
Cloudflare says the number of hyper-volumetric HTTP DDoS (distributed denial of service) attacks recorded in the third quarter of 2023 surpasses every previous year, indicating that the threat landscape has entered a new chapter.
DDoS attacks are a type of cyberattack that involves directing large volumes of garbage traffic or large numbers of bogus requests to targeted servers hosting apps, websites, and online services to overwhelm and make them unavailable to legitimate visitors.
A Cloudflare report shared with BleepingComputer reveals that, during Q3 2023, the internet company mitigated thousands of hyper volumetric HTTP DDoS attacks.
Over 89 of these attacks exceeded 100 million requests per second (rps), and the largest one peaked at 201 million rps, three times larger than the previous record, which occurred in February 2023.
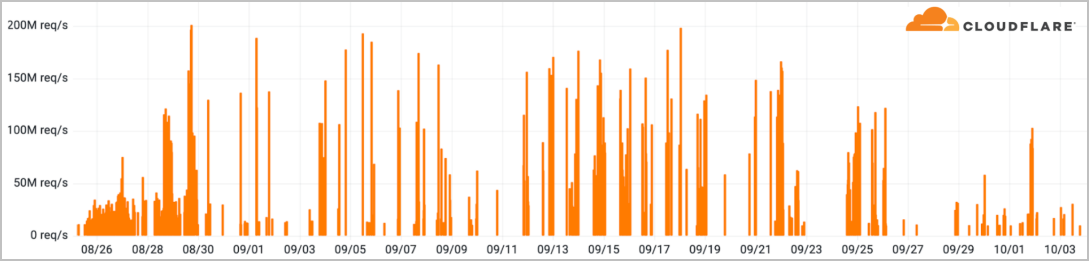
Source: Cloudflare
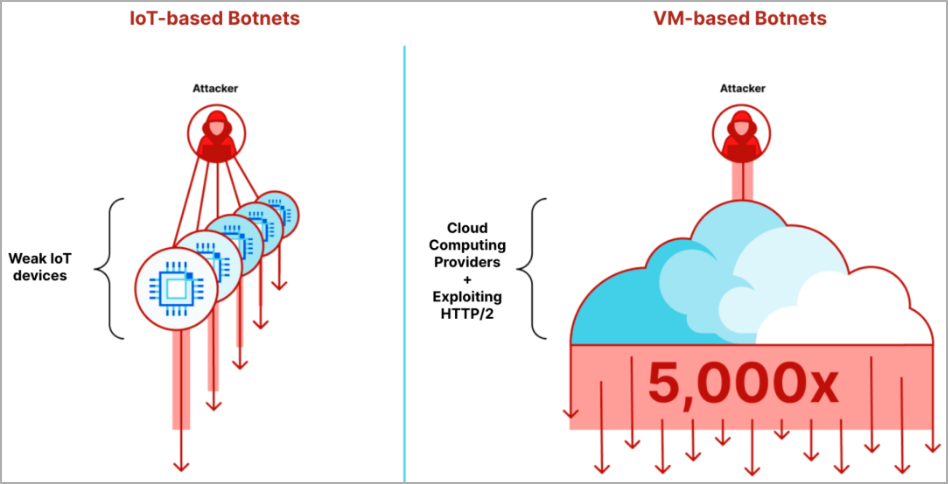
These attacks are made possible by exploiting a new technique named 'HTTP/2 Rapid Reset,' which threat actors have leveraged as a zero-day since August 2023.
The company says HTTP/2 Rapid Reset attacks have been employing VM-based botnets sized between 5-20 thousand nodes instead of millions of weak IoTs, able to deliver a much more significant punch per node.
Overall, Cloudflare reports a 65% rise in the aggregated volume of HTTP DDoS attack traffic in the last quarter and an increase of 14% in L3/L4 DDoS attacks.
