
Multiple information-stealing malware families are abusing an undocumented Google OAuth endpoint named "MultiLogin" to restore expired authentication cookies and log into users' accounts, even if an account's password was reset.
Session cookies are a special type of browser cookie that contains authentication information, allowing a person to automatically log in to websites and services without entering their credentials.
These types of cookies are meant to have a limited lifespan, so they cannot be used indefinitely by threat actors to log into accounts if they are stolen.
In late November 2023, BleepingComputer reported on two information-stealers, namely Lumma and Rhadamanthys, who claimed they could restore expired Google authentication cookies stolen in attacks.
These cookies would allow the cybercriminals to gain unauthorized access to Google accounts even after the legitimate owners have logged out, reset their passwords, or their session has expired.
BleepingComputer has contacted Google multiple times over a month with questions about these claims and how they plan to mitigate the issue, but we never received a response.
Exploiting Google OAuth endpoint
A report published today by CloudSEK researchers sheds more light on how this zero-day exploit works and paints a dire picture regarding the scale of its exploitation.
The exploit was first revealed by a threat actor named PRISMA on October 20, 2023, who posted on Telegram that they discovered a way to restore expired Google authentication cookies.
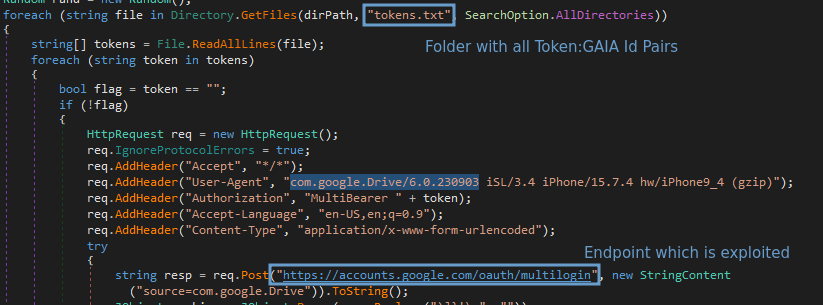
After reverse engineering the exploit, CloudSEK discovered it uses an undocumented Google OAuth endpoint named "MultiLogin," which is intended for synchronizing accounts across different Google services by accepting a vector of account IDs and auth-login tokens.
"This request is used to set chrome accounts in browser in the Google authentication cookies for several google websites (e.g. youtube)," explains a description of the API endpoint in the Google Chrome source code.
"This request is part of Gaia Auth API, and is triggered whenever accounts in cookies are not consistent with accounts in browser," a variable in the source code further explains.
CloudSEK says that information-stealing malware abusing this endpoint extracts tokens and account IDs of Chrome profiles logged into a Google account. This stolen information contains two crucial pieces of data: service (GAIA ID) and encrypted_token.
The encrypted tokens are decrypted using an encryption stored in Chrome's 'Local State' file. This same encryption key is also used to decrypt saved passwords in the browser.
Using the stolen token:GAIA pairs with the MultiLogin endpoint, the threat actors can regenerate expired Google Service cookies and maintain persistent access on compromised accounts.
Source: CloudSEK
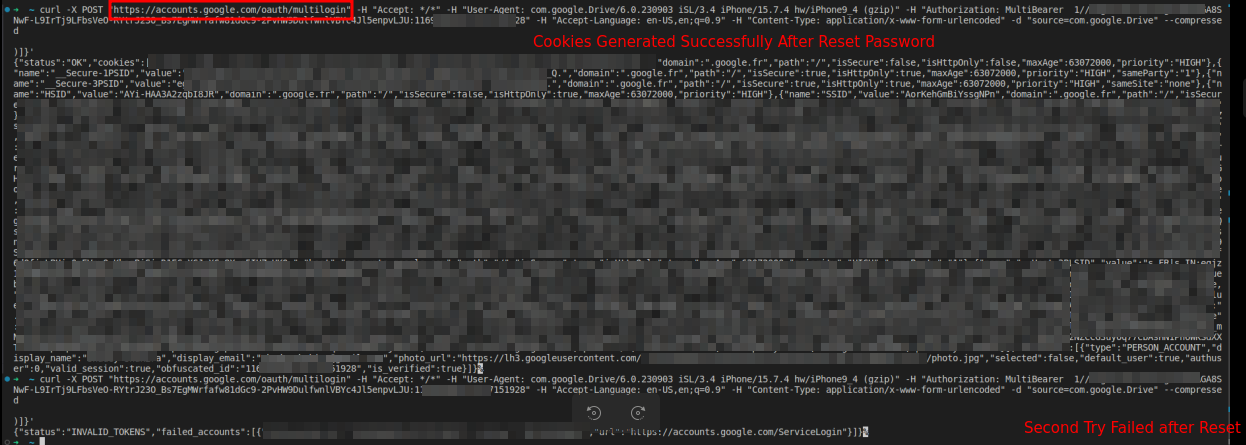
In a discussion with CloudSek researcher Pavan Karthick, BleepingComputer was told they reverse-engineered the exploit and were able to use it to regenerate expired Google authentication cookies, as shown below.
