
An exposed Trello API allows linking private email addresses with Trello accounts, enabling the creation of millions of data profiles containing both public and private information.
Trello is an online project management tool owned by Atlassian that is commonly used by businesses to organize data and tasks into boards, cards, and lists.
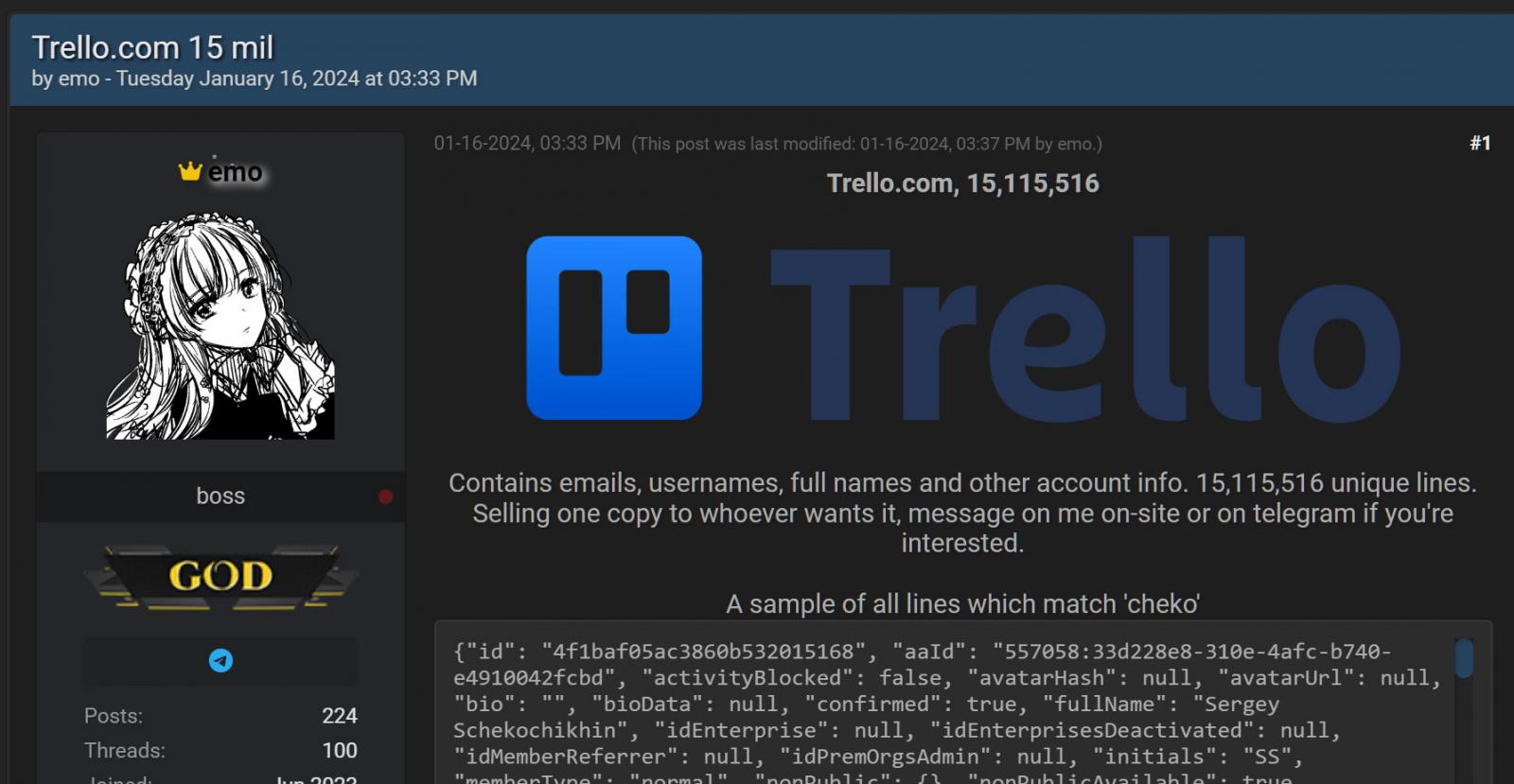
News of the Trello data leak came last week when a person using the alias 'emo' attempted to sell the data of 15,115,516 Trello members on a popular hacking forum.
"Contains emails, usernames, full names and other account info. 15,115,516 unique lines," reads the post on the hacking forum.
"Selling one copy to whoever wants it, message on me on-site or on telegram if you're interested."
Source: BleepingComputer
While almost all of the data in these profiles is public, the email addresses associated with the profiles are not.
When BleepingComputer contacted Trello about the data leak last week, we were told that it was not collected by unauthorized access to Trello's systems but by scraping public data.
"All evidence points to a threat actor testing a pre-existing list of email addresses against publicly available Trello user profiles," Atlassian, the owner of Trello, told BleepingComputer last week.
"We are conducting an exhaustive investigation and have not found any evidence of unauthorized access of Trello or user profiles.
However, it appears that there was more to the story about how the threat actor was able to confirm the email addresses.
Abusing an exposed API
In a conversation with emo, BleepingComputer learned that a publicly exposed API was used to associate email addresses with public Trello profiles.
Trello offers a REST API that allows developers to integrate the service into their applications. One of the API endpoints enables developers to query for public information about a profile based on users' Trello ID or username.
However, emo discovered that you can also query this API endpoint using an email address, and if there is an associated account, retrieve their public profile information.
Emo further said the API was publicly accessible, meaning it could be queried without logging into a Trello account or using an API authentication key.
The threat actor then built a list of 500 million email addresses and fed them into the API to determine if they were associated with a Trello account.
While BleepingComputer was told that Trello's API is rate-limited per IP address, the threat actor said they purchased proxy servers to rotate the connections to keep querying the API constantly.
The API has since been hardened to require authentication but is still available to anyone who creates a free account.
BleepingComputer contacted Trello to learn if they would be securing the API further to prevent abuse, and they shared the following statement:
"Enabled by the Trello REST API, Trello users have been enabled to invite members or guests to their public boards by email address. However, given the misuse of the API uncovered in this investigation, we’ve made a change to it so that unauthenticated users/services cannot request another user's public information by email. Authenticated users can still request information that is publicly available on another user's profile using this API. This change strikes a balance between preventing misuse of the API while keeping the ‘invite to a public board by email’ feature working for our users. We will continue to monitor the use of the API and take any necessary actions."
While scraping public data is not usually a concern, as the data was already public, email addresses associated with Trello accounts were only meant to be known by the account holder.
Therefore, linking private data, such as an email, to the public profile elevates the severity of the leak.
Furthermore, this information could be used in targeted phishing campaigns impersonating Trello to steal more sensitive information, such as passwords.
For those concerned, the Trello leak has been added to the Have I Been Pwned data breach notification service, allowing anyone to check if they are among the 15 million leaked email addresses.
A similar leak occurred in 2021 when threat actors exploited a Twitter API bug that allowed users to input email addresses and phone numbers and confirm whether they were associated with a Twitter ID.
The threat actors used another API to scrape the public Twitter data for the ID, combining the public data with associated private email addresses and phone numbers of Twitter users.
Twitter fixed this flaw in January 2022, but by then, it was too late, with multiple threat actors ultimately leaking the data of over 200 million Twitter profiles.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now