Large-scale phishing activity using hundreds of domains to steal credentials for Naver, a Google-like online platform in South Korea, shows infrastructure overlaps linked to the TrickBot botnet.
The resources used for this attack show the sheer size of the cybercriminal effort to collect login data to be used in various attacks.
Similar to Google, Naver provides a diverse set of services that range from web search to email, news, and the NAVER Knowledge iN online Q&A platform.
Massive infrastructure
Besides access to normal user accounts, Naver credentials can also open the door to enterprise environments, as a result of password reuse.
Security researchers at cyber intelligence company Prevailion earlier this year identified a massive phishing operation focused on collecting credentials of Naver users.
They started the investigation from one domain name - mailmangecorp[.]us - shared by Joe Słowik, which opened the door to a “vast network of targeted phishing infrastructure designed to harvest valid login credentials for Naver.”
“While investigating the hosting infrastructure being used to serve the Naver-themed phishing pages, PACT analysts identified overlaps with the WIZARD SPIDER [a.k.a. TrickBot] infrastructure,” Prevailion says in a report today.
The TrickBot operation is believed to have changed management recently, with its old partner, the Conti ransomware syndicate, moving to its helm.
The researchers linked 542 unique domains to the operation, 532 of them being used for Naver-themed phishing. They noticed that the operator would use an email address to register a set of domain names that resolved to a single IP address.
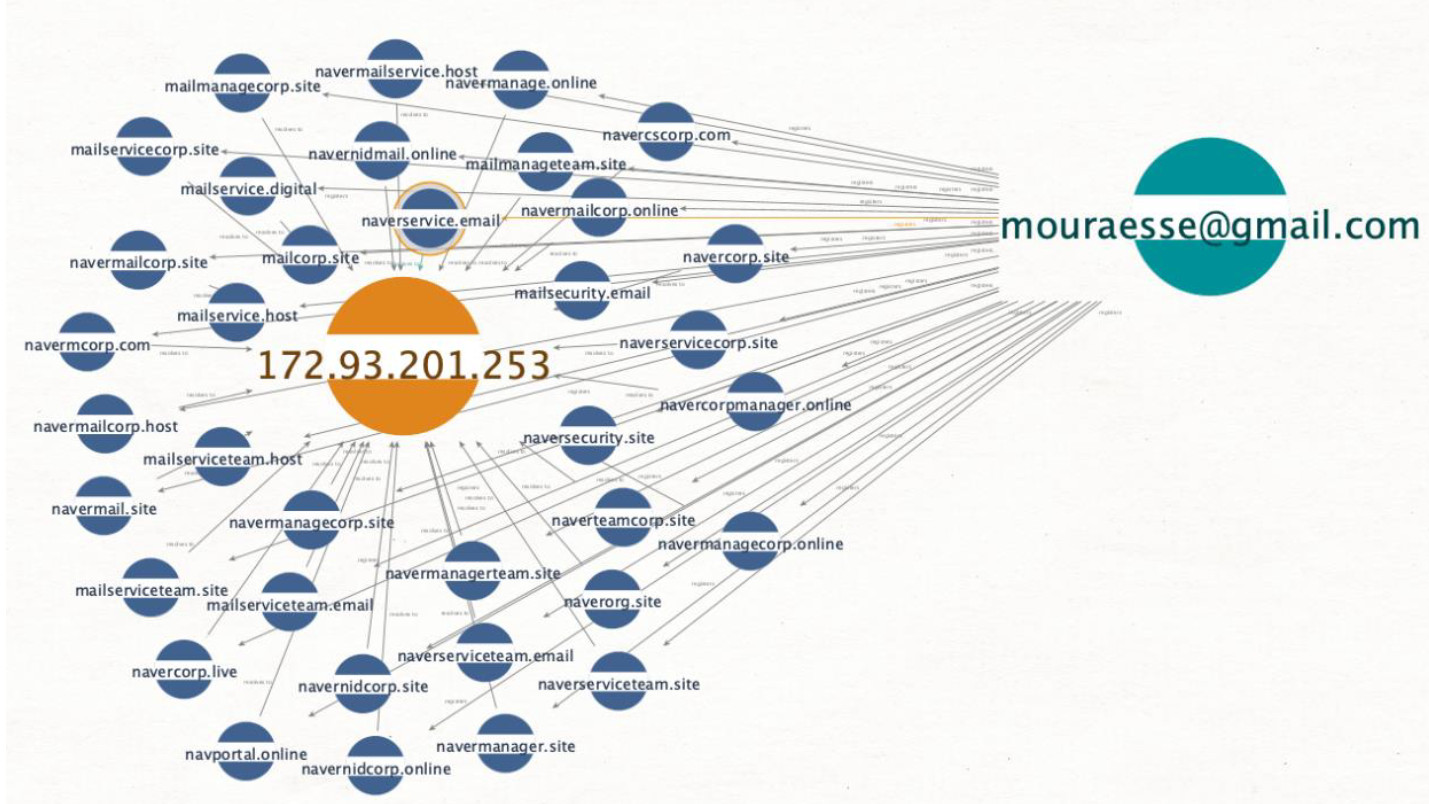
The threat actor relied on multiple addresses to create registrant personas for the Naver campaign. Some of the domains are registered as recently as February, while the oldest ones date from August 2021.
