
Google's Threat Analysis Group (TAG), whose primary goal is to defend Google users from state-sponsored attacks, said today that Russian-backed threat groups are still focusing their attacks on Ukrainian organizations.
In a report regarding recent cyber activity in Eastern Europe, Google TAG security engineer Billy Leonard revealed that hackers part of the Turla Russian APT group have also been spotted deploying their first Android malware.
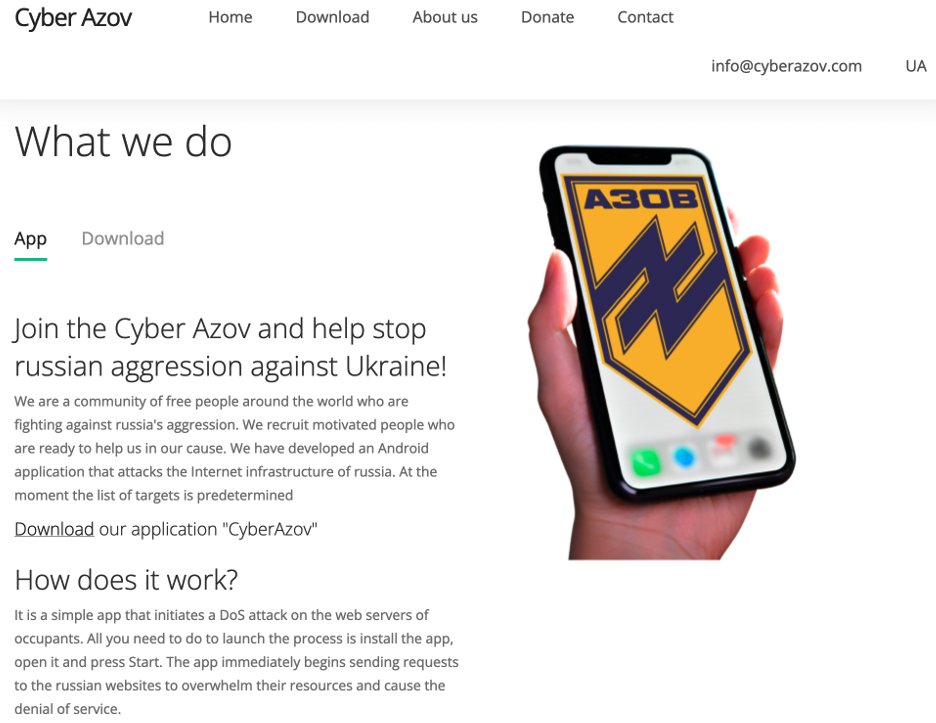
They camouflaged it as a DDoS attack tool and hosted it on cyberazov[.]com, a domain spoofing the Ukrainian Azov Regiment.
Google TAG's analysts believe Turla's operators used the StopWar Android app developed by pro-Ukrainian developers (hosted at stopwar[.]pro) when creating their own fake 'Cyber Azov' DDoS application.
"Join the Cyber Azov and help stop russian aggression against Ukraine! We are a community of free people around the world who are fighting against russia's aggression," the attackers prodded potential targets on the app's download page (still up when the article was published).
"We recruit motivated people who are ready to help us in our cause. We have developed an Android application that attacks the Internet infrastructure of russia."
"This is the first known instance of Turla distributing Android-related malware. The apps were not distributed through the Google Play Store, but hosted on a domain controlled by the actor and disseminated via links on third party messaging services," Leonard explained.
"The app is distributed under the guise of performing Denial of Service (DoS) attacks against a set of Russian websites. However, the 'DoS' consists only of a single GET request to the target website, not enough to be effective."
Leonard added that Google TAG believes there was no major impact on Android users so far and that the actual number of times the malicious Cyber Azov app was installed is minuscule.
Unorthodox cyberspies focused on high-profile targets
Turla has begun orchestrating information theft and espionage campaigns targeting networks and systems belonging to governments, embassies, and research facilities across over 100 countries since at least 1996.
Also tracked as Waterbug and Venomous Bear, this group has been previously linked to Russia's Federal Security Service (FSB).
They are the main suspects behind attacks targeting the Pentagon and NASA, the U.S. Central Command, Eastern European Ministries of Foreign Affairs, and the Finnish Foreign Ministry.
Turla was also linked to the breach of an undisclosed European government entity using a combo of remote administration trojans (RATs) and remote procedure call (RPC)-based backdoors.
This threat group is mainly known for its operators' unorthodox tactics, including using backdoor trojans with their own APIs and controlling malware using comments on Britney Spears' Instagram photos.
They've also hijacked the infrastructure and malware of Iranian APT OilRig and used them in their own campaigns to mislead and trick defenders into attributing their attacks to Iranian state hackers.
More recently, this Russian hacking group has used backdoors and remote access trojans in attacks targeting EU governments and embassies.
Google TAG also said in May that it observed the Turla hackers pushing credential phishing emails in attacks against Ukrainian defense and cybersecurity organizations.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now