
Twitter has launched its 'Encrypted Direct Messages' feature allowing paid Twitter Blue subscribers to send end-to-end encrypted messages to other users on the platform.
End-to-end encryption (E2EE) uses private and public key pairs to encrypt information sent over the internet so that only the sender and the recipient can read it.
The private decryption key is only stored on the sender's device and is not shared with anyone else. However, the public encryption key is shared with others who want to send you encrypted data.
As the private decryption key is only stored on the local recipient's device and never stored anywhere else along the way, such as on the messaging app's servers, even if someone intercepts the message, they won't be able to read it without the decryption key.
End-to-end encrypted DMs on Twitter have been a sought-after and massively requested feature that was teased and retracted in 2018.
Last November, mobile researcher Jane Manchun Wong noticed that the source code of Twitter for Android hinted at work towards implementing an E2EE system, with Elon Musk all but confirming the suspicions.
Almost half a year later, Twitter officially announced today the availability of an encrypted messages feature on the latest version of the Twitter apps for iOS and Android and on the web platform.
Based on the details in the announcement, which mentions using a device-generated private key and a centrally-provided public key, Twitter has implemented an asymmetric encryption scheme.
"The public key is automatically registered when a user logs into Twitter on a new device or browser; the private key never leaves the device and therefore is never communicated to Twitter," explains a Twitter support page for the feature.
"In addition to the private-public key pairs, there is a per conversation key that is used to encrypt the content of messages."
Although no specific or technical details like the employed encryption algorithms have been disclosed, Twitter promised to open source its E2EE implementation and publish a detailed whitepaper later in 2023.
Only available to Twitter Blue subscribers
To the disappointment of many, this new security option will only be available to users who pay for a "verified" badge, with both conversation participants needing to be subscribed to Twitter Blue or affiliated with a verified organization for their messages to be encrypted.
The chat interface on eligible users now offers an 'Encrypted Direct Messages' toggle so they can easily switch modes at any time.
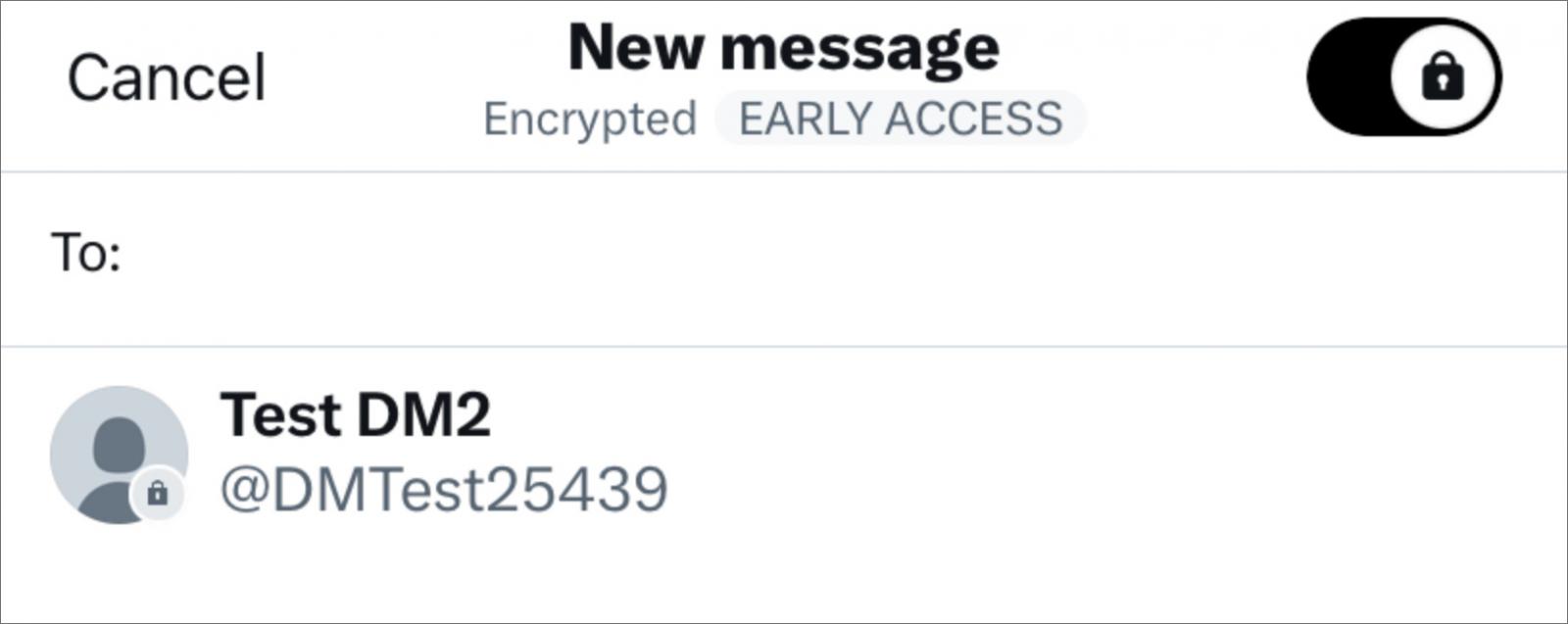
Source: Twitter
Users may resume existing conversations in E2EE mode by entering the previous message exchange, clicking on the information icon, and then selecting "Start an encrypted message."
