
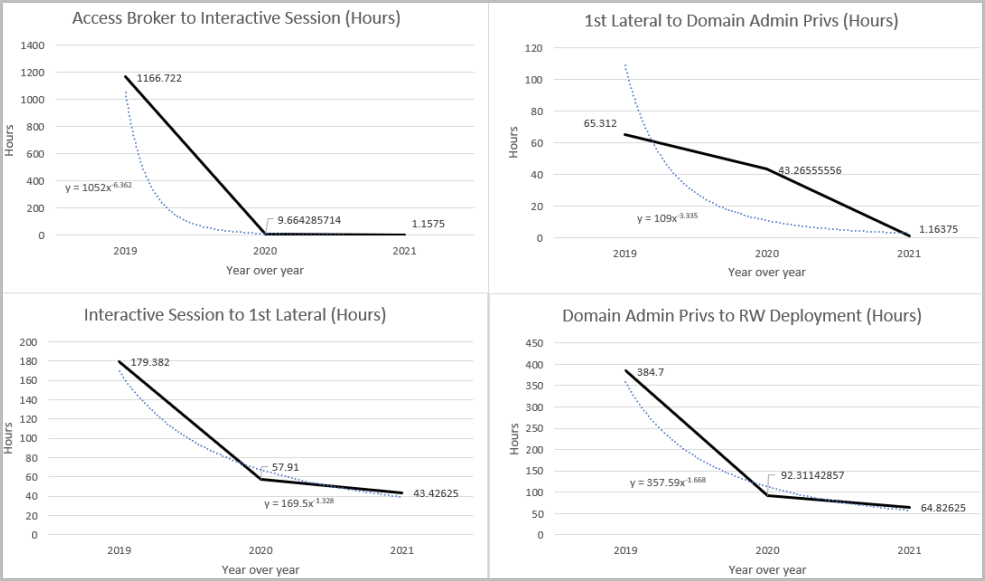
The duration of ransomware attacks in 2021 averaged 92.5 hours, measured from initial network access to payload deployment. In 2020, ransomware actors spent an average of 230 hours to complete their attacks and 1637.6 hours in 2019.
This change reflects a more streamlined approach that developed gradually over the years to make large-scale operations more profitable.
At the same time, improvements in incident response and threat detection have forced threat actors to move quicker, to leave defenders with a smaller reaction margin.
From access broker to encryption
The data was collected by researchers at IBM's X-Force team from incidents analyzed in 2021. They also noticed a closer collaboration between initial access brokers and ransomware operators.
Previously, network access brokers might wait for multiple days or even weeks before they found a buyer for their network access.
In addition, some ransomware gangs now have direct control over the initial infection vector, an example being Conti taking over the TrickBot malware operation.
Malware that breaches corporate networks is quickly leveraged to enable post-exploitation stages of the attack, sometimes completing its objectives in mere minutes.