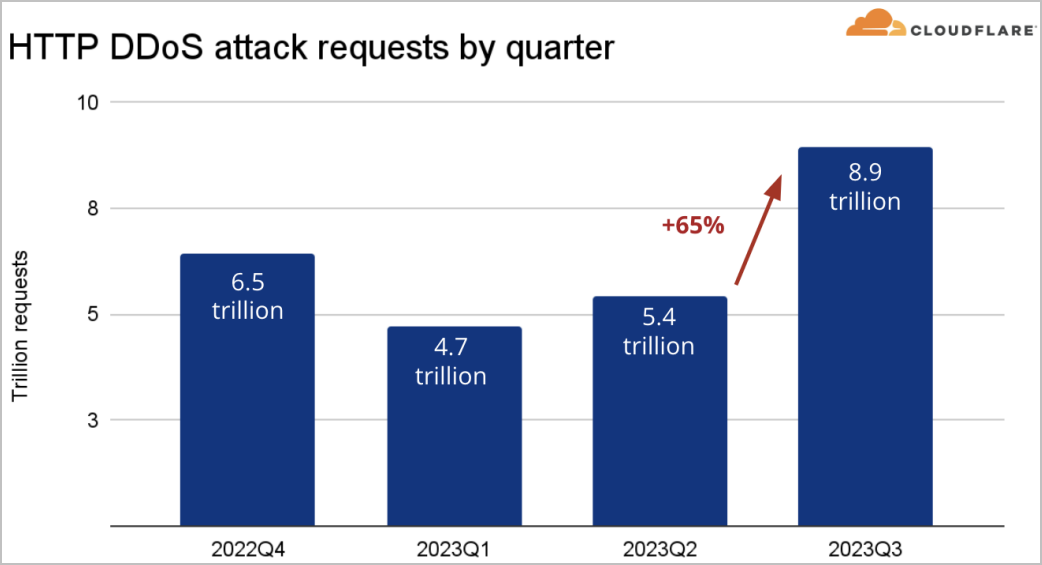
Source: Cloudflare
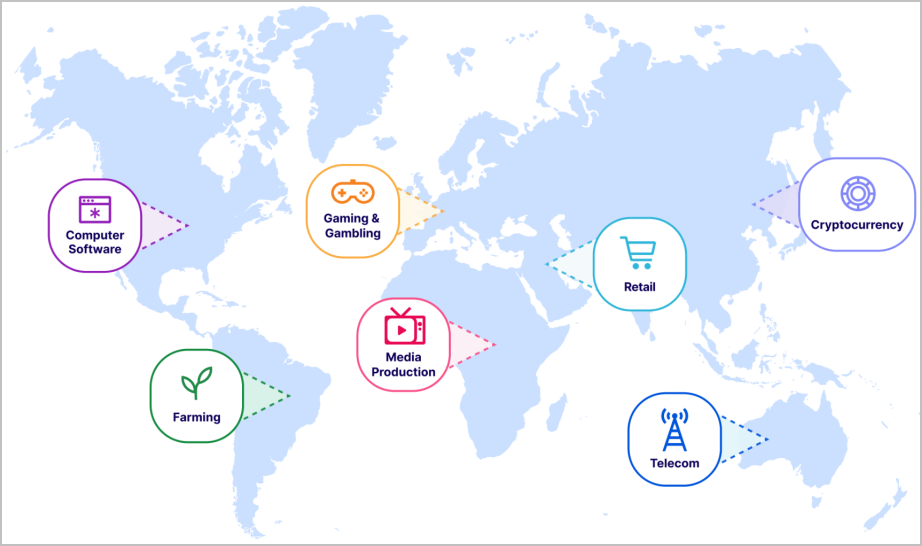
Regarding the targets this quarter, gaming and gambling entities took the lion's share of HTTP DDoS, followed by IT and internet services, cryptocurrency, software, and telecommunications.
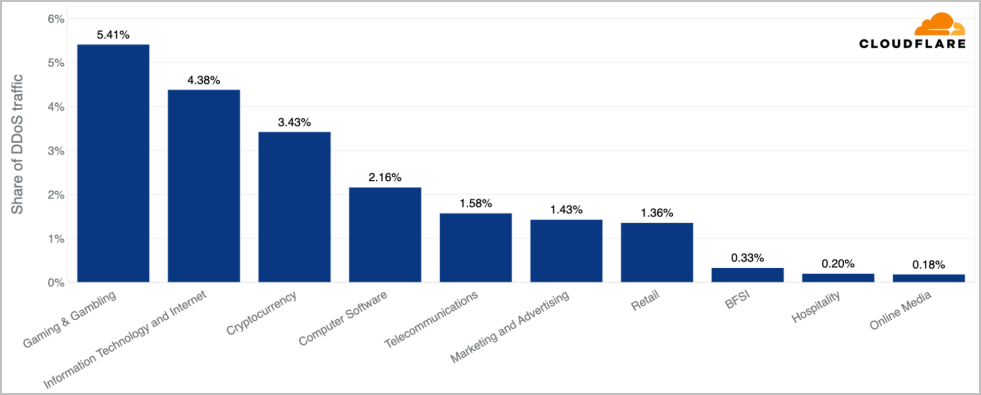
Source: Cloudflare
Application-layer DDoS attacks, on the other hand, mostly targeted mining firms, non-profit organizations, pharmaceuticals, and the U.S. Federal government.
