
An ongoing malware distribution campaign targeting South Korea is disguising RATs (remote access trojans) as an adult game shared via webhards and torrents.
The attackers are using easily obtainable malware such as njRAT and UDP RAT, wrap them in a package that appears like a game or other program, and then upload them on webhards.
WebHard is a popular online storage service in Korea, preferred mainly for the convenience of direct downloads.
Users end up at webhards through Discord or social media posts, but popular storage repositories enjoy a steady stream of daily visitors due to the content that is shared.
As reported by analysts at ASEC, threat actors are now using webhards to distribute a UDP RAT that is disguised as ZIP file containing an adult game.
When extracted, the archive contains a 'game.exe' launcher, which is actually the UDP rate malware.
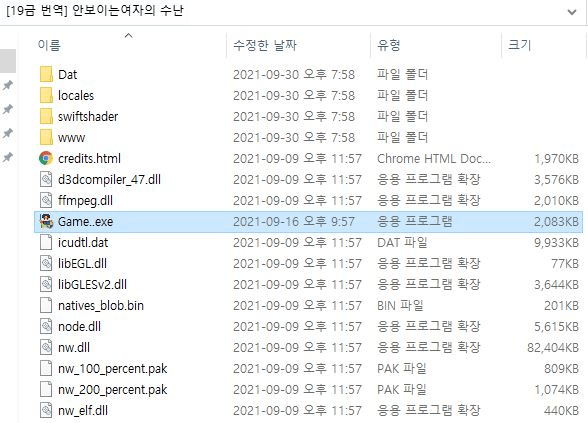
Source: ASEC
Upon execution, Game.exe drops a Themida-packed RAT and becomes hidden, while it subsequently creates a new Game.exe file that will run the actual game, convincing the victim that all went well.
Malware executables are dropped into the ‘C:\Program Files\4.0389’ folder, and are malware fetchers that can connect to the C&C and download further malicious payloads.
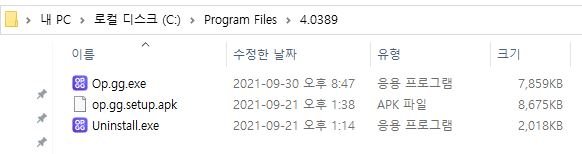
Source: ASEC
For this campaign, ASEC was unable to sample any of the additional payloads, so this may be a functionality preserved for future deployment or it's just intermittently used.
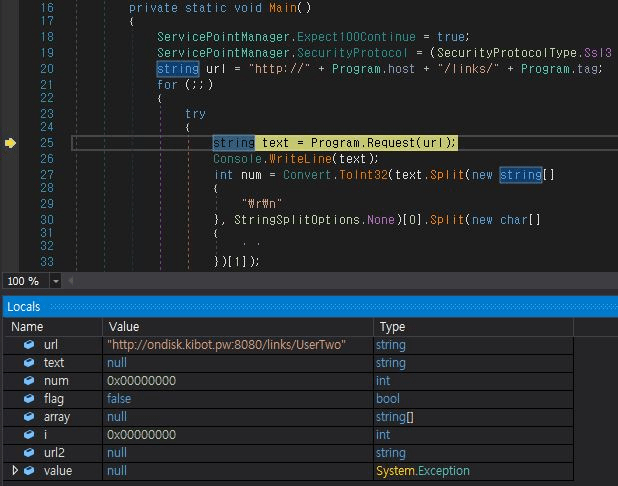
Source: ASEC
Malware like njRAT is particularly dangerous as it can steal sensitive information for the threat actors, including account credentials and keystrokes.
These tools are typically capable of capturing screenshots on the compromised device, and they also modify the Windows Registry for persistence.
In this case, the malware adds a Registry key to ensure a periodical connection to the C2 server, keeping the possibility of fetching more payloads open.
Actors have employed various tricks to convince people to download njRATs on their systems, but file hosting services and torrents remain a stable source of trouble.
Webhards are typically unregulated spaces, with no one checking what users upload and share with others on the platform, so whenever you’re pointed to one, be very careful.
ASEC warned about this risk again in June, when actors distributed yet another commodity malware disguised as a platformer game named ‘Lost Ruins’.
That package also had the capacity to run both the game and the malware simultaneously, making it a lot harder to realize the infection.
8 Common Threats in 2025
While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz's detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.









Comments
NoneRain - 3 years ago
"disable your AV to run the game" - rip
EmanuelJacobsson - 3 years ago
People who use pirated/cracked/torrented software will follow any instruction if they are told to do so.