
EXCLUSIVE: A bug in the support dashboard of Palo Alto Networks (PAN) exposed thousands of customer support tickets to an unauthorized individual, BleepingComputer has learned.
The exposed information included, names and (business) contact information of the person creating support tickets, conversations between Palo Alto Networks staff members and the customer.
Evidence shared with BleepingComputer indicates some support tickets contained attachments—like firewall logs, configuration dumps, and other debugging assets shared with the PAN staff by customers.
Palo Alto Networks, a leading provider of cybersecurity and networking products and firewalls, tells BleepingComputer it has now fixed the issue—about eight days after it was reported.
How may I help you today?
A misconfiguration in the support system of Palo Alto Networks allowed sensitive information disclosure —letting a customer access private support tickets from other companies.
A PAN customer who prefers to remain anonymous discovered the issue this month and reported it to Palo Alto Networks staff, who have now resolved the issue.
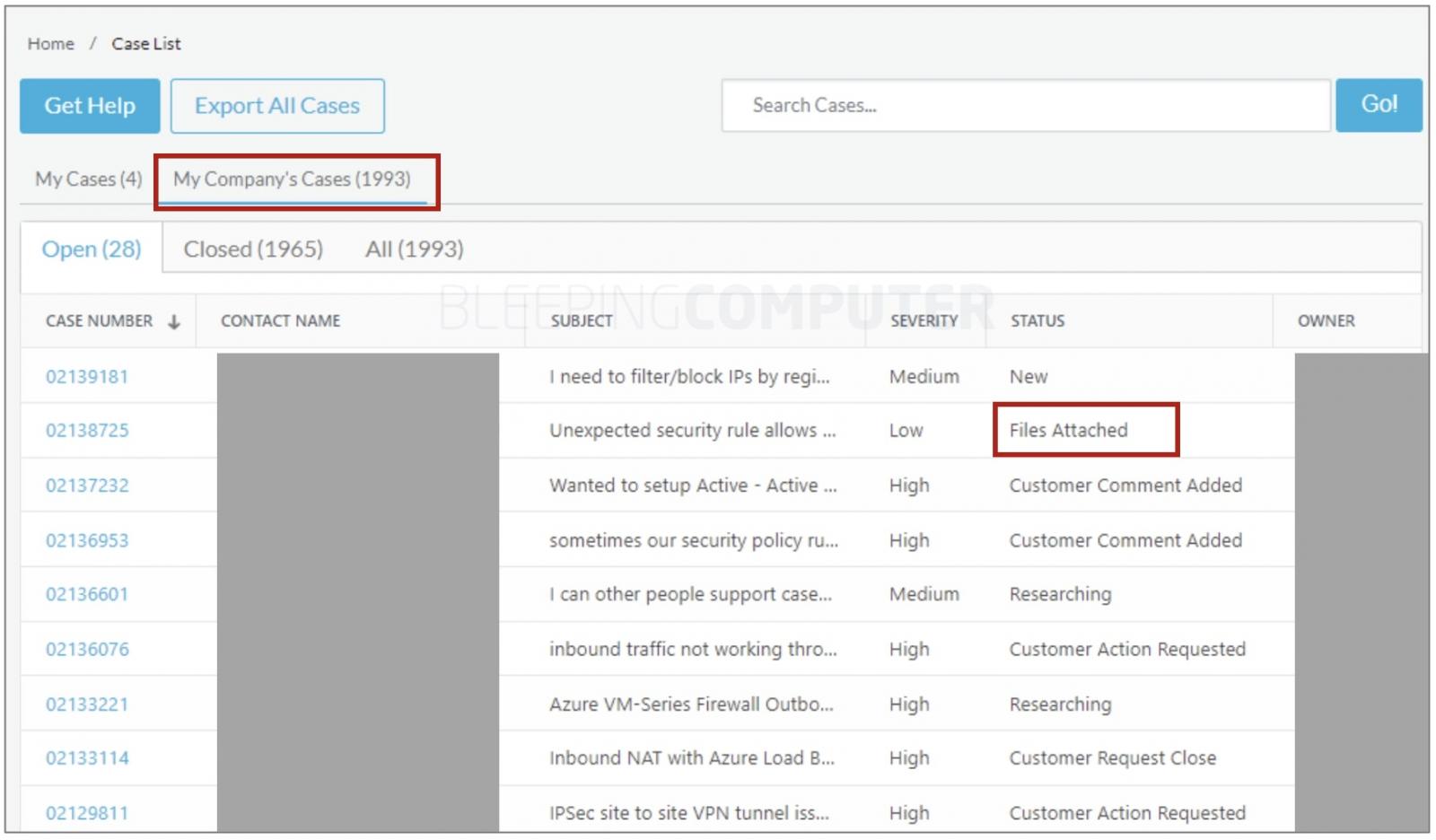
The customer further told BleepingComputer that they could see roughly 1,989 support cases that did not belong to them or their organization, and shared screenshots attesting to the fact:
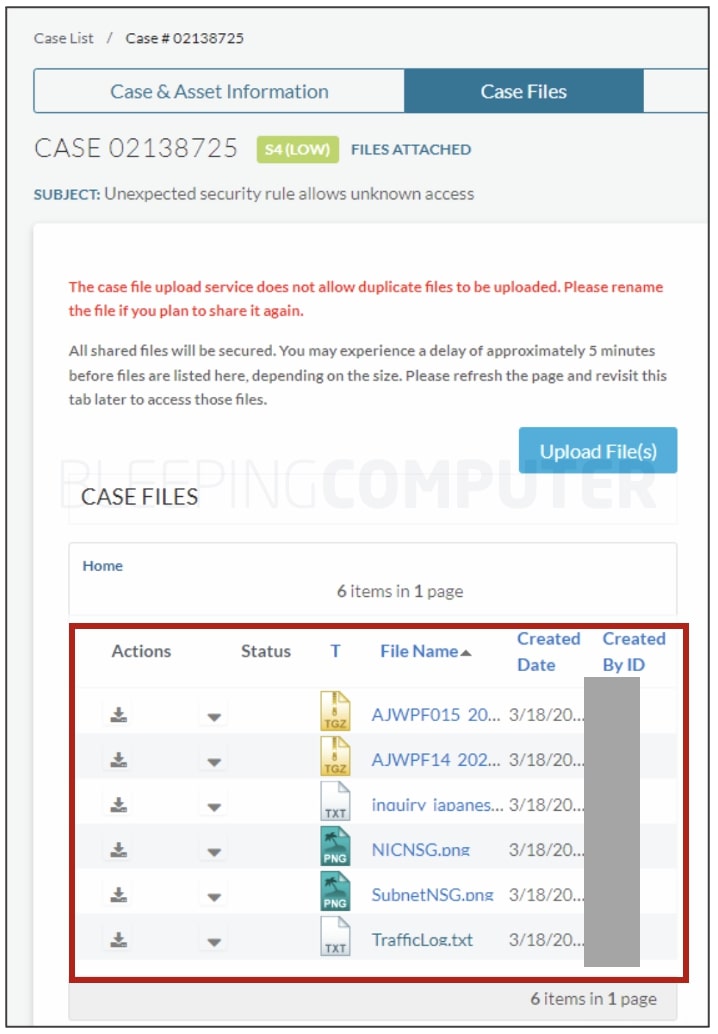
Some of these support cases had file attachments such as firewall logs, configuration dumps, network security group (NSG) layouts, images of error messages, and similar internal files shared by customers with Palo Alto Networks for troubleshooting purposes.
The screenshot shows a "download" icon next to every file. Note, the customer tipping us off did not share any of the files with BleepingComputer and claims not downloading the files either.
Some other information exposed in the support tickets included:
- Contact name, title, email address and phone number of the customer creating the tickets
- Contents of conversations between PAN support staff and customers
- PAN Product serial number and model
- Case numbers, subject line, and request severity (Critical, High, Medium, Low)
