
The first seven months of 2023 have seen a continued rapid evolution of the cybercrime ecosystem. Ransomware data exfiltration attacks, stealer log distribution, and new exploits targeting organizations continue to substantially increase.
This article explores a key component of the cybercrime ecosystem, stealer logs, and their role in the broader cybercrime ecosystem.
What are Stealer Logs?
Infostealer malware has risen to prominence as one of the most significant vectors of cybercrime over the past three years.
Infostealers are a form of remote access trojan (RAT) that infects a victim computer, exfiltrates all of the credentials saved in the browser, as well as session cookies, while also stealing other sensitive data such as credit card information, cryptocurrency wallet data, and other information from the host.
Logs are then either used or distributed to other cybercriminals as a key initial vector that enables financial fraud, account takeover attacks, ransomware distribution, and data breaches against organizations.
Malware as a Service Vendors, Telegram, and the Cybercrime Supply Chain
Malware as a service (MaaS) vendors continually develop new variants of infostealer malware which are then sold in specialized Telegram channels. The most common variants we see today are RedLine, Vidar, and Raccoon.
MaaS vendors often package their malware in convenient monthly subscription packages that can be easily purchased for a set amount of cryptocurrency, and come complete with command and control (C2) infrastructure and a backend that enables seamless management of hundreds of thousands of stealer logs.
Threat actors then simply need to identify methods to distribute the malware to consumers.
Distribution typically takes a few forms, some of the most common of which are adding infostealer payloads to cracked software, phishing emails, malvertising, and advertising free video-game currency; infostealer malware is mostly distributed in a “spray and pray” fashion, very rarely being employed in targeted attacks.
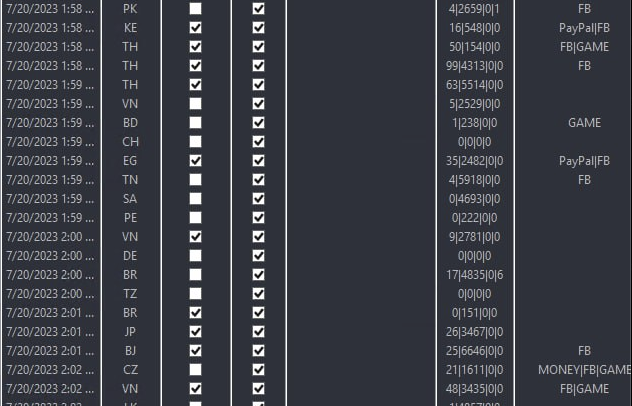
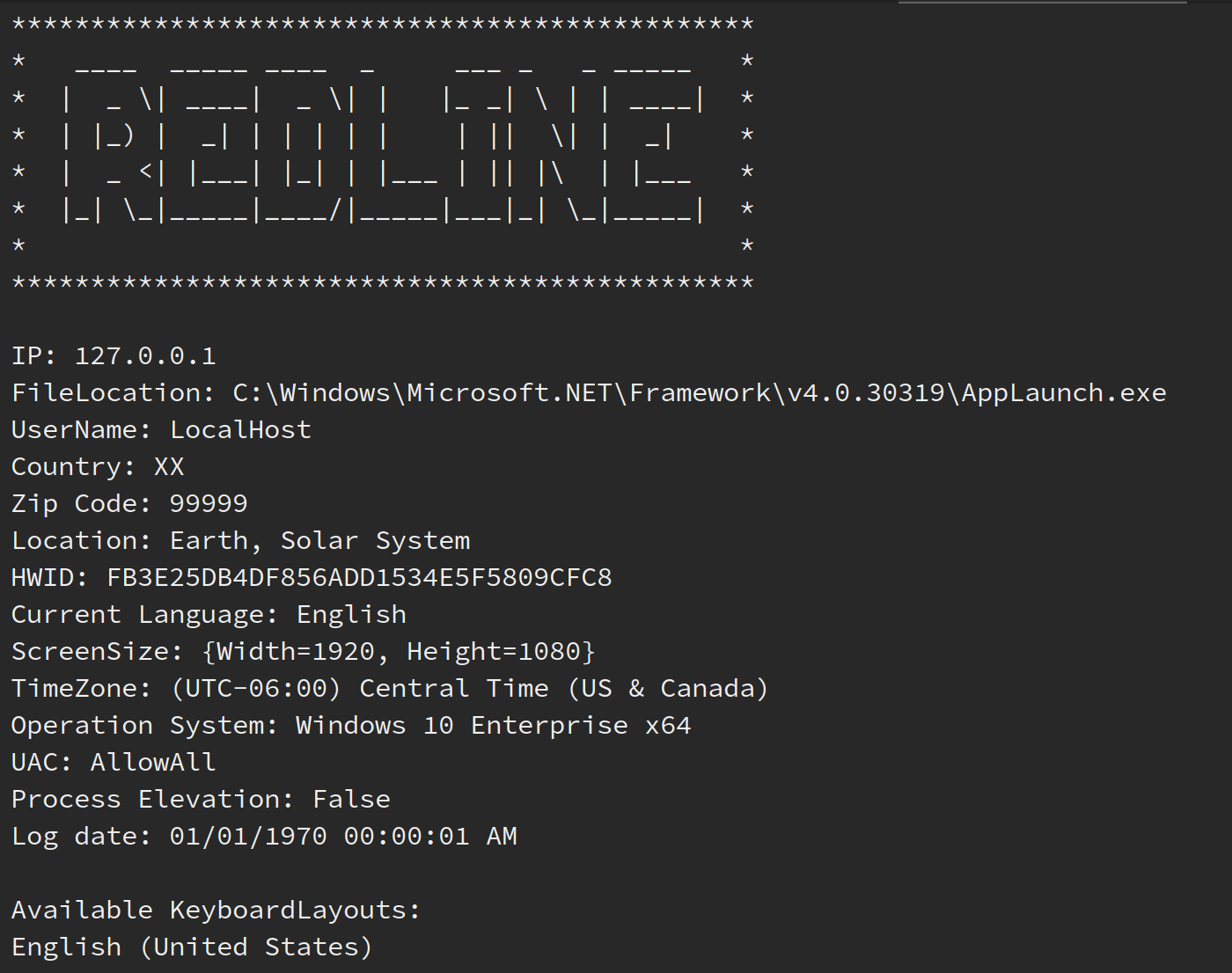
Once an infection takes place, data is exfiltrated to the malware’s backend infrastructure, in the form of “stealer logs”.
