
Multiple ASUS router models are vulnerable to the Russia-linked Cyclops Blink malware threat, causing the vendor to publish an advisory with mitigations for the security risk.
Cyclops Blink is a malware linked to the Russian-backed Sandworm hacking group that has historically targeted WatchGuard Firebox and other SOHO network devices.
The role of Cyclops Blink is to establish persistence for threat actors on the device, allowing them a point of remote access to compromised networks.
Because Cyclops Blink is modular, it can be easily updated to target new devices, constantly refreshing its scope and tapping into new pools of exploitable hardware.
Cyclops Blink now targets ASUS routers
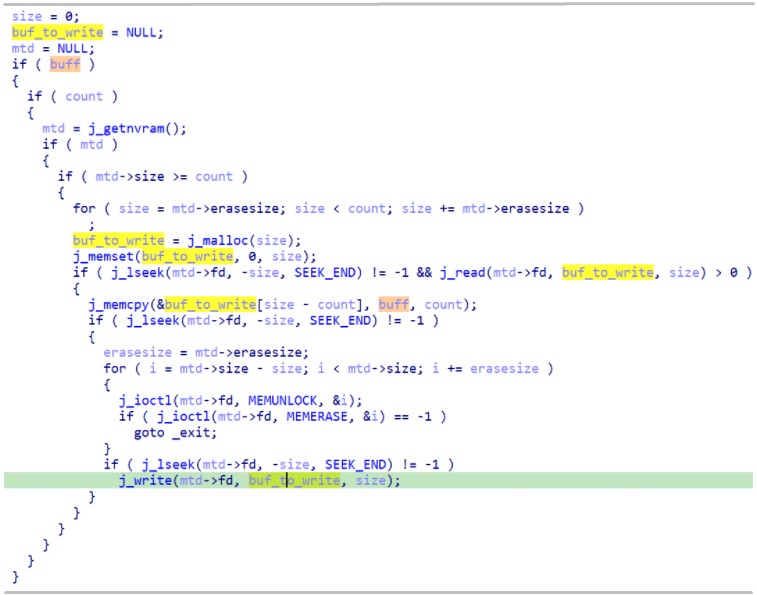
In a coordinated disclosure, Trend Micro warned that the malware features a specialized module that targets several ASUS routers, allowing the malware to read the flash memory to gather information about critical files, executables, data, and libraries.
The malware then receives a command to nest in the flash memory and establish permanent persistence, as this storage space doesn't get wiped even by factory resets.
For more details on the ASUS module of Cyclops Blink, Trend Micro has published a technical writeup today explaining how it works.
At this point, the spread of Cyclops Blink appears indiscriminate and widespread, so it doesn't matter if you consider yourself a legitimate target or not.
As the malware is tied to the elite Sandworm hacking group (also tracked as Voodoo Bear, BlackEnergy, and TeleBots), we will likely see the threat actors targeting other router manufacturers in the future.
Sandworm has been linked to other well-known cyberattacks, including the BlackEnergy malware behind the Ukrainian blackouts of 2015 and 2016 [1, 2, 3] and the NotPetya ransomware, which led to billions worth of damage to companies worldwide starting in June 2017.
Vulnerable ASUS devices
In an advisory released today, ASUS warns that the following router models and firmware versions are vulnerable to Cyclops Blink attacks:
- GT-AC5300 firmware under 3.0.0.4.386.xxxx
- GT-AC2900 firmware under 3.0.0.4.386.xxxx
- RT-AC5300 firmware under 3.0.0.4.386.xxxx
- RT-AC88U firmware under 3.0.0.4.386.xxxx
- RT-AC3100 firmware under 3.0.0.4.386.xxxx
- RT-AC86U firmware under 3.0.0.4.386.xxxx
- RT-AC68U, AC68R, AC68W, AC68P firmware under 3.0.0.4.386.xxxx
- RT-AC66U_B1 firmware under 3.0.0.4.386.xxxx
- RT-AC3200 firmware under 3.0.0.4.386.xxxx
- RT-AC2900 firmware under 3.0.0.4.386.xxxx
- RT-AC1900P, RT-AC1900P firmware under 3.0.0.4.386.xxxx
- RT-AC87U (EOL)
- RT-AC66U (EOL)
- RT-AC56U (EOL)
At this time, ASUS has not released new firmware updates to protect against Cyclops Blink but have released the following mitigations that can be used to secure devices:
- Reset the device to factory default: Login into the web GUI, go to Administration → Restore/Save/Upload Setting, click the "Initialize all the setting and clear all the data log," and then click Restore button."
- Update to the latest available firmware.
- Ensure the default admin password has been changed to a more secure one.
- Disable Remote Management (disabled by default, can only be enabled via Advanced Settings).
If you are using any of the three models designated as EOL (end of life), note that these are no longer supported and thus won't receive a firmware security update. In this case, you are recommended to replace your device with a new one.
If you own WatchGuard network devices and are looking for that advisory instead, you can find the vendor's threat mitigation advice on this webpage.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now