
Update: Title and content updated to clarify this is MiTM phishing attack conducted using a Flipper Zero but it could be performed by other devices.
Researchers demonstrated how they could conduct a Man-in-the-Middle (MiTM) phishing attack to compromise Tesla accounts, unlocking cars, and starting them. The attack works on the latest Tesla app, version 4.30.6, and Tesla software version 11.1 2024.2.7.
As part of this attack, security researchers Talal Haj Bakry and Tommy Mysk register a new 'Phone key' that could be used to access the Tesla.
The researchers reported their findings to Tesla saying that linking a car to a new phone lacks proper authentication security. However, the car maker determined the report to be out of scope.
While the researchers performed this phishing attack using a Flipper Zero, it could easily be done with other devices, such as a computer, a Raspberry Pi, or Android phones.
Phishing attack
An attacker at a Tesla supercharger station could deploy a WiFi network called "Tesla Guest," an SSID that is commonly found at Tesla service centers and car owners are familiar with it.
Mysk used a Flipper Zero to broadcast the WiFi network but notes that the same can be accomplished using a Raspberry Pi or other devices that come with WiFi hotspot capabilities.
Once the victim connects to the spoofed network, they are served a fake Tesla login page asking to log in using their Tesla account credentials. Whatever the victim enters on the phishing page, the attacker can see on the Flipper Zero in real time.
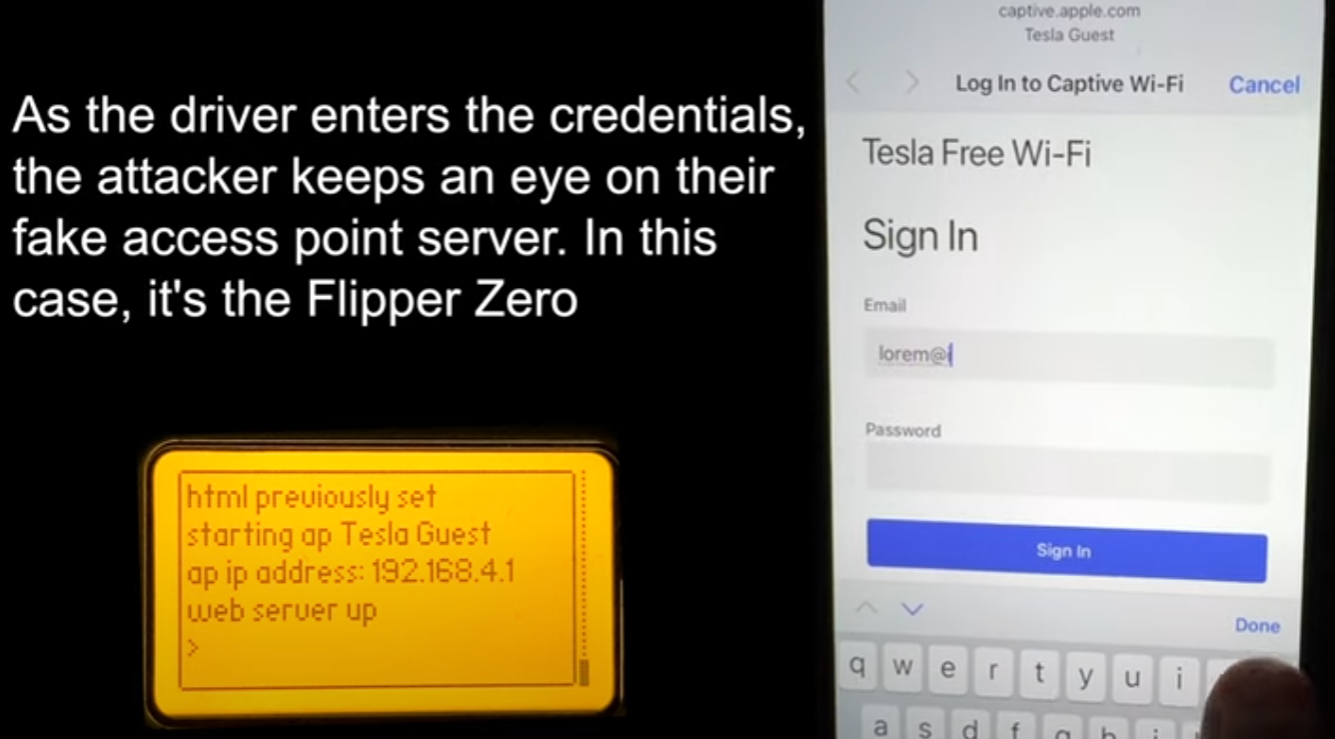
After entering the Tesla account credentials, the phishing page requests the one-time password for the account, to help the attacker bypass the two-factor authentication protection.
