
South Korean researchers have publicly disclosed an encryption flaw in the Rhysida ransomware encryptor, allowing the creation of a Windows decryptor to recover files for free.
Rhysida is a ransomware operation that launched in mid-2023 and is notorious for targeting healthcare organizations, disrupting their crucial operations, and selling sensitive patient records.
In November 2023, the FBI and CISA warned about the gang's opportunistic attacks against a broad spectrum of industry types, including healthcare, military, cultural, and energy organizations.
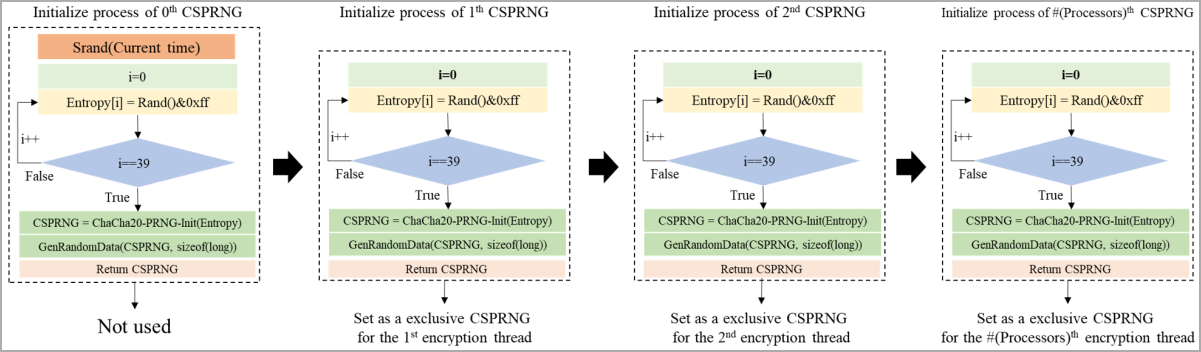
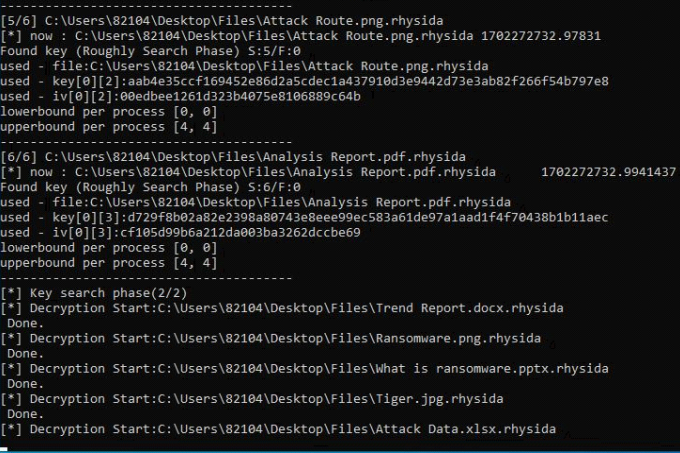
South Korean researchers, including employees of the Korean Internet & Security Agency (KISA), examining Rhysida found an implementation vulnerability in the ransomware's encryption scheme, specifically, the random number generator (CSPRNG) that helps generate the unique private (encryption) key in each attack.
By exploiting the flaw, the analysts could recover the internal state of CSPRNG during the attack and use it to create a valid key to reverse the data encryption.
