
A recent survey of 100 large (over 5,000 employees) North American IT firms shows that ransomware actors are making greater effort to recruit insiders in targeted firms to aid in attacks.
The survey was conducted by Hitachi ID, which performed a similar study in November 2021. Compared to the previous survey, there has been a 17% rise in the number of employees offered money to aid in ransomware attacks against their employer.
Most specifically, 65% of the survey respondents say that they or their employees were approached between December 7, 2021, and January 4, 2022, to help hackers establish initial access.
.jpg)
Source: Hitachi ID
In most cases, the threat actors used email and social media to contact employees, but 27% of their approach efforts were conducted via phone calls, a direct and brazen means of contact.
As for the money offered to the employees, most received an offer below $500,000, but some proposals were north of a million USD.
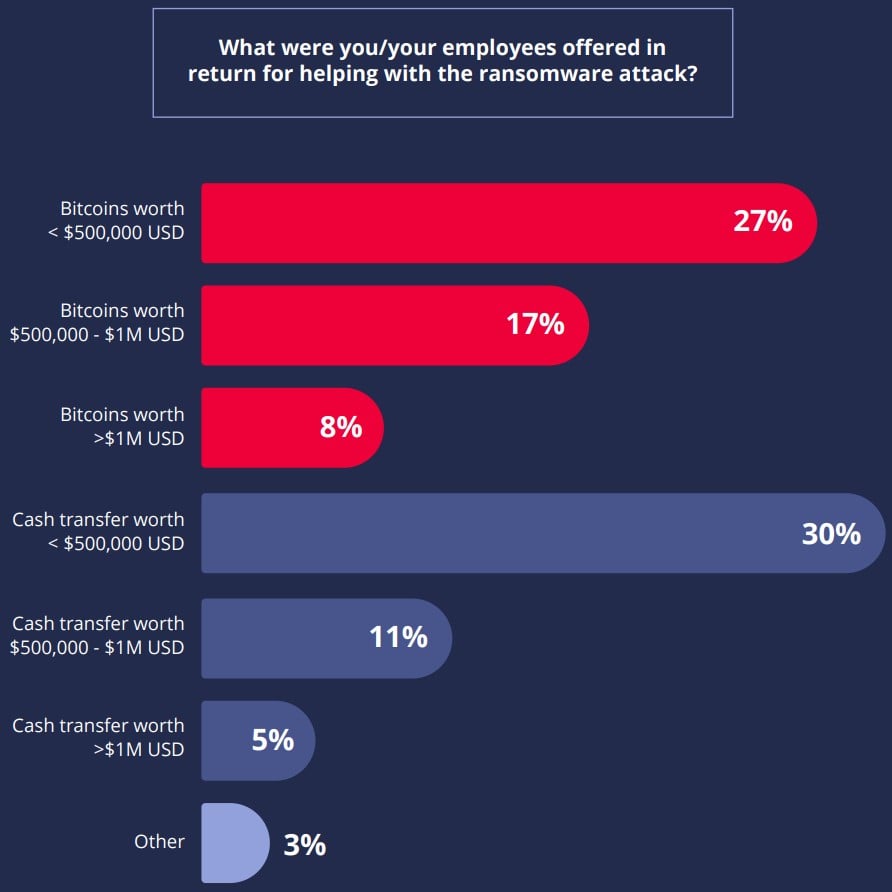
Source: Hitachi ID
In half of those cases, ransomware gangs attacked the targeted company even without any insider help.
This shows that once a firm is a candidate for a ransomware attack, the rest is just about exploring potential ways to make the infiltration easier and less likely to be detected.
An ignored area
As reflected in the findings of the Hitachi ID survey, insider threats are generally ignored, underrated, and not accounted for when developing cybersecurity plans.
When IT executives were questioned about how concerned they are about internal threats, 36% responded with more concern about external threats, with 3% not worried about threats at all.
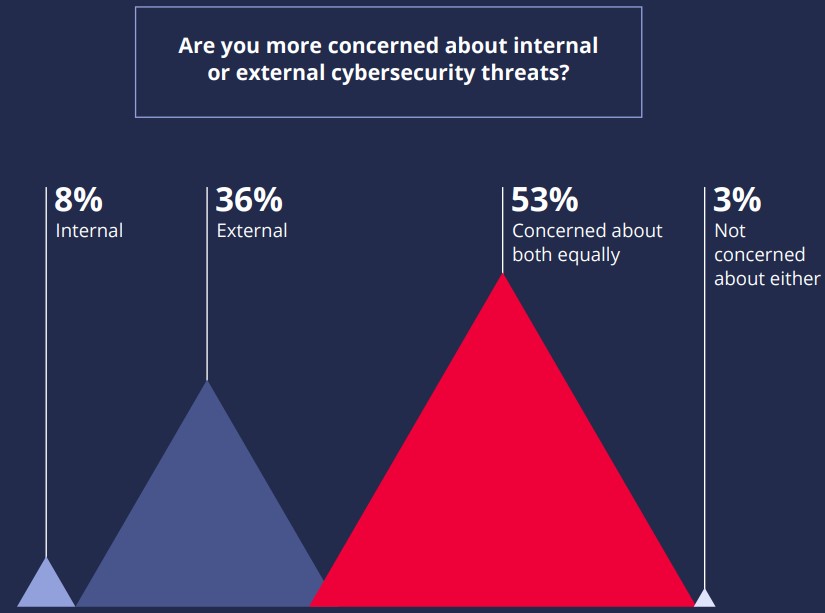
Source: Hitachi ID
Since last summer, when the LockBit 2.0 ransomware operation openly invited rogue employees to help them gain corporate network access, the awareness around the issue has been raised, but the problem persists.
CISA released a tool that can help companies assess their stance against insider threats in September 2021, warning that the particular trend is rising.
The entities that decided to do something about the issue increased employee training and sent fake emails to employees in critical areas with reports of disgruntled employees or low-performance indicators. However, most haven’t implemented specific security measures to curb the problem.
Ideal timing
The fact that the United States is going through a job quitting surge called the “Great Resignation” raises the chances of success for ransomware actors in these peculiar negotiations.
Today, many companies have employees on the verge of quitting or who have already decided to leave but wait for the right moment, and an unexpected offer involving a large sum of money may be enticing for some.
An increasing number of people feel over-stressed, underpaid, exploited, exhausted, or don’t feel like work is worth their time and energy anymore.
These people may be seen as ideal candidates for ransomware gangs who entice them with a hefty payment to be short-term accomplices.



Comments
JustinFlynn - 2 years ago
I'd like to meet the 3% that have no concern over Internal or External threats.
Elko_NV - 2 years ago
Is estimated, still less than 15% of businesses have any Cyber Insurance. This may deter me if i was your average bad employee. The better carriers have 24/7 claims lines that enlist professionals to ID the type of encryption, try to kick the TA's off the network, remediate the network to how it was prior, and potentially negotiate a ransom payment as a last resort (while working with law enforcement).