
With the United State tax season in high gear, threat actors have sprung into action with a recent tax document phishing scam that abuses TypeForm forms to steal your login credentials.
TypeForm is a website that allows you to create compelling and intricate forms that are used to collect legitimate information, conduct surveys, or even create quizzes that you can embed on a site.
As with all good things, threat actors are known to abuse TypeForm to create convincing login forms used as part of their phishing scams.
In a new report by email security firm ArmorBlox, researchers outline one such phishing scam that aims to take advantage of the 2021 tax season by pretending to be a W-2 tax document shared via Microsoft OneDrive.
The scam starts with users receiving an email pretending to be from OneDrive where a file named '2020_TaxReturn&W2.pdf ' is shared with the user.
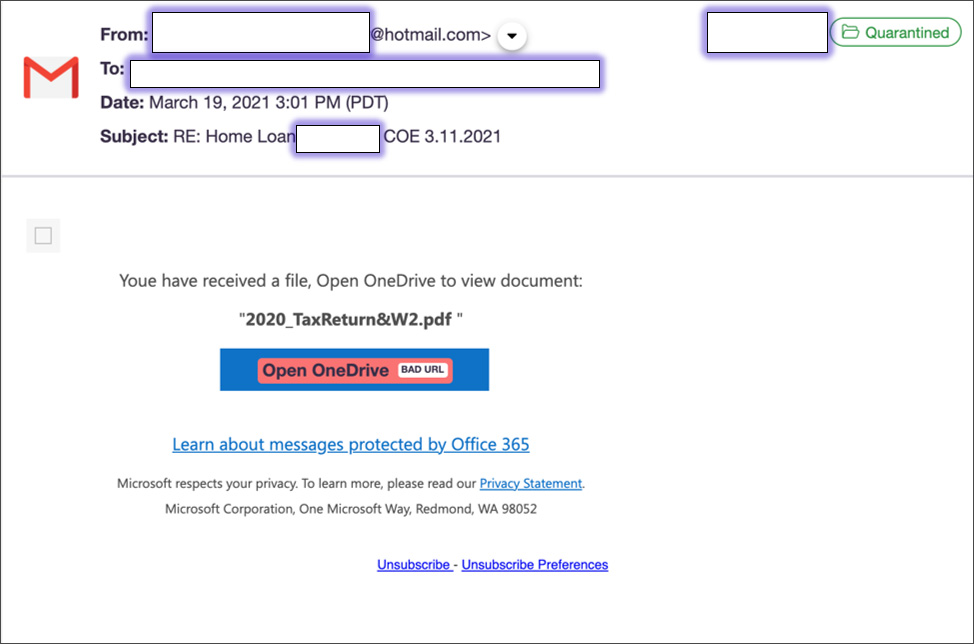
In the past, companies always sent US tax documents via postal mail but have more recently started to move towards digital delivery of tax documents, such as 1099 and W-2 forms. While the above email does not stand up to scrutiny, for someone who is overwhelmed, receiving a tax form via email would not necessarily trigger suspicion and could lead them to mistakenly clicking on the embedded link.
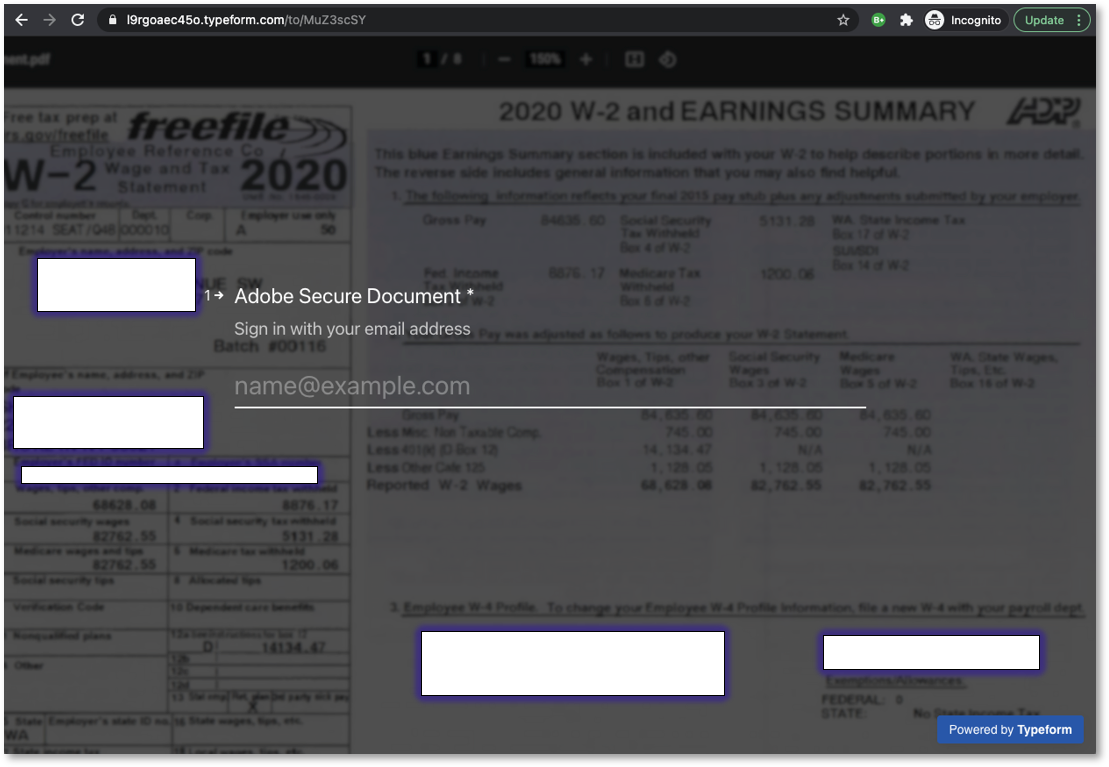
When a recipient clicks on the link to retrieve the document, they are brought to a TypeForm form that includes a blurred out 2020 W-2 tax document pretending to be secured by the Adobe Secure Document service.
This form, shown below, will request that the visitor enter their email address and password to log in and retrieve the W-2 document.