Source: Cloudflare
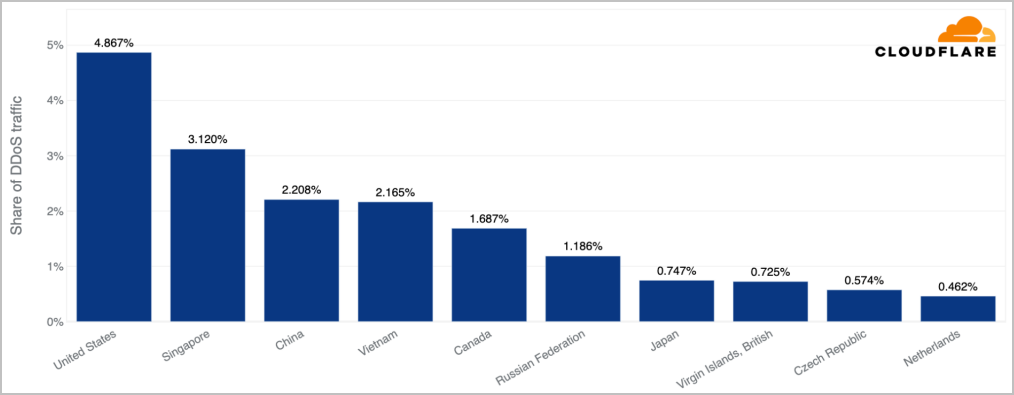
Nearly 5% of all HTTP DDoS traffic was directed to entities in the United States, over 3.1% went to firms in Singapore, and China came third with 2.2%.
Source: Cloudflare
Emerging trends in the DDoS landscape
Cloudflare has also observed trends in lesser-known attack vectors that could indicate the emergence of new attack strategies.
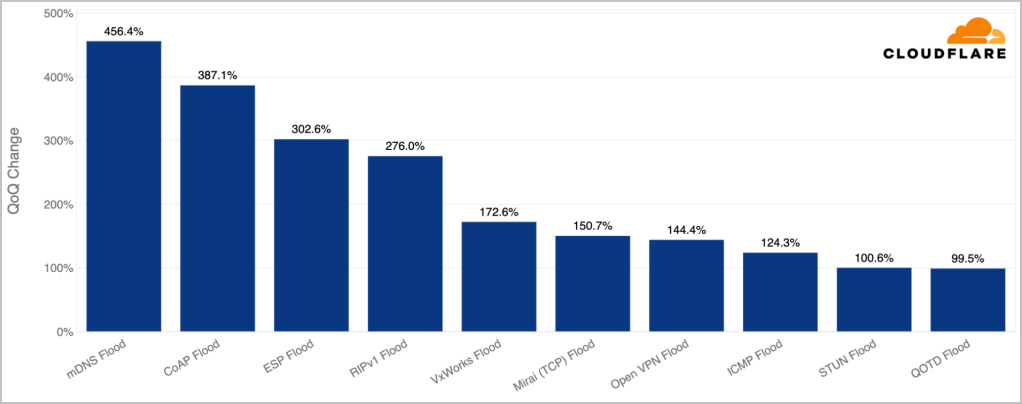
The first notable trend is a quarterly increase of 456% in the observed mDNS (multicast DNS) attacks.
MDNS is a UDP-based protocol for service/device discovery in local networks that attackers exploit for amplification attacks, tricking vulnerable mDNS servers to respond to malicious queries with the target's address.
The second significant increase concerns CoAP (Constrained Application Protocol), which recorded an uptick of 387%.
CoAP is a protocol designed for lightweight communication between simple electronic devices. Attackers exploit poorly configured devices to abuse the protocol's multicast capabilities and generate unwanted traffic.
The third observed trend is an increase of 303% in the ESP (Encapsulating Security Payload) DDoS attacks this quarter.
ESP, part of IPsec, is a secure network communications protocol that can be abused in misconfigured or vulnerable devices to amplify DDoS attacks.
Source: Cloudflare
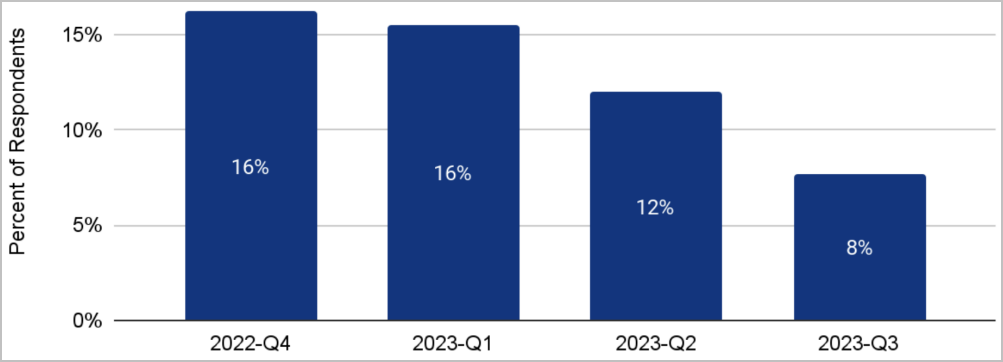
Finally, Cloudflare reports that ransom DDoS attacks follow a negative trend, falling for the second successive quarter.
Source: Cloudflare
DDoS attacks constantly evolve as threat actors adapt and explore new techniques to circumvent modern defenses. Furthermore, hacktivist groups have increasingly used DDoS attacks to target political entities or a country's organizations that they are protesting.
The most effective defense strategy encompasses a comprehensive, multi-layered approach to enhance DDoS resilience. However, as new techniques emerge, companies and security companies will need to evolve their defense strategies.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now