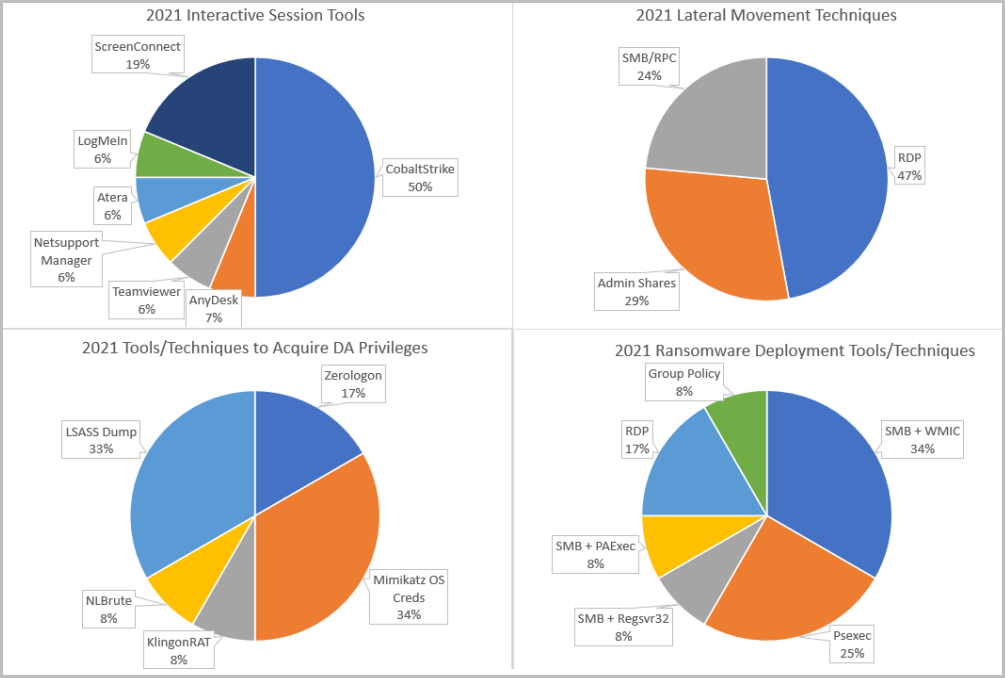
In terms of the tools and methods that ransomware actors use, Cobalt Strike is common for interactive sessions, RDP for lateral movement, Mimikatz and LSASS dump for credentials, and SMB + WMIC and Psexec are typically usd for deploying payloads on the network hosts.
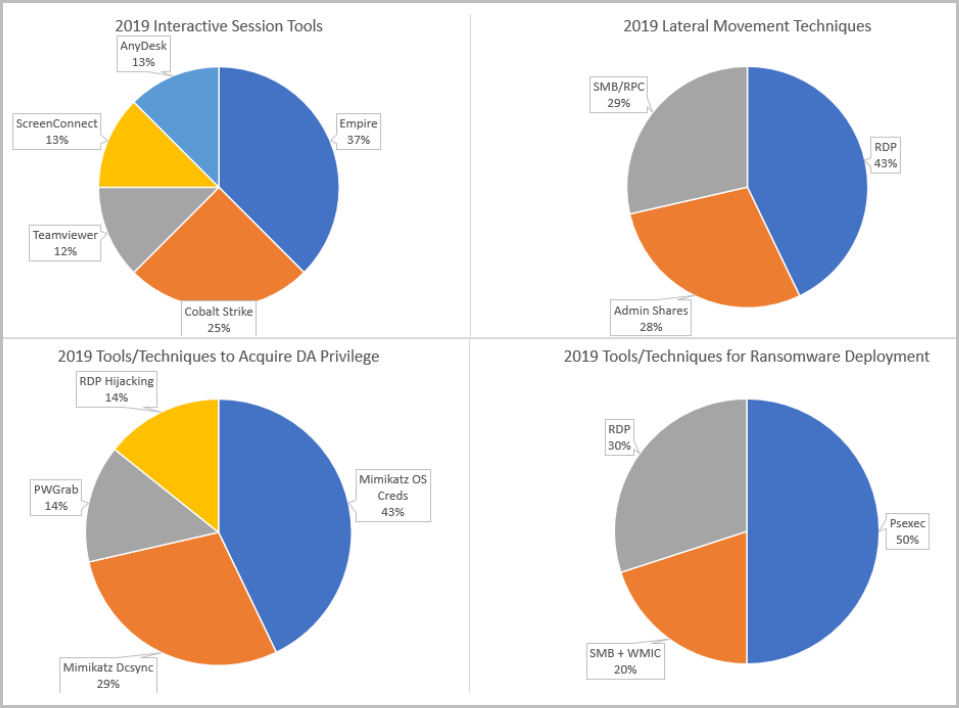
Ransomware actors used many of the same tools in 2019 but to various degrees.
Faster detection but not enough
The performance of threat detection and response systems in 2021 improved since 2019 but this was not sufficient, the researchers say.
