
A threat actor announced on a cybercrime forum that they sold the source code and a cracked version of the Zeppelin ransomware builder for just $500.
The post was spotted by threat intelligence company KELA and while the legitimacy of the offer has not been validated, the screenshots from the seller indicate that the package is real.
Whoever bought the package could use the malware to spin up a new ransomware-as-a-service (RaaS) operation or write a new locker based on the Zeppelin family.
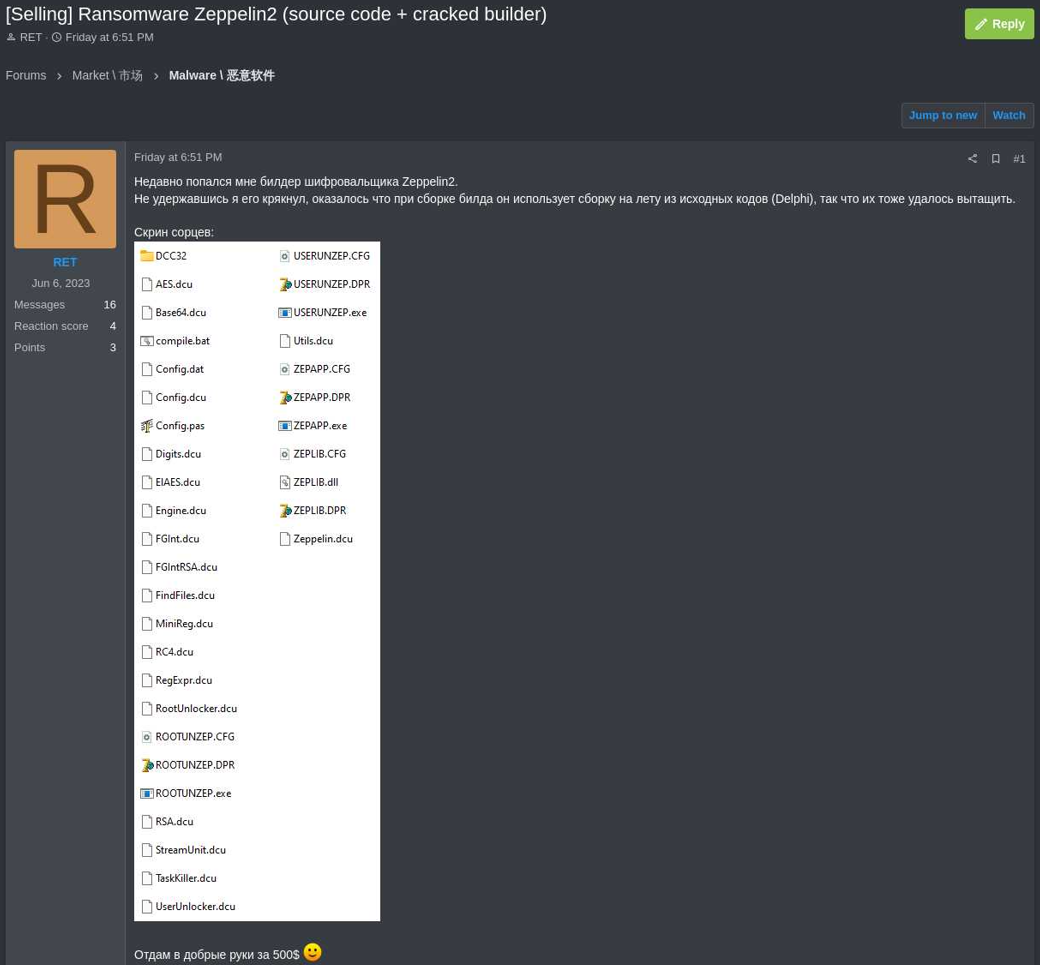
The seller of the Zeppelin source code and builder uses the handle 'RET' and clarified that they did not author the malware but simply managed to crack a builder version for it. RET added that they had acquired the package without a license.
"Where I got the builder without a license is my business. [...] I just cracked the builder," the seller wrote in a reply to other members of the hacker forum.
The cybercriminal noted that they intended to sell the product to a single buyer and would freeze the sale until completing the transaction.