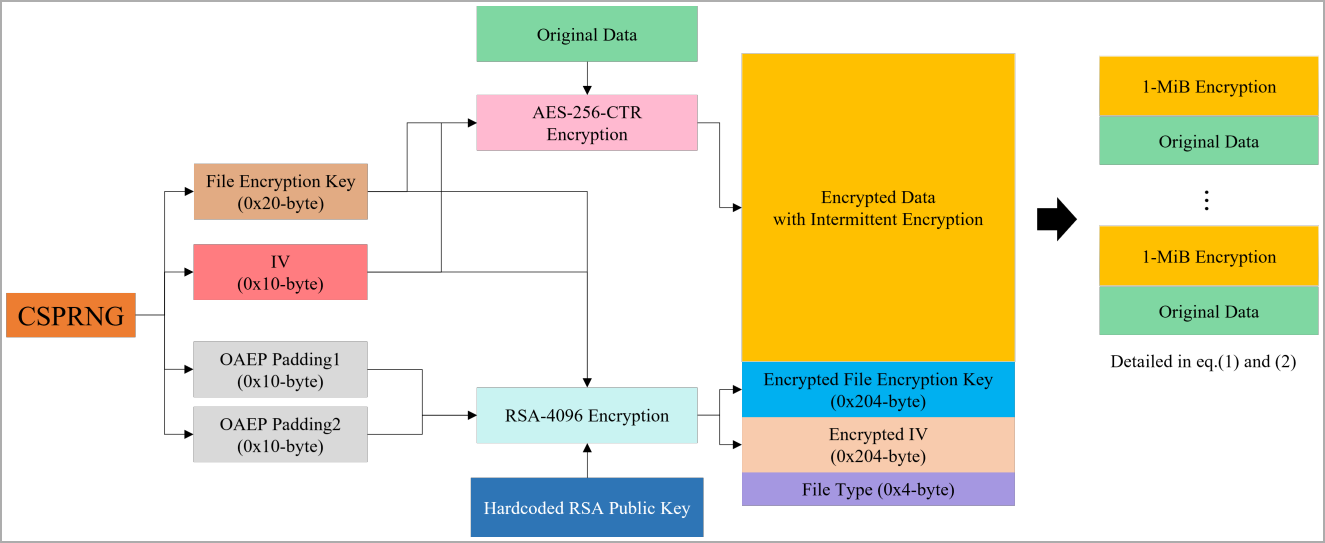
Rhysida's use of intermittent encryption, a tactic of only encrypting parts of the files while leaving others in plaintext, was critical in shaping the decryption method, as the researchers had to understand the encryption pattern and apply the right key selectively to the affected file parts.
Predictable seed value
Rhysida's faulty value generation system relies on deriving the 32-bit seed value from the system's current time, which the researchers say limits the search space to a computationally viable scope.
Rhysida uses this value to generate the private encryption key and initialization vector but lacks other high-entropy data sources to ensure that the seed value is unpredictable, making it guessable by looking into logs or other data indicating the time of the infection.
Armed with this knowledge, the researchers developed a method that systematically regenerates the CSPRNG state by trying out different seed values within the expected range.
Once the correct value is found (by validating that it can decrypt data), all subsequent random numbers used by the ransomware to encrypt files can be easily predicted, so all locked data can be retrieved without requiring the actual private key.
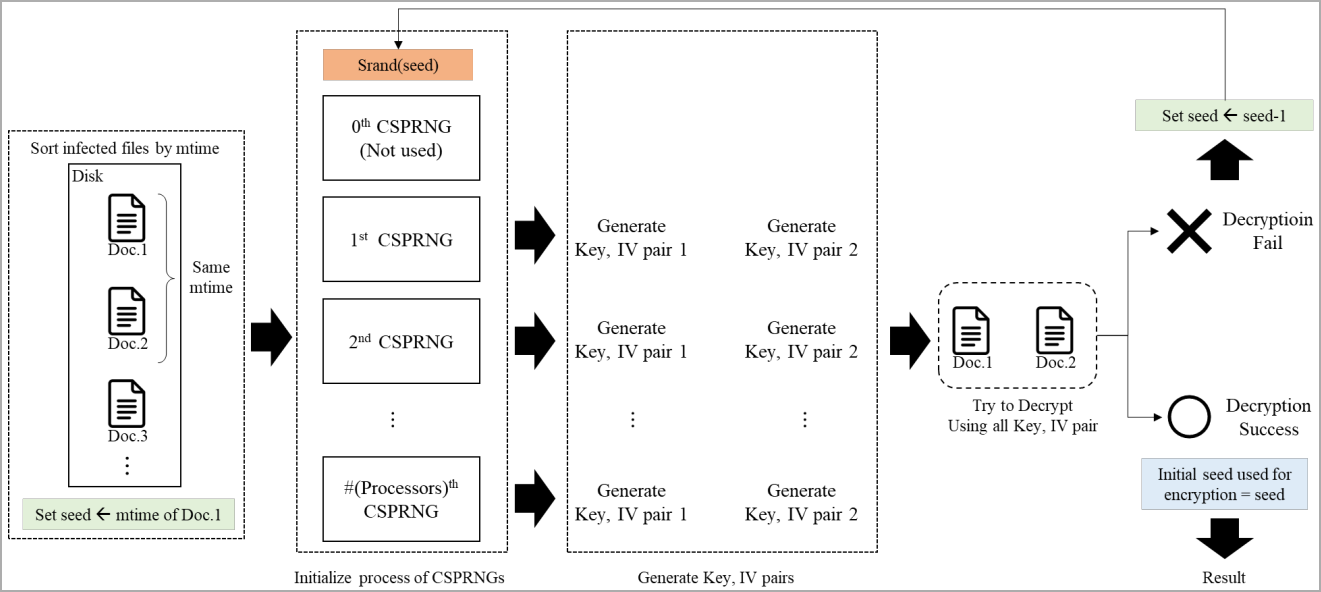
The decryption works by accurately regenerating the same encryption key and initial vector used during the original encryption process and then applying a counter-mode (CTR) encryption process to the encrypted segments of the files.