The screenshot on the left shows infrastructure related to a common infostealer variant. The columns display the infection date, country code, checkboxes to mark duplicates, counts of credentials, and finally an automatic parsing system to identify high-value credentials within the log.
Stealer Logs Distribution: Tor and Telegram Take Center Stage
Stealer logs used to be distributed almost exclusively on dark web online stores, through popular autoshops such as Genesis Market and Russian Market.
However, in recent years, there has been an increasing adoption of the messaging platform Telegram for everything related to cyber-crime, including stealer logs distribution; out of more than one million unique logs collected per month, we currently see more than 70% being distributed on Telegram channels.
Threat actor groups create channels, usually referred to as “clouds”, where they will sell access to freshly gathered stealer logs, for a subscription fee.
On top of selling access to their “private” channels, these groups will usually have a “public” channel, where they distribute what can be considered samples of what a potential buyer would get access to by purchasing a subscription to their “private” channels.
Every day, thousands of stealer logs are distributed across Telegram, spread across hundreds of channels.
Whilst most members of these channels are looking for an easy way to make a quick buck, such as by leveraging stolen cryptocurrency wallets, or access to bank accounts, other more advanced users will look at leveraging the illegitimate access stealer logs provide in order to disrupt corporate operations.
Stealer Logs, Access Brokers and Ransomware Affiliates
We have seen substantial evidence that initial access brokers (IAB), threat actors that operate on dark web forums and sell access to company networks and IT Infrastructure, use logs as a primary vector of initial access.
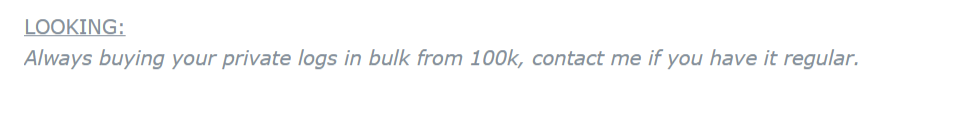
Once IABs have established a foothold in a company’s network, the access itself is then auctioned off on dark web forums.
Depending on the level of access provided, these auctions can be valuable to ransomware affiliates as an “easy” entry point for a ransomware attack.
How Stealer Logs Can Impact Consumers and Organizations
Stealer logs constitute a danger to consumer and organizations alike, with consumers (the victim of the infection) at risk of being victim of financial fraud or cryptocurrency theft, as well as unauthorized access to their accounts, but a surprising amount of stealer logs also provide some corporate access to various services.
A recent Flare analysis found more than 350,000 logs that contained credentials to commonly used corporate applications including single-sign on (SSO) portals, access to cloud environments, and other high-value applications.
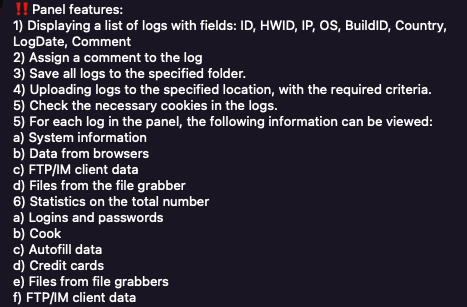
Stealer Log Detection & Remediation with Flare
Flare automates detection for corporate credentials across tens of millions of stealer logs, providing contextualized high-value alerting to security teams.
Flare’s SaaS platform automatically detects the leading threats that lead to ransomware attacks, data breaches, and other forms of cybercrime affecting organizations.
Sign up for a free trial to find out how Flare can seamlessly integrate high-value cybercrime intelligence into your security program in 30 minutes.
Sponsored and written by Flare.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now