New SSH Vulnerability
Schneier on Security
NOVEMBER 15, 2023
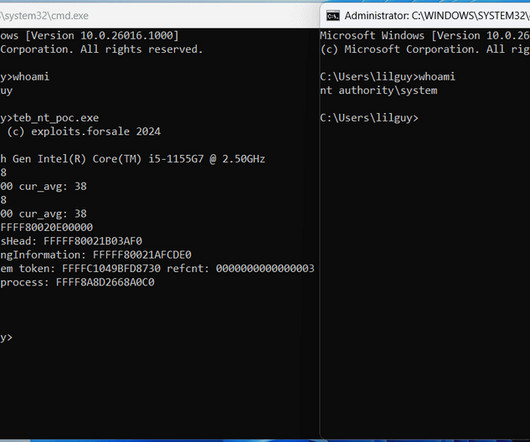
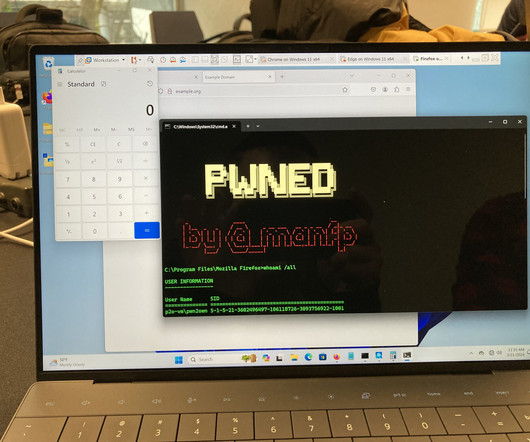
We provide a security analysis of the SSH, IKEv1, and IKEv2 protocols in this scenario, and use our attack to discover hundreds of compromised keys in the wild from several independently vulnerable implementations.













































Let's personalize your content