Today, researchers have disclosed their findings on a novel Windows malware sample that uses Internet Control Message Protocol (ICMP) for its command-and-control (C2) activities.
Dubbed "Pingback," this malware targets Microsoft Windows 64-bit systems, and uses DLL Hijacking to gain persistence.
Abuses real Windows service to load malicious DLL
Today, Trustwave senior architect Lloyd Macrohon and principal security researcher Rodel Mendrez, have released their findings on a novel Windows malware that exists as a 64-bit DLL.
Of note is the malware sample's choice of the communication protocol being ICMP, which is also used by the popular ping command and the Windows traceroute utility.
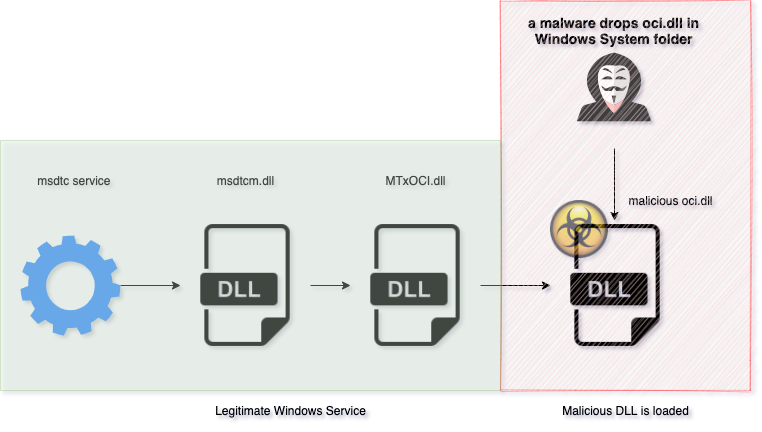
The malicious file in question is a mere 66-KB DLL called oci.dll, and is typically dropped within Windows "System" folder by another malicious process or attack vector.
The researchers soon realized that this DLL was not being loaded by the familiar Windows application rundll32.exe, but instead relied on DLL Hijacking.
Source: Trustwave
"We knew that the file was suspicious during our initial triaging, but we could not figure how it was loaded into the system because the DLL was not loaded through traditional rundll32.exe," state Macrohon and Mendrez.
DLL Hijacking is a technique used by attackers on Windows systems that involves placing a malicious DLL file in one of the folders trusted by the Windows operating system, such that a legitimate system application picks up and runs the malicious DLL file.
In this manner, attackers can exploit a real, trusted Windows process to execute their arbitrary malicious code.
Last year, BleepingComputer had reported, about 300 Windows executables could be abused for DLL Hijacking.
In this case, Trustwave's researchers identified it was the Microsoft Distributed Transaction Control (msdtc) service being abused to load the malicious oci.dll.
In fact, msdtc.exe is present on the list of over 300 Windows executables that make the perfect candidates for DLL Hijacking, as compiled by PwC researcher Wietze Beukema.
On launch, the Windows msdtc service searches for 3 DLLs to load: oci.dll, SqlLib80.dll, and xa80.dll.
The real oci.dll represents an Oracle library (Oracle Call Interface) that exists for supporting and interacting with Oracle databases. But, here's the catch:
"By default, the three Oracle DLLs do not exist in the Windows system directory."
"So, in theory, an attacker with system privileges can drop a malicious DLL and save it using one of the DLL filenames that MTxOCI loads," explain the researchers.
Although the researchers experimented with dropping all 3 DLL filenames on Windows, they found that only oci.dll could be seamlessly loaded by the msdtc service.
But, where does the malicious oci.dll come from?
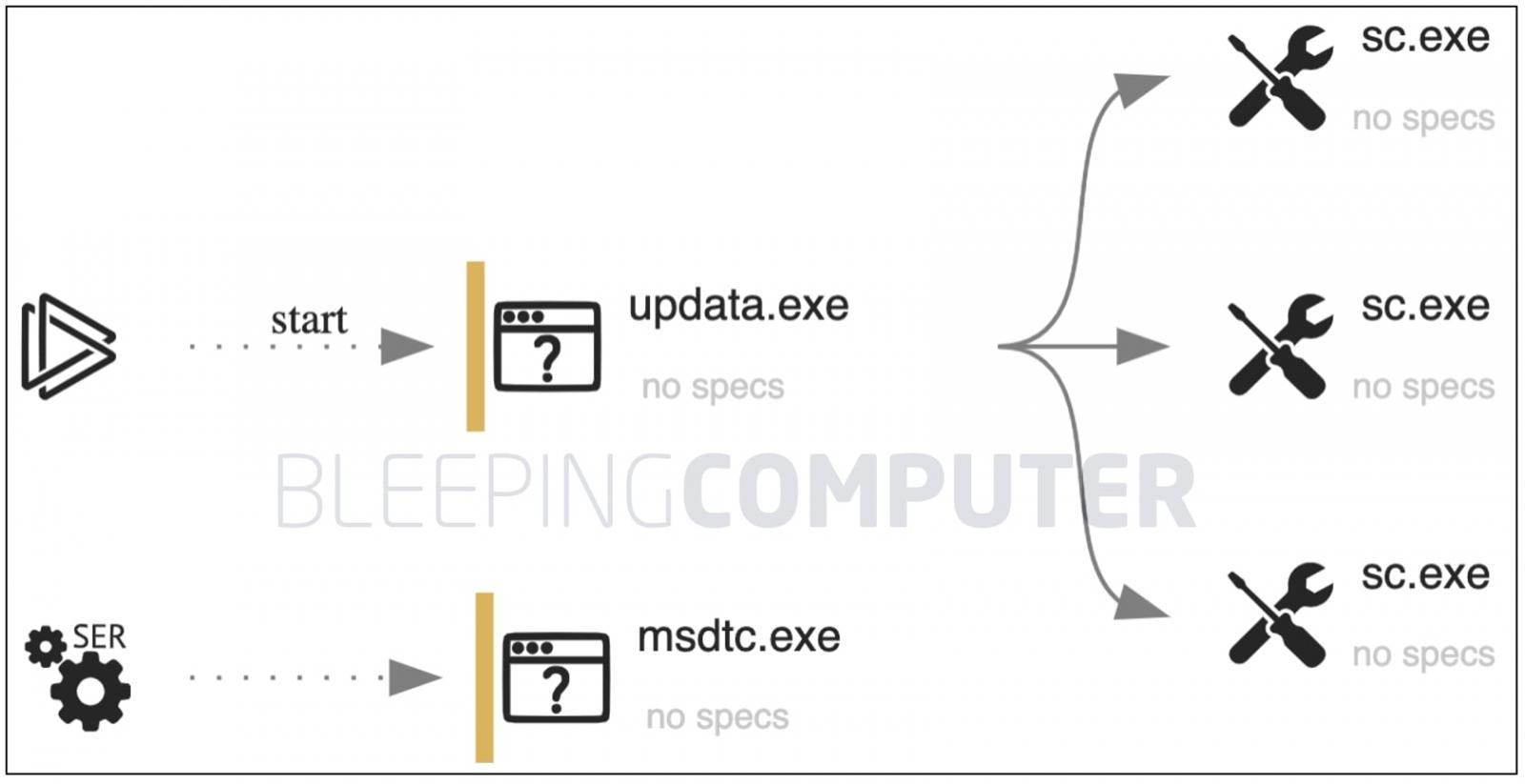
While the initial entry vector is still being investigated, the researchers suspect that another malware sample, updata.exe is behind both dropping the malicious oci.dll in the Windows "System" folder and configuring msdtc to run on every startup.
