
Malicious advertisements are now being injected into Microsoft's AI-powered Bing Chat responses, promoting fake download sites that distribute malware.
Bing Chat, powered by OpenAI's GPT-4 engine, was introduced by Microsoft in February 2023 to challenge Google's dominance in the search industry.
By offering users an interactive chat-based experience instead of the traditional search query and result format, Bing Chat aimed to make online searches more intuitive and user-friendly.
In March, Microsoft began injecting ads into Bing Chat conversations to generate revenue from this new platform.
However, incorporating ads into Bing Chat has opened the door to threat actors, who increasingly take out search advertisements to distribute malware.
Furthermore, conversing with AI-powered chat tools can instill unwarranted trust, potentially convincing users to click on ads, which isn't the case when skimming through impersonal search results.
This conversation-like interaction can imbue AI-provided URLs with a misplaced sense of authority and trustworthiness, so the existing problem of malvertizing in search platforms is amplified by the introduction of AI assistants.
The fact that these ads are labeled as promoted results when the user hovers over a link in Bing Chat conversations is likely too weak of a measure to mitigate the risk.
Imitating a popular IP scanner
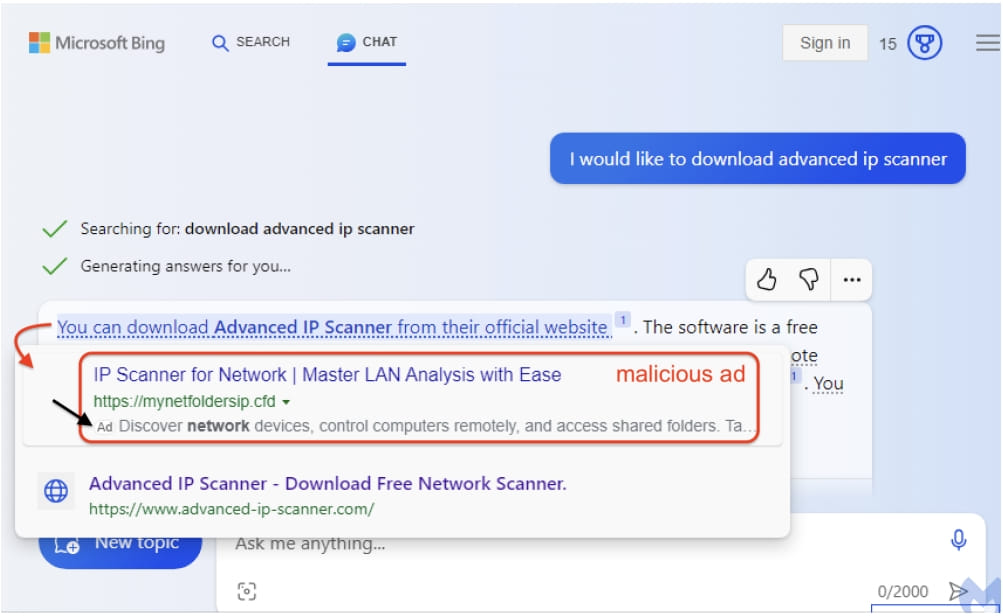
Malicious ads spotted by Malwarebytes are pretending to be download sites for the popular 'Advanced IP Scanner' utility, which has been previously used by RomCom RAT and Somnia ransomware operators.
The researchers found that when you asked Bing Chat how to download Advanced IP Scanner, it would display a link to download it in the chat.
However, when you hover over an underlined link in a chat, Bing Chat may show an advertisement first, followed by the legitimate download link. In this case, the sponsored link was a malvertisements pushing malware.