The most impressive development in this area is endpoint detection solutions. In 2019, only 8% of targeted organizations had such a capability, while in 2021, this percentage grew to 36%.
In terms of alerts generated by security tools, IBM X-Force data shows that 42% of attacked organizations were warned in a timely manner in 2019. Last year, alerts were delivered in 64% of network intrusion cases.
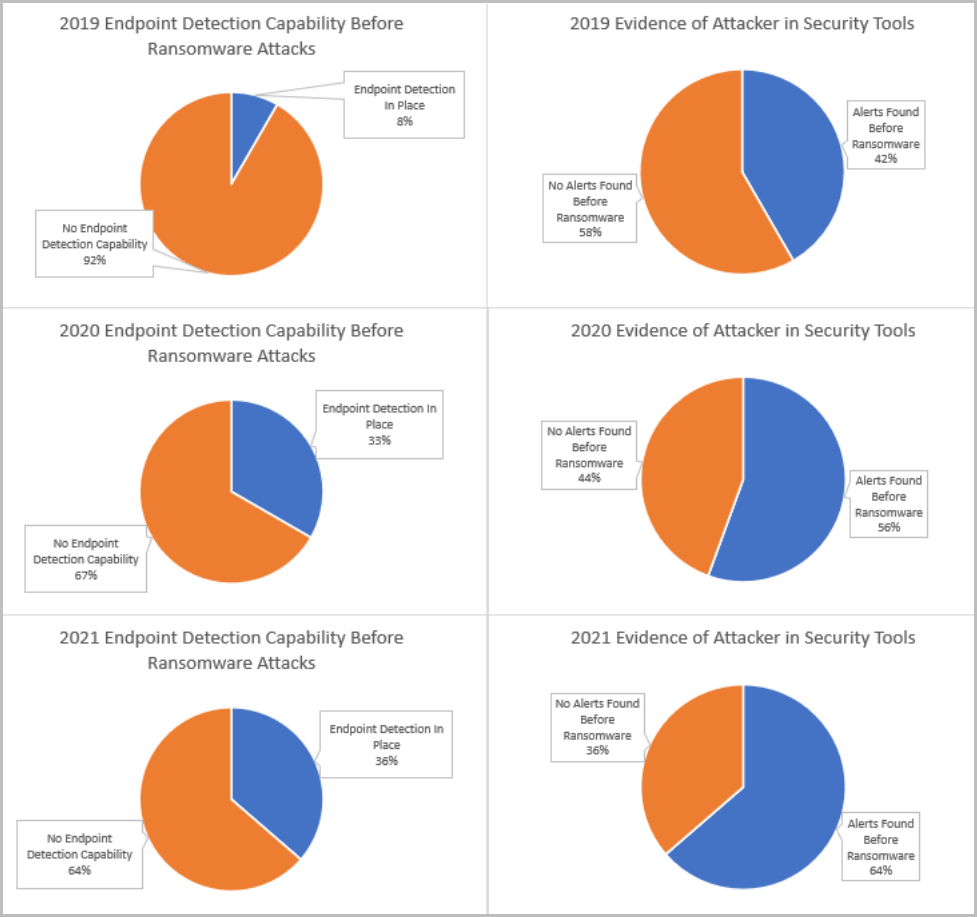
While these figures show a gradual improvement in detection, there’s still a significant gap that threat actors can take advantage of.
Outlook
Despite the defense improvements, ransomware continues to be a significant threat as actors adopted a highly targeted approach and turn to manual hacking to move inside the victim network and maintain a low profile until the final stage of the attack, system encryption.
Clearly, ransomware adversaries have gotten faster at what they do. An example from April 2022 presented a case of an IcedID malware infection leading to Quantum ransomware deployment in just 3 hours and 44 minutes.
Also, the encryption process is quicker these days. Once it starts, in many cases it's very difficult to stop it before considerable damage occurs.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now