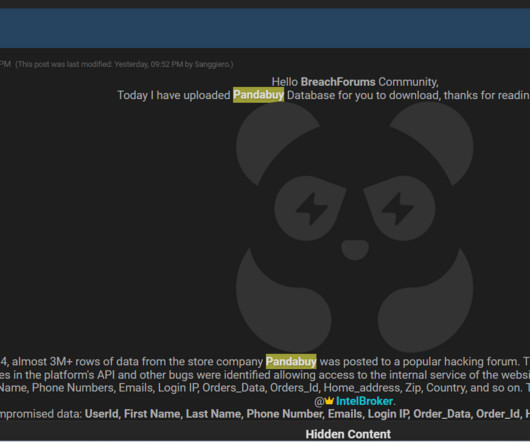
PandaBuy data breach allegedly impacted over 1.3 million customers
Security Affairs
APRIL 2, 2024
Threat actors claimed the hack of the PandaBuy online shopping platform and leaked data belonging to more than 1.3 At least two threat actors claimed the hack of the PandaBuy online shopping platform and leaked data of more than 1.3 Sanggiero said that he breached the platform with another threat actor named ‘ IntelBroker.’










































Let's personalize your content