The attacker has to move before the OTP expires and log into the Tesla app using the stolen credentials. Once in the account, the threat actor can track the vehicle's location in real time.
Adding a new key
Access to the victim's Tesla account allows the attacker to add a new 'Phone Key.' For this, they must be in close proximity of the car, just a few meters away.
Phone Keys use Tesla's mobile app in conjunction with the car owner's smartphone to allow locking and unlocking the vehicle automatically, over a secure Bluetooth connection.
Tesla cars also use Card Keys, which are slim RFID cards that need to be placed on the center console's RFID reader to start the vehicle. Although more secure, Tesla treats them as a backup option if the Phone Key is unavailable or out of battery.
Mysk says that adding a new Phone Key through the app does not require the car to be unlocked or the smartphone to be inside the vehicle, which makes for significant security gap.
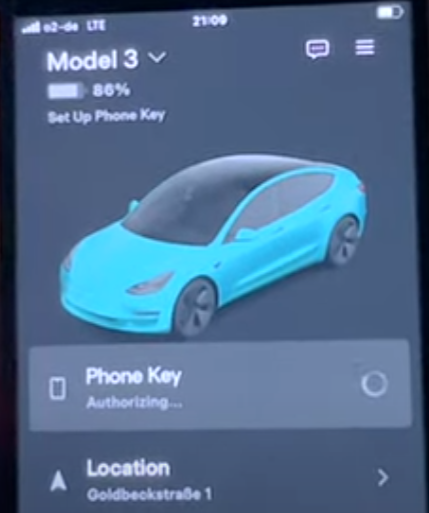
To make matters worse, once a new Phone Key is added, the Tesla owner does not receive a notification about the fact through the app, and no alert is shown on the car's touchscreen.
With the new Phone Key, the attacker can unlock the car and activate all its systems, allowing them to drive away as if they were the owner.
Mysk notes that the attack is successful on a Tesla Model 3. In the report to the car company, the researcher notes that the hijacked Tesla account must belong to the main driver and that the vehicle must already be linked to a Phone Key.
The researchers argue that requiring a physical Tesla Card Key when adding a new Phone Key would improve security by adding an authentication layer for the new phone.
"I was able to add a second phone key on a new iPhone without the Tesla app prompting me to use a key card to authenticate the session on the new iPhone. I only signed in on the new iPhone with my username and password, and as soon as I granted the app access to the location services, it activated the phone key," Tommy Mysk and Talal Haj Bakry wrote in the report to Tesla.
The company replied by saying that its investigation determined that it was the intended behavior and that the Tesla Model 3 owner's manual does not state that a key card is needed to add a phone key.
BleepingComputer has contacted Tesla with questions on the above and whether they plan to issue an OTA update that introduces security measures to prevent these attacks, but we have not heard back yet.
.jpg)

Comments
TalkingSasquach - 1 month ago
This is such a misleading article this is EXACTLY why Flipper Zero is getting banned places. You can run an Evil Portal attack on virtually anything and that attack has been around FOREVER. Making an article that says Flipper Zero WiFi Attack can Steal Cars is absolutely ridiculous click-bait nonsense. I used to respect bleepingcomputer but after seeing this and other articles with the same misleading nonsense, you've changed my mind. The community deserves better. Do better.
h_b_s - 1 month ago
The research and the article are a direct response to the Flipper Zero maker claiming Zeros can't be used to steal cars. That is and always was provably false. They can be, along with screwing with any number of other mischief causing RF protocol attacks. Let's not lose sight that this is exactly what the Zero was intended to do: easily carrying out penetration testing and vulnerability testing. It's inevitable it would be put to nefarious uses, just like lock picks, hammers, screwdrivers, etc.
What the people trying to ban Zeros miss is that Zeros are just a tool. It won't stop people from screwing with or stealing cars because the basic vulnerabilities are there to be exploited by anyone with a laptop that has WIFI and BT capability along with a cheap SDR dongle and appropriate antenna. Fixing the problem with proper legislation is difficult and usually results in deep pocket litigation along with election year nastiness when overly powerful organizations like trade organizations and unions run libelous ads because they don't like you any more because a politician dared to do their job and cost them money. It's easier to blame the usual scapegoats like the mysterious and shadowy "hackers" because it's easier to hate what people don't understand than it is to educate oneself.
