
The Auckland Transport (AT) transportation authority in New Zealand is dealing with a widespread outage caused by a cyber incident, impacting a wide range of customer services.
AT is the government-owned regional transportation authority in the Auckland region, responsible for public transport through ferries, busses, and trains and for designing and building roads and other infrastructure.
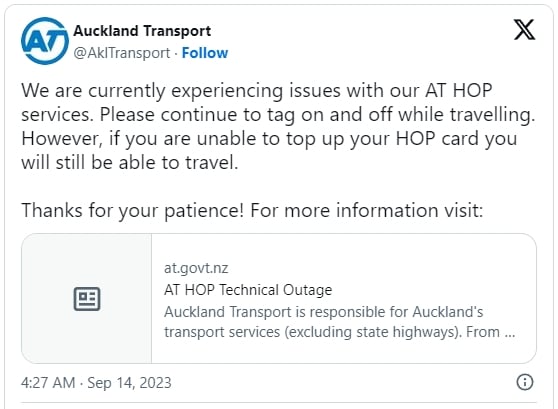
The company has announced today that it's experiencing issues with its HOP services (integrated ticketing and fares system) as a cyber incident has impacted parts of its network.
According to the latest update published earlier today, the following AT services have been impacted as a result of the attack:
- Online top-ups, as well as other AT HOP services using MyAT HOP on the AT website.
- Existing auto top-ups work, but there's a delay in the payment processing.
- Ticket and top-up machines are only accepting cash payments.
- Transactions using Eftpos/credit cards are unavailable. Some machines may not be working.
- AT customer service centers will have limited functionality and may only be able to accept cash payments.
- HOP retailers cannot top up HOP cards or process other AT HOP services like loading concessions.
In a statement given to local media outlet NZ Herald, a spokesperson for AT stated that they have indications they were targeted by ransomware but noted that investigations are still ongoing.
The same source stated that there will be leniency for passengers with empty HOP cards, and traveling using AT's busses, ferries, and trains should continue unaffected.
AT's website and HOP services might return to normal operations early next week, so patience is recommended as the organization gradually restores the affected systems.
Given that ransomware attacks typically also involve data exfiltration to be used in double-extortion, there's concern that AT customers might have had their sensitive details exposed.
Regarding this scenario, AT mentions, "At this point in time, we believe the incident is isolated to one part of our system and that no personal or financial data has been accessed."
No major ransomware groups have yet assumed responsibility for the attack on AT's systems.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now