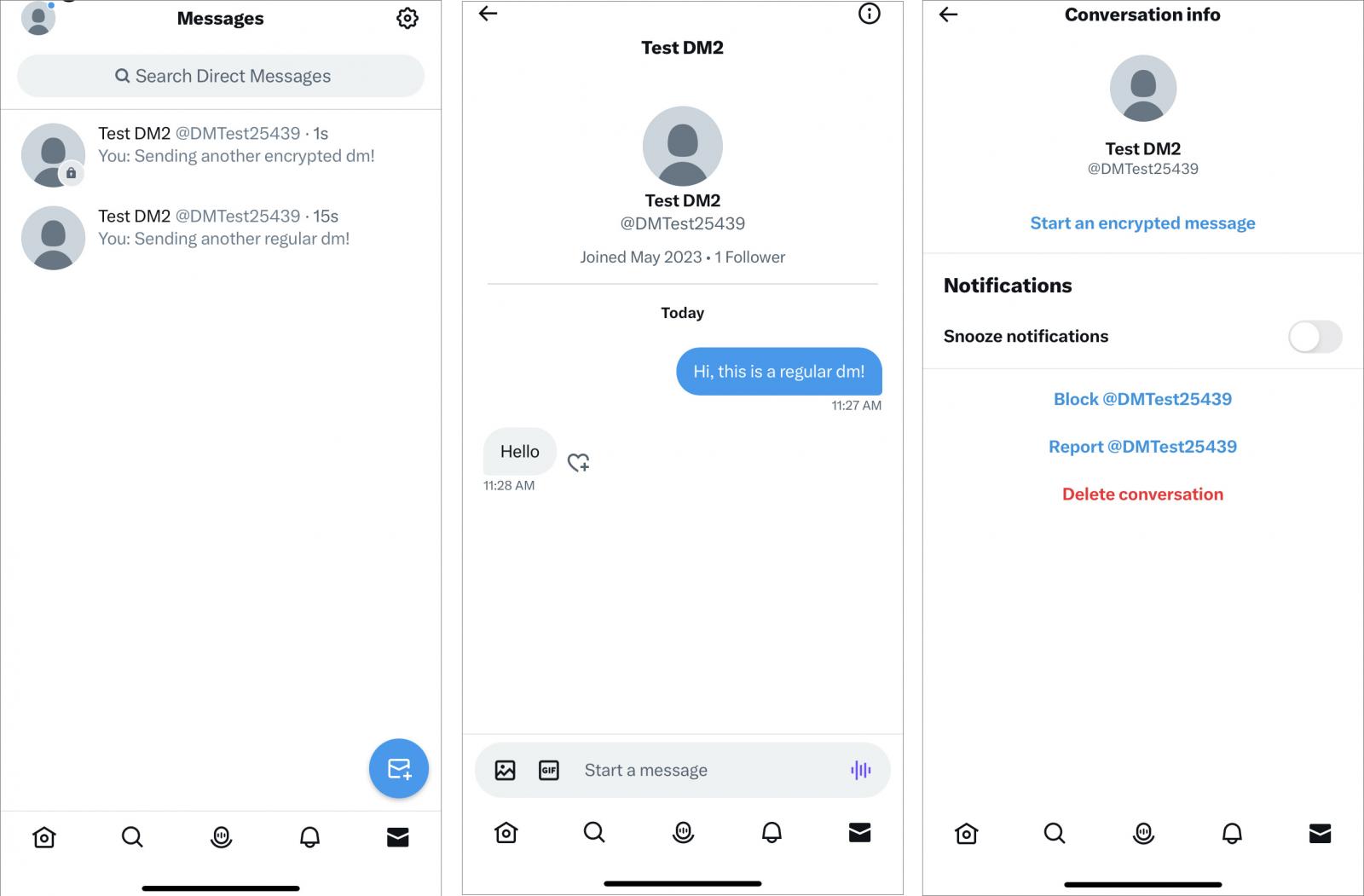
"Free" Twitter users will not have the option to use 'Encrypted Direct Messages,' defaulting to the standard unencrypted communications.
Apart from leaving non-paying users out, Twitter has also informed of some limitations, like not being able to send encrypted messages to groups, only supporting text and links (no media), not allowing new devices to join existing encrypted conversations, and only allowing a maximum of 10 registered devices per user.
Twitter also notes that the security of the private key, which remains on the device at all times, is crucial to protect the integrity of the new E2EE messaging system.
As, if an attacker steals that key, they may use it to decrypt all encrypted messages sent and received by the breached device.



Comments
johnlsenchak - 11 months ago
Twitter has become a huge joke after Musk took it over.
Sean133 - 11 months ago
It was a joke before Musk took over. At least he's trying to fix it.