TalkingSasquach - 1 month ago
With the same justification, you could say that the Flipper can be used to break into anything buy using it to smash a window.
h_b_s - 1 month ago
Yup. And in some US states, the "thief's tools" laws are written to be just that vague. In practice, however, what a tool's primary everyday purpose is what matters. A hammer is just a hammer because its primary use is driving nails, not smashing windows. When you get to tools like lock picks, some states you can be arrested just for carrying them without a locksmith's state issued license because their primary everyday purpose IS to open locks you don't have a key for. Usually that means you're up to no good. Likewise, the primary use for a Flipper Zero is arguably illegal thanks to the notoriously vague wording on the US's CFAA and likely most state digital intrusion/vandalism laws. It's not inconceivable that a sufficiently politically motivated DA could go after you under existing thief's tools laws just for owning a Flipper Zero. They are designed to test the integrity of security systems that use RF elements, but unlike locksmiths, there's no licensing for "ethical hacking" as such, though a private investigator's license or a signed contract for penetration testing with local companies *might* suffice (don't hold your breath, there are cases where it hasn't). The only protection we really have in the US is a "norm" the DoJ won't prosecute good faith security research under the CFAA with certain caveats. There's no such legal protection either in US federal law and definitely not in most states for that. Anyone that pays attention will know that norms and other such statements aren't binding and can be ignored by anyone. Also the states can do as they wish so long as their actions aren't prevented under federal preemption statutes.
With a laptop and an SDR you can't really be reasonably prosecuted for owning thief's tools because that's not their primary use, but it's not out of the realm of possibility you could for a Flipper Zero. Obviously, the debate has raged for years with no real resolution over curiosity versus thief's tools issue. This is just more of that same debate. If you really want to do something useful however, I suggest making donations to the Electronic Frontier Foundation @ https://eff.org to fund their lobbying, outreach, and legal efforts (or the equivalent organization in your local jurisdiction).
electrolite - 1 month ago
Although I do not share the same level of annoyance as the OP he does have a valid point. The title of an article should encapsulate what the core issue is. Based on the title here, you get the impression that the Flipper Zero can hack Tesla cars. That is highly circumstantial. The real story is that Tesla cars at a Tesla SuperCharger station can be compromised by a MITM attack when connecting to the station's AP. The title should have encapsulated something along those lines because it is more precise. But this is a general trend in the publishing industry to use buzz words, fads or memes in the title just to grab attention. Using Flipper Zero is just a convenient device name because it has been in the news lately and does not deserve the attention it is getting.
Heck if we want to use click-bait titles, why not go with "Musk hacked by Mysk".
h_b_s - 1 month ago
It's not circumstantial. The Flipper Zero can mount MitM attacks with the proper code just like any laptop can so long as the vehicle uses frequencies that fall within the Flipper's device capabilities. That's what makes it convenient for RF environment awareness and vulnerability testing. I'm not arguing these things should be banned. I'm saying that what Flipper Zero's maker is saying, that they "can't" be used to open vehicles, is demonstrably untrue. The nuances matter, but most people ignore them like the OP. Binary is the absolultist's weapon. Strictly yes or no. The real world doesn't work in binary. It functions in analog shades of gray. Flippers can be programmed to enable unauthorized access in many cases because those "locks" aren't well designed. It would be more accurate to say it's a tool that allows security experts to quickly and conveniently test their environments for known problems before an adversary does it for them. Yet, like any tool, especially a versatile one like a Flipper Zero or HackerRF One (or any SDR transceiver in the proper frequency range), can be used for criminal activities. It will do no good to ban them because their functionality is easily duplicated.
But as you said, and I'm perhaps not being clear: yes, the real story is that Tesla's vehicles are still easily accessed with off-the-shelf tools as are the vehicles from many different car manufacturers, NOT that Flipper Zero can potentially be used to do so. Flippers are only a story because the manufacturer made a false claim they couldn't be used in this way.
TalkingSasquach - 1 month ago
Flipper can't really do MitM attacks because it can't transmit and receive simultaneously. It's a simple really bad Evil Portal honey pot. It's basically the worst way to accomplish this attack, since the portals are limited to about 2k characters and they look so non-convincing that almost no one should fall for it.
Lawrence Abrams - 1 month ago
We heard you and others loud and clear and agree our original title was misleading.
We updated the title and story yesterday to make it more clear that this attack is not confined/due to Flipper Zero and could be accomplished many other ways.
electrolite - 1 month ago
"The research and the article are a direct response to the Flipper Zero maker claiming Zeros can't be used to steal cars. "
Did you even watch the reasearcher's video? His concern was that the Tesla credentials can be siphoned at the stations. He mentioned using the Flipper. He never said he was out to prove the Flipper maker wrong, you just projected your stance on him. That comes across as disingenuous and I agree with the OP even more now. I had never heard of the Flipper before but articles like this are having a Streisand effect.
"Edit" The author updated the title to say "MITM" instead so I appreciate that.
DyingCrow - 1 month ago
The owner really has to make an effort to put themselves in this situation, why would this be a problem? Starting with "hmm, there's a free wi-fi here, lemme connect to it because...it's free"