Source: Malwarebytes
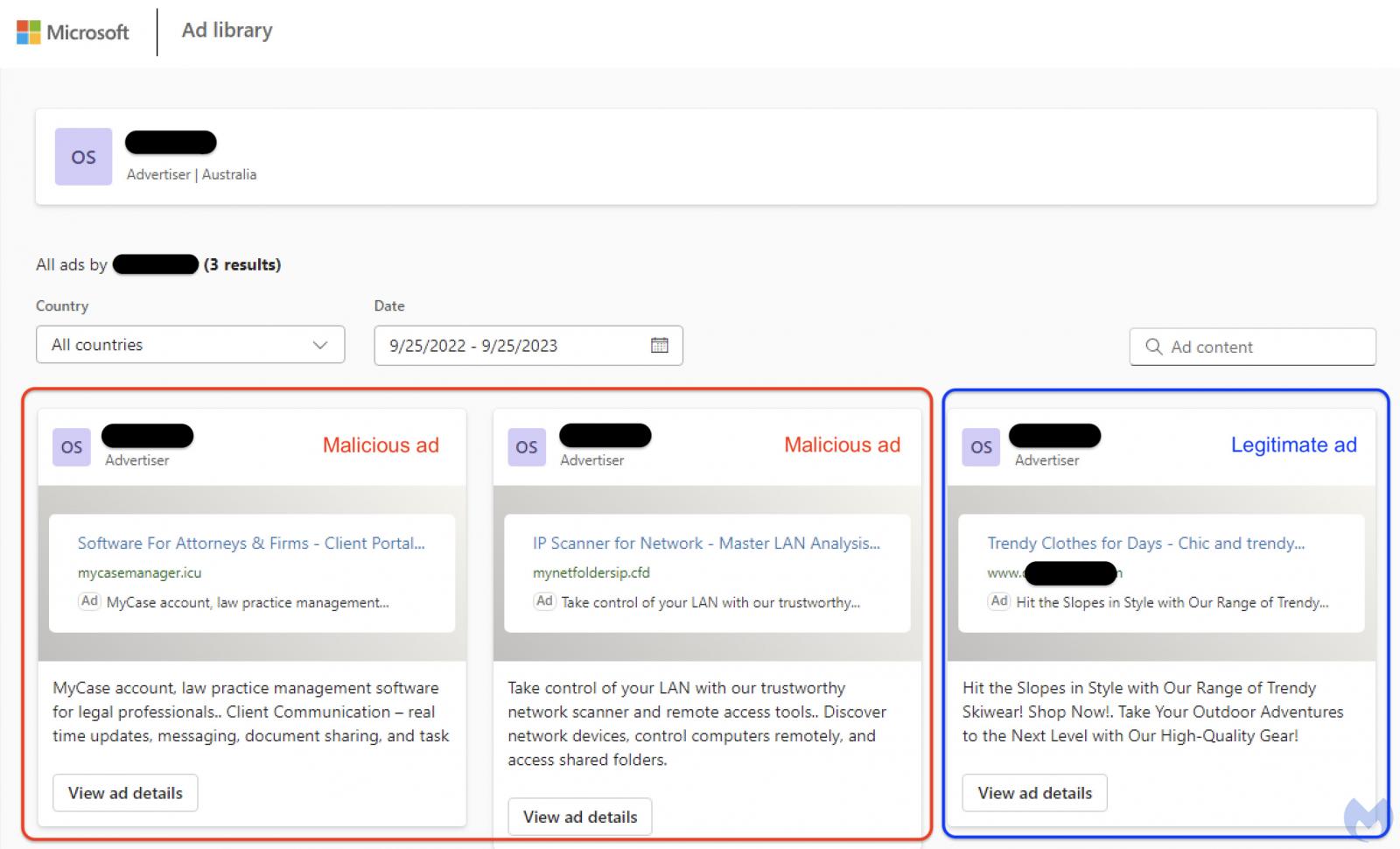
The malvertizing campaign was created by someone who hacked into the ad account of a legitimate Australian business to create two malicious ads targeting system admins (IP scanner) and lawyers (MyCase law manager).
Source: Malwarebytes
Clicking on the malicious ad for the IP scanner takes users to a website ('mynetfoldersip[.]cfd') that separates bots and crawlers from human victims by checking IP address, timezone, and various system indicators for sandbox/virtual machines.
The victims are then redirected to 'advenced-ip-scanner[.]com', a clone of Advanced IP Scanner that uses typosquatting (notice the e in advenced) to trick visitors.
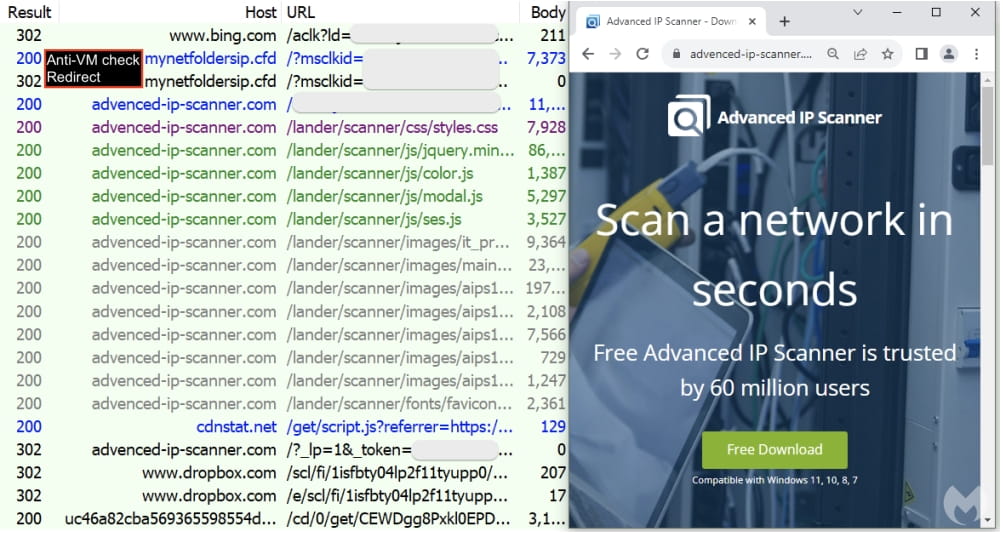
The downloaded MSI installer contains three files, one of which is a heavily obfuscated malicious script that connects to an external resource to retrieve the payload.
