Cisco Talos — Our not-so-secret threat intel advantage
Cisco Security
AUGUST 24, 2022
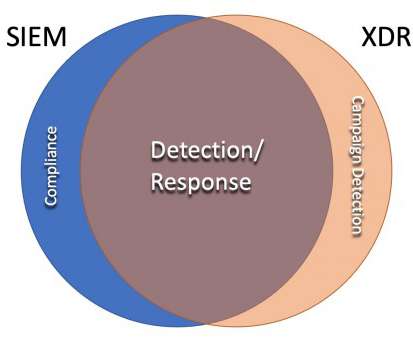
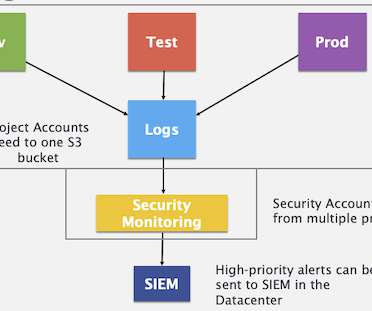
We’re very fortunate to have our security technologies powered by Cisco Talos , one of the largest and most trusted threat intelligence groups in the world. How Talos powers XDR. Security tools are only as good as the intelligence and expertise that feeds them.















Let's personalize your content