
A newly discovered Linux malware known as Symbiote infects all running processes on compromised systems, steals account credentials, and gives its operators backdoor access.
After injecting itself into all running processes, the malware acts as a system-wide parasite, leaving no identifiable signs of infection even during meticulous in-depth inspections.
Symbiote uses the BPF (Berkeley Packet Filter) hooking functionality to sniff network data packets and to hide its own communication channels from security tools.
This novel threat was discovered and analyzed by BlackBerry and Intezer Labs researchers, who worked together to uncover all aspects of the new malware in a detailed technical report. According to them, Symbiote has been under active development since last year.
System-wide infection via shared objects
Instead of having the typical form of an executable, Symbiote is a shared object (SO) library that gets loaded into running processes using the LD_PRELOAD directive to gain priority against other SOs.
By being the first to load, Symbiote can hook the "libc" and "libpcap" functions and perform various actions to conceal its presence, like hiding parasitic processes, hiding files deployed with the malware, and more.
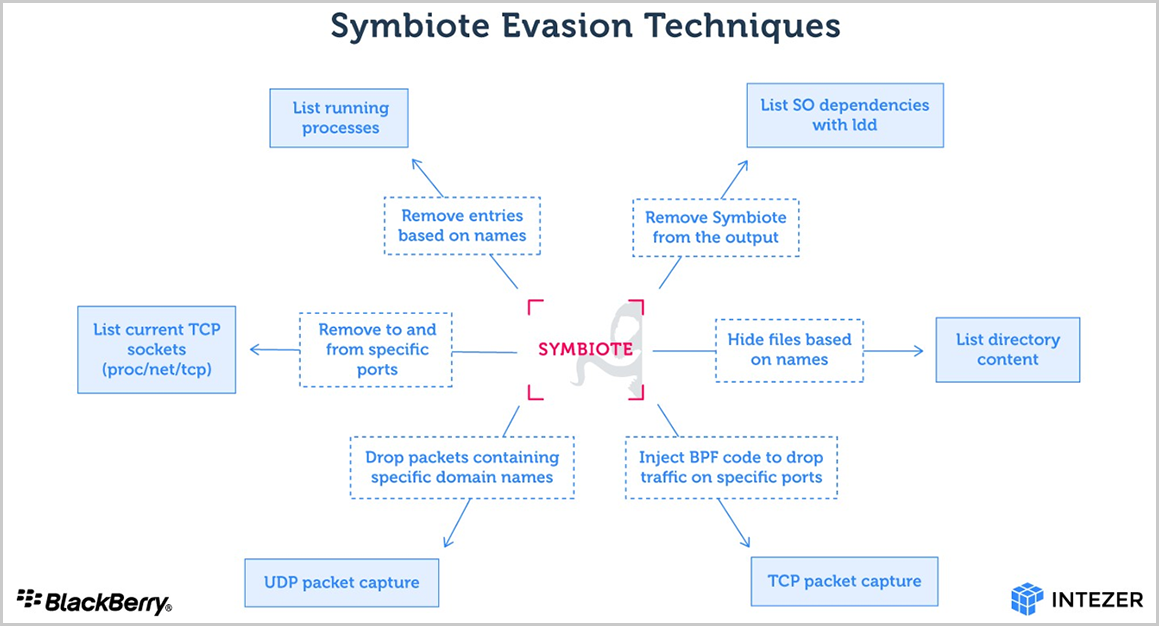
"When it injects itself into processes, the malware can choose which results it displays," the security researchers revealed in a report published today.
"If an administrator starts a packet capture on the infected machine to investigate some suspicious network traffic, Symbiote will inject itself into the inspection software's process and use BPF hooking to filter out results that would reveal its activity."
To hide its malicious network activity on the compromised machine, Symbiote scrubs connection entries it wants to hide, performs packet filtering via BPF, and removes UDP traffic to domain names in its list.
Backdoors and data theft
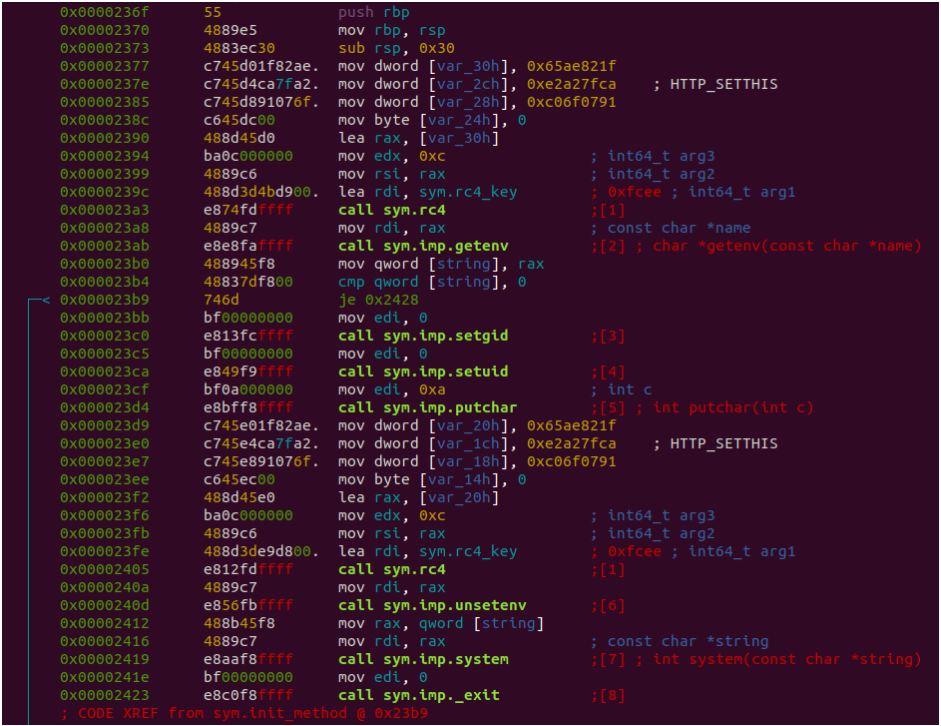
This stealthy new malware is primarily used for automated credential harvesting from hacked Linux devices by hooking the "libc read" function.
This is a crucial mission when targeting Linux servers in high-value networks, as stealing admin account credentials opens the way to unobstructed lateral movement and unlimited access to the entire system.
Symbiote also gives its operators remote SHH access to the machine via the PAM service, while it also provides a way for the threat actor to gain root privileges on the system.
The malware's targets are mostly entities engaging in the financial sector in Latin America, impersonating Brazilian banks, the country's Federal police, etc.
"Since the malware operates as a user-land level rootkit, detecting an infection may be difficult," the researchers concluded.
"Network telemetry can be used to detect anomalous DNS requests and security tools such as AVs and EDRs should be statically linked to ensure they are not 'infected' by userland rootkits."
Such advanced and highly-evasive threats used in attacks against Linux systems are expected to increase significantly in the upcoming period, as large and valuable corporate networks use this architecture extensively.
Only last month, another similar backdoor called BPFDoor was spotted using BPF (Berkeley Packet Filter) to passively listen to incoming and outgoing network traffic on infected hosts.



Comments
ComputerGeek01 - 1 year ago
So the Linux version of a preload DLL attack. It's amazing how the oldest ideas are still doing the most damage.