When entering their credentials, the form will repeatedly state that the credentials are incorrect until it ultimately displays a message saying the service was "Unable to verify your identity."
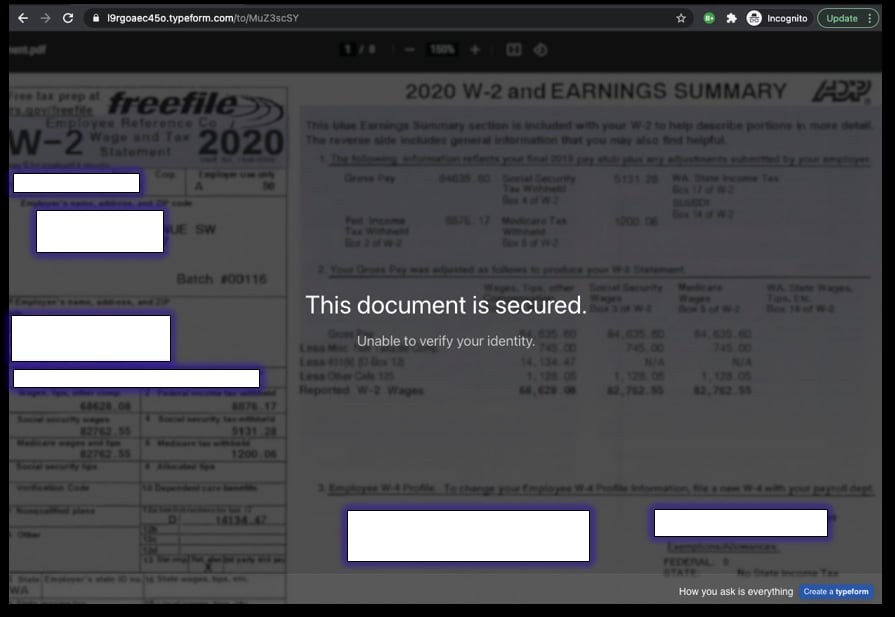
ArmorBlox researchers believe that these repeated failed login messages are simply a cover for the threat actors trying to capture as many credentials as they can while the recipient tries various user name and password combinations.
"It’s likely that the error messages could be a smokescreen for the attackers to gather as many account ID and password combinations as unsuspecting victims are willing to enter in an attempt to brute-force their way to gain access to the W2. In reality, there is no W2 pot of gold at the end of this malicious rainbow," ArmorBlox explains in their report.
TypeForm is not the only legitimate form creation service to be abused by threat actors. Other phishing campaigns have used Google Forms and Canva to steal login credentials.
Microsoft Forms is also heavily abused, which has led Microsoft to proactively warn IT admins when they detect phishing campaigns abusing Microsoft Forms in their Active Directory tenants.
To prevent falling for these types of scams, it is always important to take a minute to scrutinize unexpected emails, especially those containing links to shared documents or that prompt you to log in to a service.
Usually, there are tells that allow you to spot that something is not right, which could be senders using free email services, spelling errors, bad grammar, or just strange requests from the recipient.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now