
Image: Midjourney
Microsoft says an initial access broker known for working with ransomware groups has recently switched to Microsoft Teams phishing attacks to breach corporate networks.
The financially motivated threat group behind this campaign is tracked as Storm-0324, a malicious actor known to have deployed Sage and GandCrab ransomware in the past.
Storm-0324 has also provided the notorious FIN7 cybercrime gang access to corporate networks after compromising them using JSSLoader, Gozi, and Nymaim.
FIN7 (aka Sangria Tempest and ELBRUS) was seen deploying Clop ransomware on victims' networks. It was also previously linked to Maze and REvil ransomware before the now-defunct BlackMatter and DarkSide ransomware-as-a-service (Raas) operations.
"In July 2023, Storm-0324 began using phishing lures sent over Teams with malicious links leading to a malicious SharePoint-hosted file," Microsoft said on Tuesday.
"For this activity, Storm-0324 most likely relies on a publicly available tool called TeamsPhisher."
This open-source tool enables attackers to bypass restrictions for incoming files from external tenants and send phishing attachments to Teams users.
It does this by exploiting a security issue in Microsoft Teams discovered by Jumpsec security researchers that Microsoft refused to address in July after saying that the flaw did "not meet the bar for immediate servicing."
Nevertheless, the issue was also exploited by APT29, the Russian Foreign Intelligence Service (SVR) hacking division, in attacks against dozens of organizations, including government agencies worldwide.
While Microsoft did not provide details on the end goal of Storm-0324's attacks this time around, APT29's attacks aimed to steal the targets' credentials after tricking them into approving multifactor authentication (MFA) prompts.
Today, the company said that it has since been working to put a stop to these attacks and protect Teams customers.
"Microsoft takes these phishing campaigns very seriously and has rolled out several improvements to better defend against these threats," Microsoft said.
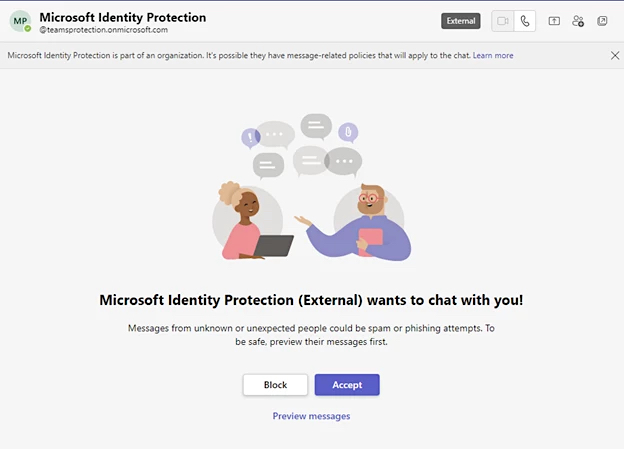
According to Redmond, threat actors using these Teams phishing tactics are now recognized as "EXTERNAL" users when external access is enabled within an organization's settings.
"We have also rolled out enhancements to the Accept/Block experience in one-on-one chats within Teams, to emphasize the externality of a user and their email address so Teams users can better exercise caution by not interacting with unknown or malicious senders," Microsoft said.
"We rolled out new restrictions on the creation of domains within tenants and improved notifications to tenant admins when new domains are created within their tenant."
After detecting Storm-0324's Teams phishing attacks, Microsoft suspended all tenants and accounts they used in the campaign.
.jpg)

Comments
RichieSanchez - 7 months ago
Microsoft, PLEASE allow Admins to block malicious domains at an Org level for Microsoft Teams, instead of asking users to block suspicious msgs per message attempt. There is currently no way to proactively block known bad actor domains and sender addresses from Teams. There is only the optiom to make the O365 Tenant private and block all external domains, then wjitelist trusted external domains. This might be ok for small businesses but not sustainable in enterprise businesses.