Prevailion researchers discovered that the domains resolving to the IP address in the image above were part of a redirect scheme (HTTP/302) that took potential victims to fake login pages for the Naver platform hosted on Hostinger.
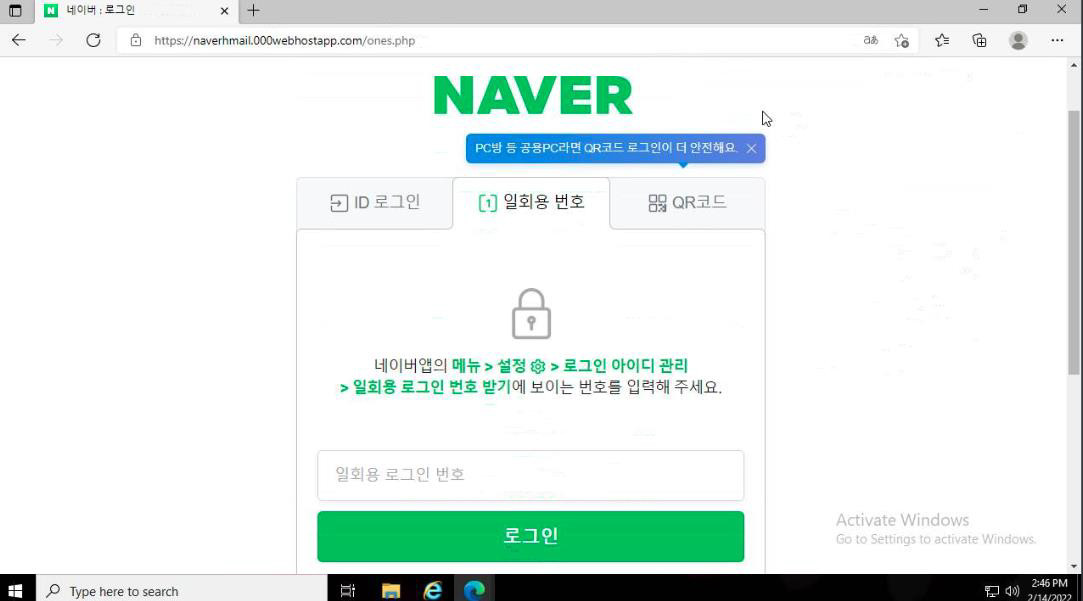
From the initial email address, Prevailion was able to find another cluster of 58 phishing domains resolving to 23.81.246[.]131, an IP address that proved critical in establishing the initial connection between Naver credential phishing and the infrastructure associated with TrickBot.
According to the researchers, a couple of Cobalt Strike beacon samples on Virus Total were associated with 23.81.246[.]131 as part of a campaign that exploited CVE-2021-40444 to deliver Conti ransomware, a common payload for TrickBot.
In the report today, Prevailion provides additional indicators connecting the Naver phishing domains to TrickBot infrastructure revealed in public research from RiskIQ and Microsoft.
The researchers say that their findings are suggesting that the Naver phishing activity is continuing as the infrastructure is still in use and numerous domains have been registered this month for this purpose.
Prevailion notes that “this infrastructure appears to support separate, discrete campaigns” and while the overlaps with TrickBot infrastructure exist, they are limited to hosting and DNS resolutions.
The company also underlines that “the Naver-themed phishing activity that was initially discovered does not appear to be the work of a ransomware group directly.”
However, these file-encrypting attacks are often preceded by phishing or credential-stealing campaigns run by affiliates or partners seeking access to networks of valuable targets.
One theory that Prevalion believes explains their findings is that cybercriminals are relying on an “infrastructure-as-a-service” type of offering for their operations.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now