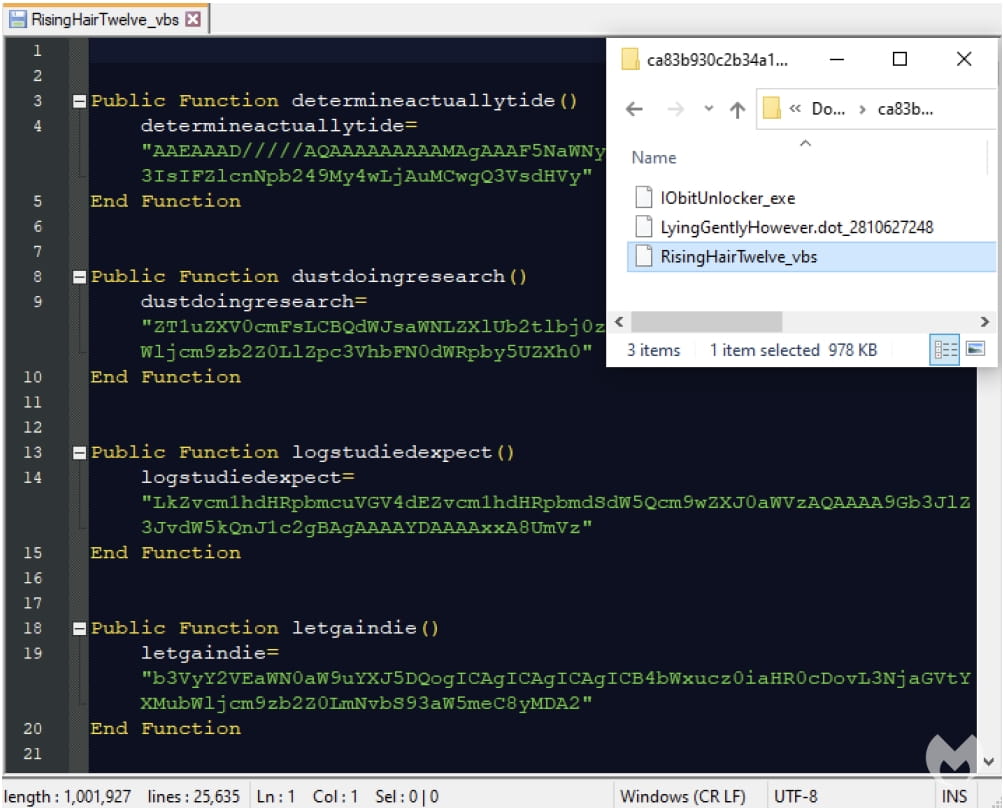
Unfortunately, Malwarebytes could not find the final payload for this malware campaign, so it is unclear what malware is ultimately being installed.
However, in similar campaigns, threat actors commonly distribute information-stealing malware or remote access trojans that allow them to breach other accounts or corporate networks.
The display of malvertising within Bing Chat conversations highlights the expanding frontier of cyber threats and makes it crucial for users to be wary of chatbot results and always double-check URLs before downloading anything.



Comments
ThomasMann - 7 months ago
"...Microsoft's AI-powered Bing Chat responses, ..."
Of course, what did you think AI will be used for? For YOUR advantage???
The more of all these idiotic digital toys you use, the more retarded you end up. And the less you will reamain aware enough to notice it....
NoneRain - 7 months ago
AI is a tool like any other. Use it to enhance your own skills and get results faster.
This 8-80 mentality usually comes from those who are ignorant about the tech they're talking about.
Dominique1 - 7 months ago
Google ads are dangerous! Microsoft ads are dangerous! I don't need an AI to tell me that GAFAM ads are dangerous. It should be pretty clear by now. Besides! Who click these ads anyway? LOL!!!
mikebutash - 7 months ago
Microsoft's lack of foresight linked to rampant malware distribution, say it isn't so.
No1gr8 - 7 months ago
MS had to invest $10 billion to get these ads :) What's the ROI on that? Maybe those infected will see Windows Defender ads, too.
Knight_of_BAAWA - 7 months ago
This is my shocked and surprised face.
Icepop33 - 7 months ago
This disco ball of complexified technology keeps growing more attack surfaces. I feel bad for security pros in the future. In the near term, their services will be in great demand, until people realize it's futile and start laughing in their faces when they mention the words "computer security". If only we instilled common sense and best practices into our youth, but we're going the other way and KISS and better standardization doesn't allow for all the bespoke dark patterns in software service implementation.