
Law enforcement has detained a suspect believed to be a key member of the OPERA1ER cybercrime group, which has targeted mobile banking services and financial institutions in malware, phishing, and Business Email Compromise (BEC) campaigns.
The gang, also known as NX$M$, DESKTOP Group, and Common Raven, is suspected of having stolen between $11 million and $30 million over the last four years in more than 30 attacks spanning 15 countries across Africa, Asia, and Latin America.
The suspect was arrested by authorities in Côte d'Ivoire in early June following a joint law enforcement action dubbed Operation Nervone with the help of AFRIPOL, Interpol's Cybercrime Directorate, cybersecurity company Group-IB, and telecom carrier Orange.
Further information that helped with the investigation was shared by the Criminal Investigative Division of the United States Secret Service and cybersecurity researchers from Booz Allen Hamilton DarkLabs.
"According to the INTERPOL's 2022 African Cyberthreat Assessment Report, cybercrime is a growing threat in the West Africa region, with victims located worldwide. Operation NERVONE underscores INTERPOL's commitment to proactively combat the threat of cybercrime in the region," Interpol said today.
"Operation Nervone was backed by two key INTERPOL initiatives: the African Joint Operation against Cybercrime and the INTERPOL Support Programme for the African Union in relation to AFRIPOL, funded by the United Kingdom's Foreign, Commonwealth & Development Office and Germany's Federal Foreign Office, respectively."
Group-IB analysts and the CERT-CC department at Orange, tracking the OPERA1ER group since 2019, have linked the threat actors to over 35 successful attacks between 2018 and 2022, roughly one-third of them carried out in 2020.
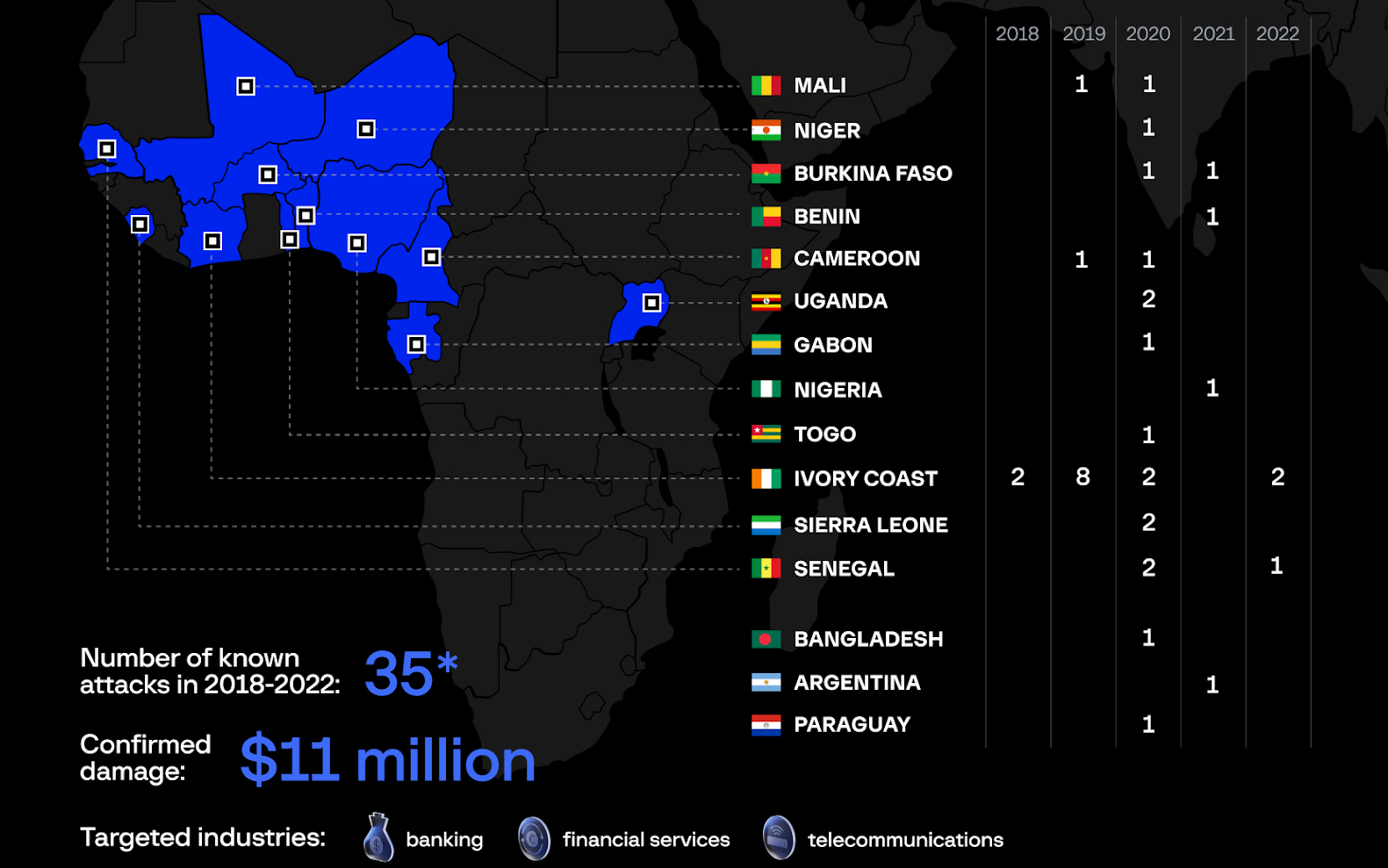
OPERA1ER members predominantly speak French and are believed to operate from Africa, and they rely on various tools in their attacks, including open-source solutions, common malware, and frameworks like Metasploit and Cobalt Strike.
However, initial access to targets' networks is gained through spear-phishing emails that exploit popular subjects such as invoices or postal delivery notifications and push a wide range of first-stage malware, including Netwire, BitRAT, venomRAT, AgentTesla, Remcos, Neutrino, BlackNET, and Venom RAT, as well as password sniffers and dumpers.
OPERA1ER has been observed maintaining access to compromised networks for a period ranging from three to twelve months, occasionally targeting the same company multiple times.
They also typically focus on operator accounts that control significant sums of money, using stolen credentials to transfer funds into Channel User accounts before ultimately redirecting them to subscriber accounts under their control. The group withdraws the stolen money as cash through an extensive network of ATMs over holidays or weekends to avoid detection.
Researchers at Symantec also found links between OPERA1ER and a cybercriminals group they track as Bluebottle that used a signed Windows driver in attacks against at least three banks in French-speaking African countries.
"Any attempt to investigate a sophisticated threat actor such as OPERA1ER, which stole millions from financial service companies and telecom providers across the world, requires a highly coordinated effort between public and private sector bodies," said Group-IB CEO Dmitry Volkov.
"The success of Operation Nervone exemplifies the importance of threat data exchange, and thanks to our collaboration with INTERPOL, Orange-CERT-CC and private and public sector partners, we were collectively able to piece together the whole puzzle."



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now