
Google said today that it sent roughly 50,000 alerts of state-sponsored phishing or hacking attempts to customers during 2021, a considerable increase compared to the previous year.
"So far in 2021, we’ve sent over 50,000 warnings, a nearly 33% increase from this time in 2020," said Ajax Bash, a Google security engineer working with the company's Threat Analysis Group (TAG).
"On any given day, TAG is tracking more than 270 targeted or government-backed attacker groups from more than 50 countries. This means that there is typically more than one threat actor behind the warnings."
Google sends government-backed attack alerts when detecting phishing attempts, brute-force attacks, malware delivery attempts launched from infrastructure linked to known government-sponsored threat groups.
According to Bash, these warnings are intentionally delivered in large batches instead of real-time to ensure the threat actors can't figure out defense algorithms and strategies.
The company has been warning Google users of such attacks since 2012, an alert system redesigned in 2017 and revamped with added info on the potential attack vector as seen in recent alerts sent in September.
Russian and Iranian threat actors stand out
This year, the most notable campaigns targeting Google users were coordinated by the Russian-backed APT28 (aka Fancy Bear) hacking group linked to the GRU Russian military intelligence agency and APT35 (aka Charming Kitten), an Iranian threat actor active since at least 2014.
The first was behind a large-scale phishing campaign accounting for 86% of all state-backed activity alerts delivered in September, with Google warning 14,000 users that their accounts were directly targeted.
Shane Huntley, Director of Google's Threat Analysis Group, said these warnings are commonly sent to activists, journalists, government officials, or people working in national security structures because they're the ones targeted by government-backed entities.
All phishing emails sent in this massive Fancy Bear campaign were blocked by Gmail and didn't make it in the targets' inboxes, as they were automatically classified as spam.
APT35 also had a very active year, hijacking accounts, deploying malware, and coordinating espionage campaigns to collect confidential info for the Iranian government.
In early 2021, the Iranian hacking group used a compromised site affiliated with a UK university to target Gmail, Hotmail, and Yahoo users, asking them to log in using their credentials to attend a fake webinar.
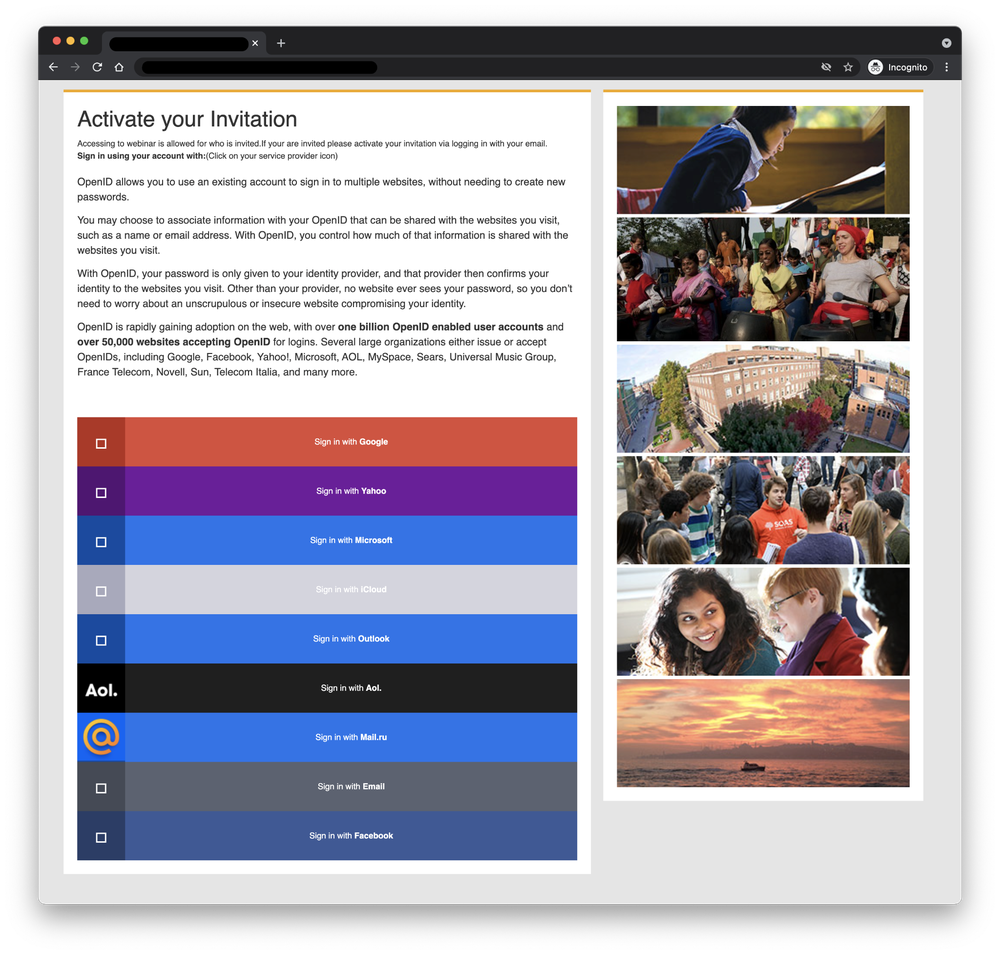
Google also observed them trying to deliver spyware onto potential victims' smartphones using malicious apps disguised as legitimate VPN software distributed via the Google Play Store and third-party platforms between May 2020 and July 2021.
They also impersonated Munich Security and Think-20 (T20) Italy conference officials in phishing campaigns using multiple redirects via Dropbox, Google Drive, App Scripts, Google Sites, and various Microsoft services pages to bypass detection.
"Thousands of these warnings are sent every month, even in cases where the corresponding attack is blocked. If you receive a warning it does not mean your account has been compromised, it means you have been identified as a target," Bash added.
"Users are encouraged to take these warnings seriously and consider enrolling in the Advanced Protection Program or enabling two-factor authentication if they haven't already."



Comments
Some-Other-Guy - 2 years ago
Update:
If you are using Windows 10 or 11, you have been identified as a target of a State Sponsored Attack!
Fact Checks Welcomed!
xrobwx71 - 2 years ago
"Update:
If you are using Windows 10 or 11, you have been identified as a target of a State Sponsored Attack!
Fact Checks Welcomed!"
Could this be why?
https://gs.statcounter.com/os-version-market-share/windows/desktop/worldwide