
Pwn2Own 2021 ended with contestants earning a record $1,210,000 for exploits and exploits chains demoed over the course of three days.
During this year's hacking competition, 23 teams and researchers and security researchers targeted multiple products in the web browsers, virtualization, servers, local escalation of privilege, and enterprise communications categories.
The total prize pool for Pwn2Own 2021 was over $1,500,000 in cash and included a Tesla Model 3.
While no team signed up to hack a Tesla car this year, the contestants gained code execution and escalated privileges on fully patched systems after hacking Windows 10, Microsoft Teams, Microsoft Exchange, Ubuntu Desktop, Google Chrome, Microsoft Edge, Safari, and Parallels Desktop.
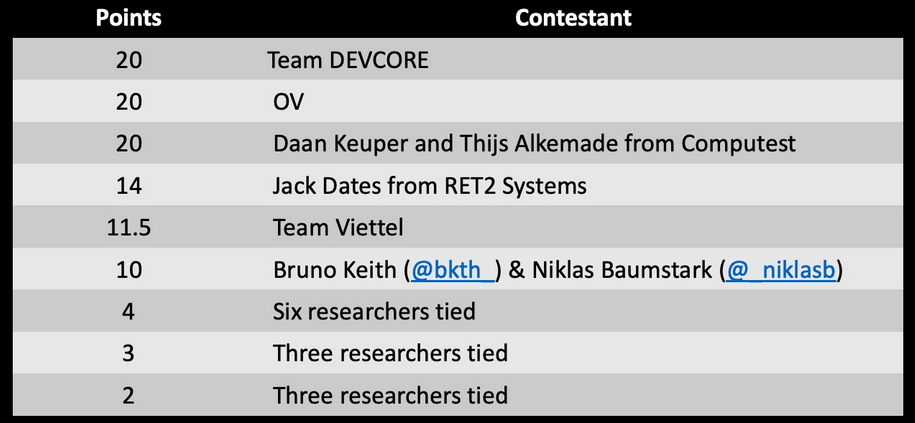
The competition ended with a tie between Team DEVCORE, OV, and Computest's Daan Keuper and Thijs Alkemade, each of them earning $200,000 and 20 Master of Pwn points.
$600,000 earned for three successful attempts
Team DEVCORE achieved remote code execution on a Microsoft Exchange server by chaining together an authentication bypass and a local privilege escalation on the first day of Pwn2Own 2021.
The security researcher known as OV online demoed code execution on a machine running Microsoft Teams by combining two separate security bugs.
Last but not least, on the second day, Computest's Daan Keuper and Thijs Alkemade gained code execution by hacking the Zoom Messenger using a zero-click exploit chain combining three different bugs, a feat considered by many the highlight of Pwn2Own 2021.
The contestants also hacked Microsoft's Windows 10 operating system four times during the competition to escalate to SYSTEM privileges from a normal user on fully patched machines and demoed an exploit for a bug that Microsoft was already aware of.
They also gained root privileges on fully patched Ubuntu Desktop machines twice and demonstrated a third exploit that abused a bug already known by the vendor.
After the vulnerabilities are exploited and reported during Pwn2Own, vendors are given 90 days to develop and release security fixes until Zero Day Initiative publicly discloses them.
You can watch recordings of all three Pwn2Own 2021 contest days below.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now