
A new trend in phishing attacks emerged in December 2021, with threat actors abusing the commenting feature of Google Docs to send out emails that appear trustworthy.
Google Docs is used by many employees working or collaborating remotely, so most recipients of these emails are familiar with these notifications.
Since Google itself is being "tricked" into sending out these emails, the chances of email security tools tagging them as potentially risky are practically zero.
The trick has actually been under limited exploitation since October last year, and while Google has attempted to mitigate the issue, they haven't fully closed the vulnerability yet.
This recent campaign is blowing up in proportions and is being monitored actively by threat analysts at Avanan, who shared their report with Bleeping Computer prior to publication.
How the attack works
Hackers use their Google account to create a Google Document and then comment it to mention the target with an @.
Google then sends a notification email to the target's inbox, informing them that another user has commented on a document and mentioned them.
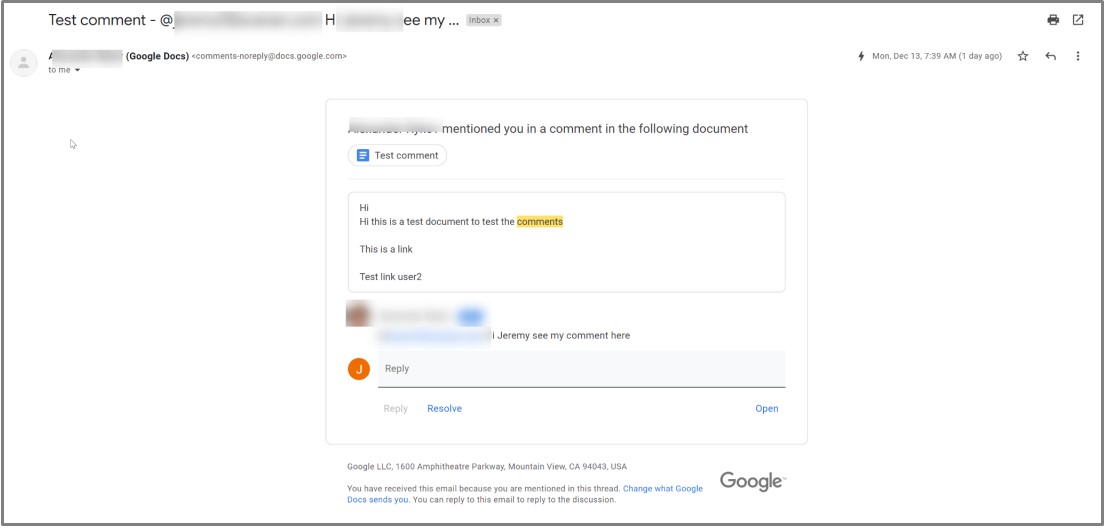
Source: Avanan
The comment on the email can carry malicious links that lead to malware dropping web pages or phishing sites, so there are clearly no checking/filtering mechanisms in place.
Secondly, the threat actor's email isn't shown in the notification, and the recipient only sees a name. This makes impersonation very easy, and simultaneously raises the chances of success for the actors.
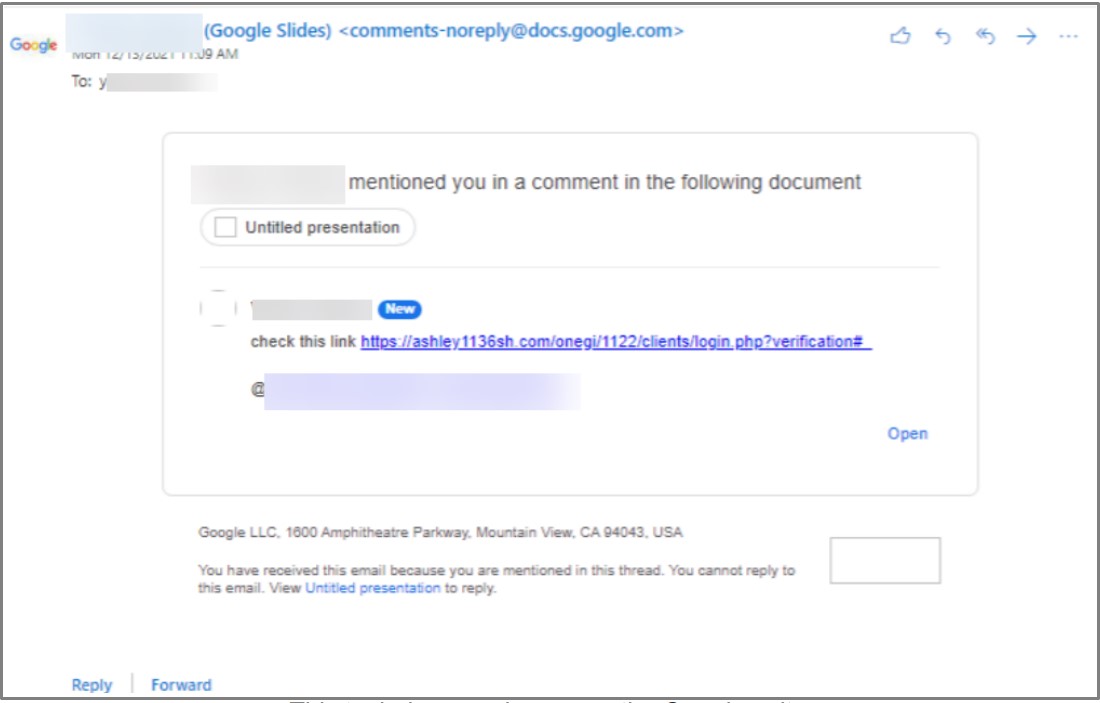
Source: Avanan
The same technique works on Google Slide comments too, and Avanan reports having seen actors leveraging it on various elements of the Google Workspace service.
To make things worse, attackers don't have to share the document with their targets since mentioning them is enough to send malicious notifications.
Attacks in the wild and protection measures
According to Avanan, the threat actors behind these attacks appear to favor Outlook users, but the target demographic is not limited to them.
This ongoing spear-phishing campaign uses over 100 Google accounts and has already hit 500 inboxes across 30 organizations.
The only way to mitigate the risk of this and similar campaigns is to:
- Confirm that the sender email matches your colleague's (or claimed person)
- Avoid clicking on links that arrive via email and are embedded on comments
- Deploy additional security measures that apply stricter file-sharing rules on Google Workspace
- Use an internet security solution from a trustworthy vendor that features phishing URL protection



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now