Source: CloudSEK
However, Karthick explained that the authentication cookie can only be regenerated once if a user resets their Google password. Otherwise, it can be regenerated multiple times, providing persistent access to the account.
To protect your account from this attack, Karthick says you must first logout of your Google account, change your password, and then log back into the account.
"This will ensure that the key is revoked and password safe," tweeted Karthick
Malware devs rush to add exploit
Lumma stealer first adopted the exploit on November 14, whose developers applied blackboxing techniques such as encrypting the token:GAIA pair with private keys to hide the mechanism from competitors and prevent the replication of the feature.
Still, others were able to copy the feature or incorporate PRISMA's exploit into their stealers, with Rhadamanthys being the first to follow on November 17.
Since then, numerous other information stealers have adopted the exploit, including Stealc on December 1, Medusa on December 11, RisePro on December 12, and Whitesnake on December 26.
So, at least six info-stealers currently claim the ability to regenerate Google cookies using this API endpoint.
Threat intelligence firm Hudson Rock has also published the following video on YouTube, where a cybercriminal demonstrates how the cookie restoration exploit works.
A subsequent release by Lumma updated the exploit to counteract Google's mitigations, suggesting that the tech giant knows about the actively exploited zero-day flaw.
Specifically, Lumma turned to using SOCKS proxies to evade Google's abuse detection measures and implemented encrypted communication between the malware and the MultiLogin endpoint.
However, since Google hasn't confirmed the abuse of the MultiLogin endpoint, the status of the exploitation and its mitigation efforts remain unclear at this time.
Update 1/3 - A Google spokesperson has sent BleepingComputer the following statement regarding the above:
Google is aware of recent reports of a malware family stealing session tokens. Attacks involving malware that steal cookies and tokens are not new; we routinely upgrade our defenses against such techniques and to secure users who fall victim to malware. In this instance, Google has taken action to secure any compromised accounts detected.
However, it’s important to note a misconception in reports that suggests stolen tokens and cookies cannot be revoked by the user. This is incorrect, as stolen sessions can be invalidated by simply signing out of the affected browser, or remotely revoked via the user's devices page. We will continue to monitor the situation and provide updates as needed.
In the meantime, users should continually take steps to remove any malware from their computer, and we recommend turning on Enhanced Safe Browsing in Chrome to protect against phishing and malware downloads.



Comments
e11i0t - 4 months ago
How can you save yourself if you are compromised you might ask ? Forgot to put this in original report you can find it here as well as in original report
Interim Remediation Steps:
While we await a comprehensive solution from Google, users can take immediate action to safeguard against this exploit. If you suspect your account may have been compromised, or as a general precaution, sign out of all browser profiles to invalidate the current session tokens. Following this, reset your password and sign back in to generate new tokens. This is especially crucial for users whose tokens and GAIA IDs might have been exfiltrated. Resetting your password effectively disrupts unauthorized access by invalidating the old tokens which the infostealers rely on, thus providing a crucial barrier to the continuation of their exploit.
Dill2046 - 4 months ago
Somehow, the remediation steps described don't correspond with the description above that said this exploit can persist across password reset, at least once. More details and reference, please.
WhiteGandalf - 4 months ago
What i ask myself after reading this: Why the hack do they bother to establish that two-factor-authentication at all - in the first place?!
If they build in ways to circumvent the latter, and thus having users forced to enthrall themselves with the sophisticated implications of account stealing, thus climbing to a level where things like to-factor-authentication are completely useless BY DEFINITION OF THE ENFORCED LEVEL OF COMPETENCE of their users?!
If a user is intelligent enough to grasp the implications of this threat, there is no need at all whatsoever to implement things like "two-factor authentication" with all their inconveniences in the first place.
In the status as it is, google could just require their users to have sophisticated insight into hacking technology - and counter measures -, because if they don't, they are helpless prey anyways.
I BET - and i will win - that whatever google will do in reaction to the disclosure of this threat WILL IN NO WAY change anything about this principle.
EITHER you are a user who has sophisticated insight into and IS aware of threats, and thus have no need whatsoever for over complicated login procedures, OR you are a user who has nothing of that and is left standing in the rain with however complicated login procedures get implemented.
mobileMcPhoneFace - 3 months ago
In my opinion, it is well worth the effort to enroll in the Google Advanced Protection Program (https://landing.google.com/advancedprotection/) for an added layer of security.
It requires purchasing one or two (if you want a backup) FIDO compliant hardware security keys.
Dill2046 - 3 months ago
Doesn't look like that would prevent this problem, though. It's a malware that steals OAuth token, bypassing both the password/2FA protections.