This method effectively reverses the encryption, restoring the original plaintext without needing the attacker's private key, exploiting the symmetric property of CTR mode where the encryption and decryption operations are identical.
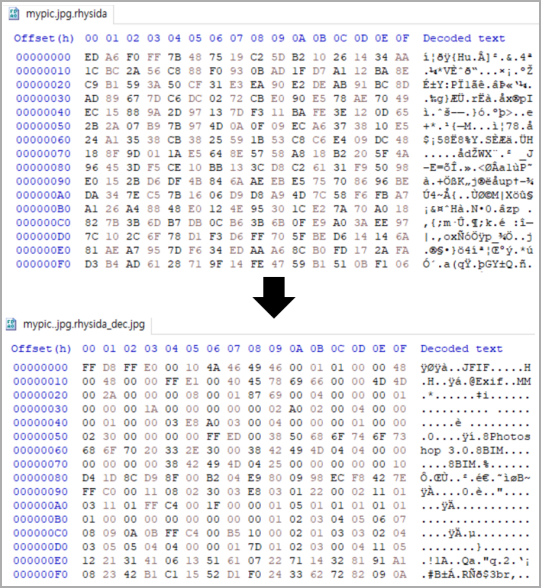
An automated decryption tool for Windows is available on KISA's website along with a technical paper published last Friday, with usage instructions in Korean and English.
Victims of the Rhysida ransomware may use the tool to try to decrypt their files for free, but BleepingComputer cannot guarantee the tool's safety or effectiveness.
Ransomware expert Fabian Wosar told BleepingComputer that this decryptor only works for encrypted files by the Rhysida Windows encryptor and cannot decrypt files encrypted on VMware ESXi or via its PowerShell-based encryptor.
Flaw privately exploited for months
The Rhysida encryption flaw has been privately used for months by cybersecurity firms and governments worldwide since at least May 2023.
"There goes another one. They are obviously not the first one who found this vulnerability," explains Wosar in a thread on X
"This was independently found by at least three other parties, who chose to circulate it in private instead of seeking publication and alerting Rhysida about their problem."
"As to who those parties are: Avast found it in October last year, the French CERT authored and published a private paper about it in June, and I found the vulnerability in May last year."
Wosar told BleepingComputer that petabytes of data on hundreds of machines have been successfully decrypted using this flaw since he discovered it in May.
When BleepingComputer contacted the South Korean researchers to ask why the flaw was publicly disclosed, they shared the following statement.
As far as we know, many cyber security companies are disclosing decryption techniques on their blogs/githubs/etc. And this definitely helps to mitigate the damage. We developed the decryption tool in collaboration with KISA and decided to release the paper to effectively demonstrate it. We are publishing our detailed research in the hope that it will contribute to the resilience of ransomware victims.
However, now that the flaw is public, Wosar warns that the ransomware operation will likely fix the bug in days, making it impossible to recover files without paying a ransom demand.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now