
Ransomware attacks continue to grow both in sophistication and quantity. 2023 has already seen more ransomware attacks involving data exfiltration and extortion than all of 2022, an increasing trend we expect to continue.
This article will explore the business model of ransomware groups and the complex cybercrime ecosystem that has sprung up around them.
The Rise of Triple Extortion Ransomware
Ransomware is traditionally associated with threat actors utilizing encryption to lock companies of data, systems, and IT infrastructure. However, in recent years, ransomware groups have evolved their tactics to not only encrypt data but also exfiltrate it, making it a double-edged weapon for extortion.
This new approach allows them to not only hold organizations hostage by denying access to their own data, but also threaten to leak or sell the stolen information if the ransom demands are not met.
This shift in strategy has proven to be highly profitable for ransomware groups, as organizations are often willing to pay large sums to prevent the public exposure of their sensitive data, which allows groups to profit off of victims even if the victim has an effective backup and recovery system.

Source: Flare
If a victim doesn't pay, groups will often auction off the data, providing another method to monetize their work.
The rise of data extortion ransomware has coincided with a dramatic increase in both the number of groups active and the number of attacks against organizations. Data extortion was originally added to the arsenal of ransomware groups as a double extortion technique, to be used in addition to encryption.
However, recently many groups have begun resorting to triple extortion , in some cases blackmailing individual employees, harassing third-party organizations of the victim, and even DDoSing websites in addition to data encryption and exfiltration.
Ransomware Groups, Affiliates, and Triple Extortion
Ransomware groups don't operate alone. They often have a network of affiliates who help them carry out attacks and distribute the ransomware. These affiliates may specialize in different aspects of the attack, such as initial access, data exfiltration, or negotiation.
Affiliate programs enable groups to focus on developing new variants, negotiation, or other aspects of the attack, allowing for role specialization and a greater number of attacks over time.
And it's paying off; Flare has already detected more ransomware data disclosures in 2023 than in all of 2022, representing a steep increase in the number of attacks.
Source: Flare
Additionally, since we are looking at disclosure, we are likely only identifying a small number of the total attacks against organizations.
As the ecosystem has grown, we have seen that ransomware groups are becoming increasingly aggressive. Groups such as Karakurt have been documented as not only exfiltrating data but also harassing individual employees and even third parties within the organization.
Triple Extortion Ransomware in Context: The Broader Cybercrime Ecosystem
The broader cybercrime ecosystem also acts as a crucial enabler for ransomware groups by offering services like bulletproof hosting, money laundering, initial access to environments, and employee credentials via stealer logs.
We'll cover a few of the main ways that the broader cybercrime ecosystem intersects with ransomware groups:
Ransomware Groups and Initial Access Brokers
Initial access brokers (IAB) are commonly active on the dark web forums Exploit and XSS. IABs work to compromise corporate IT infrastructure, which they then auction off on specific dark web forums, often with a start price, step price, and "blitz" or buy it now.

Source: Flare
In many cases, we have seen access brokers advertise that they have access to a victim's backup and recovery systems or that the victim lacks backup and recovery, providing further evidence that IABs expect their listings to be used for ransomware.
Stealer Logs: A Key Vector for Ransomware
Stealer logs likely represent another critical source of initial access to IT environments for ransomware groups. Stealer logs are the result of an infostealer malware infection.
These logs contain valuable information such as usernames, passwords, and other credentials that can be used to gain unauthorized access to systems.
Ransomware groups may acquire these logs from Telegram channels, dark web forums, or marketplaces, enabling them to bypass traditional methods of gaining access to a victim's network.
In a recent Flare analysis, we found more than 50,000 stealer logs that contained credentials to corporate single sign on applications. Stealer logs also include active session cookies, which can be used to bypass MFA authentication controls.
0-Days and Dark Web Marketplaces
The ransomware group CL0P exploited the 0-day MOVEit for enormous advantage, resulting in hundreds of victims and billions of dollars in damages.
0-days are likely one of the least common forms of access that ransomware groups use, due to the sophistication required to find and leverage them and the fact that there are far easier ways to facilitate an infection.
However, numerous dark web marketplaces, forums, and Telegram channels do facilitate sales of alleged 0-day exploits.
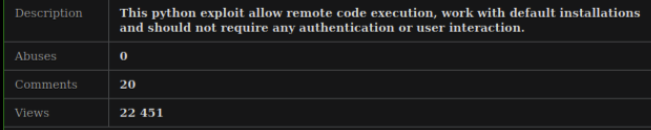
Source: Flare
More sophisticated ransomware groups will also likely source their own vulnerabilities rather than purchasing existing ones.
Ransomware is on the Rise
Data extortion ransomware schemes continue to explode in popularity, with new groups arising on a monthly basis and dozens of new victim organizations every week.
Building an effective continuous threat exposure management process that enables automated detection of stealer logs, ransom blog mentions, illicit Telegram channels , and monitoring of other cybercrime forums has never been more important than now.
Ransomware Detection & Remediation with Flare
Flare currently monitors more than 50 ransomware groups that are actively engaged in double and triple extortion schemes. Flare’s easy-to-use SaaS platform automates detecting company-specific threats across the clear & dark web and illicit Telegram channels.
Sign up for a free trial to learn more about how Flare can boost your security program’s cybercrime monitoring capabilities in 30 minutes.
Sponsored and written by Flare.

Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now