"The first problems started when I registered for a Palo Alto support account on the 10th of March," the unnamed customer tells BleepingComputer.
"After logging in, my browser would get stuck in a redirect loop when trying to access Palo Alto knowledgebase, but more importantly, it was returning 403 insufficient permissions when trying to login to Palo Alto Hub, from where Cloud Identity Engine could be installed."
The customer raised this issue with PAN support and was told their access to the Palo Alto Hub was "fixed."
"However, to my surprise, when I logged in to the support portal, I was able to see not only the support cases I raised, but also ~1990 support cases under 'My Company's Cases' tab," further explains the user.
Palo Alto Networks: 'no data was downloaded or altered'
On realizing the access blunder, the customer tells BleepingComputer that they promptly notified Palo Alto Networks, both by raising a "critical support request" and contacting select PAN members on LinkedIn.
BleepingComputer reached out to PAN to better understand the scope and impact of this data leak.
PAN says that no data was downloaded and implies that the scope of the leak remained limited to just one customer:
"We were notified of an issue that allowed an authorized customer to view a small subset of support cases, which they typically would not be able to view," a Palo Alto Networks spokesperson told BleepingComputer.
"We immediately initiated an investigation and identified it was due to a permission misconfiguration error in a support system."
"Our analysis confirmed no data was downloaded or altered, and the issue was immediately remediated."
Note, however, the bug fix took approximately eight days, after which the aforementioned customer's access to the 1,900 unrelated tickets was revoked.
PAN did not answer if it notified customers whose information was impacted by the data leak bug, or if it was planning on doing so.
At this time, the company says, there is no customer action required and that it is confident that its products and services are secure.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now