As analyzed by BleepingComputer, updata.exe indeed executes a sequence of commands to configure msdtc to run persistently and further drops oci.dll:
sc config msdtc obj= Localsystem start= auto
sc start msdtc
Source: BleepingComputer (analyzed on ANY.RUN)
Uses ICMP tunneling for covert communication
The oci.dll malware once launched by msdtc, uses ICMP for stealthily receiving commands from its C2 server.
Trustwave researchers who named this malware "Pingback," state that the advantage of using ICMP for communications is that Pingback remains effectively hidden from a user.
That's because ICMP has no concept of "ports" and uses neither TCP nor UDP. As such, oci.dll may not be picked up by diagnostic tools like netstat.
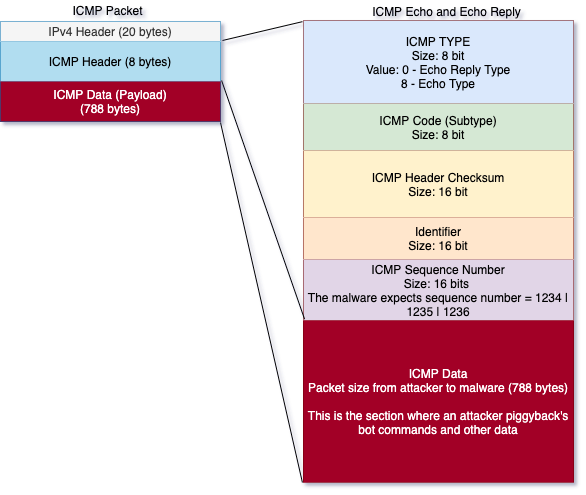
Every ICMP packet, however, does contain a "data" field with enough space to sneak in custom data within the field and to transmit it back and forth between two systems:
Source: Trustwave
"The ICMP data section is where an attacker can piggyback an arbitrary data to be sent to a remote host. The remote host replies in the same manner, by [piggybacking] an answer into another ICMP packet and sending it back," explain Macrohon and Mendrez.
Pingback malware (oci.dll) simply listens for any and all inbound ICMP packets on an infected system and selectively parses packets with sequence numbers: 1234, 1235, or 1236.
An incoming ICMP packet with sequence number 1234 indicates to the malicious process that this request contains payload or commands, whereas 1235 and 1236 are Pingback's way of keeping track of and acknowledging if a request has been received on either end.
The data received can contain C2 commands like shell, download, upload, exec, etc.
In essence, these commands are used to transmit data back and forth between the attacker-controlled server and the infected system and enable a remote attacker to execute other arbitrary commands on the infected system.
BleepingComputer also noticed, oci.dll referenced a fictitious file path named after Visual Studio 2008 that may appear to contain legitimate project data to a casual observer, but is likely used by the Pingback malware for its nefarious activities, such as data storage:
"ICMP tunneling is not new, but this particular sample piqued our interest as a real-world example of malware using this technique to evade detection," state the researchers.
But, since ICMP also has legitimate use-cases as a diagnostic tool, the researchers' advice is not to disable it, but rather putting monitoring mechanisms in place to detect any suspicious ICMP traffic.
Trustwave's detailed technical findings are provided in a blog post. The researchers have also created a proof-of-concept C2 bot to demonstrate some of Pingback's commands.
The Indicators of Compromise (IOCs) associated with the Pingback malware are provided below:
File: oci.dll
SHA256: E50943D9F361830502DCFDB00971CBEE76877AA73665245427D817047523667F
SHA1: 0190495D0C3BE6C0EDBAB0D4DBD5A7E122EFBB3F
MD5: 264C2EDE235DC7232D673D4748437969
Network:
ICMP Type=8
Sequence Number: 1234|1235|1236
Data size: 788 bytes



Comments
Kotodzyo - 2 years ago
damn, this is a good one