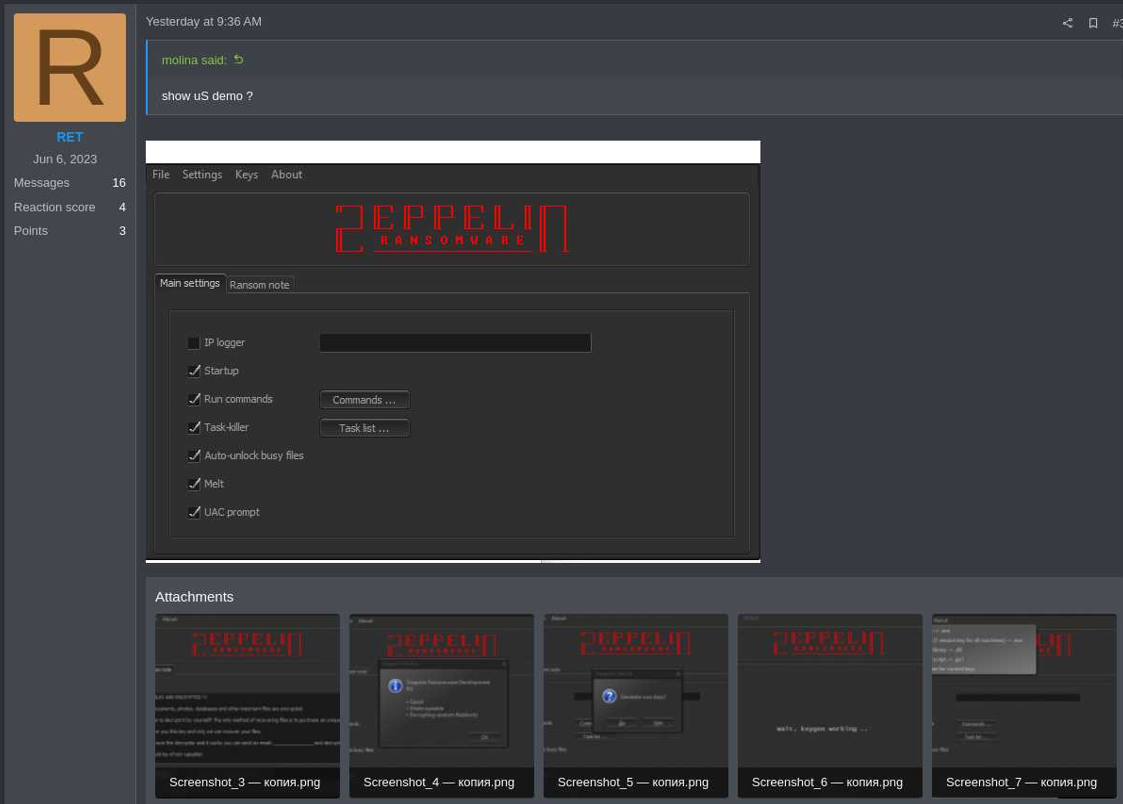
In November 2022, following the discontinuation of the Zeppelin RaaS operation, law enforcement and security researchers disclosed they had found exploitable flaws in Zeppelin's encryption scheme, allowing them to build a decrypter and help victims since 2020.
A user on the Zeppelin forum thread asks explicitly whether the new version has fixed the flaws in the cryptography implementation, to which the seller replies by saying that it's the second version of the malware that should no longer include the vulnerabilities.
Zeppelin ransomware background
Zeppelin is a derivative of the Delphi-based Vega/VegaLocker malware family that was active between 2019 and 2022. It was used in double-extortion attacks and its operators sometimes asked for ransoms as big as $1 million.
Builds of the original Zeppelin ransomware were sold for up to $2,300 in 2021, after its author had announced a major update for the software.
The RaaS offered a relatively advantageous deal to affiliates, allowing them to keep 70% of the ransom payments, with 30% going to the developer.
In the summer of 2022, the Federal Bureau of Investigation (FBI) warned about a new tactic employed by Zeppelin ransomware operators involving multiple rounds of encryption.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now