
Threat actors are luring potential thieves by spamming login credentials for other people account's on fake crypto trading sites, illustrating once again, that there is no honor among thieves.
This new cryptocurrency scam is gaining traction recently, involving emails and texts sharing credentials to an online trading account holding 30 Bitcoin for them to withdraw, which today trades for around $900,000.
The phishing email, seen by security analyst Jan Kopriva, informs the recipient that a deposit of 30 BTC has been added to an account on the Orbitcoin trading platform.
In the email, the crooks include a customer ID (username) and a password, essentially luring the targets into logging into the system to access the stored bitcoin.
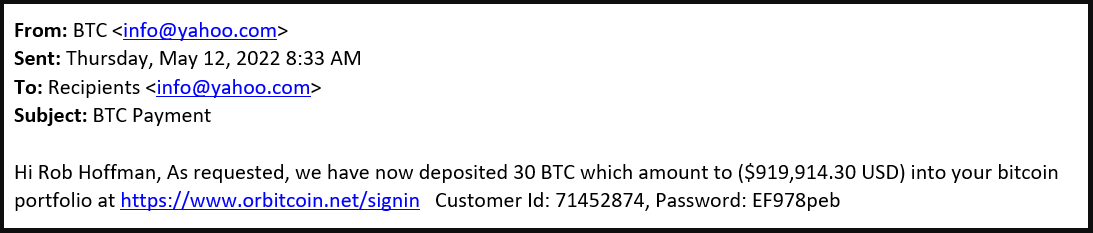
The Orbitcoin platform is fake, but the scammers have done an excellent job creating a convincing website that looks like an actual crypto exchange, at least to careless visitors.
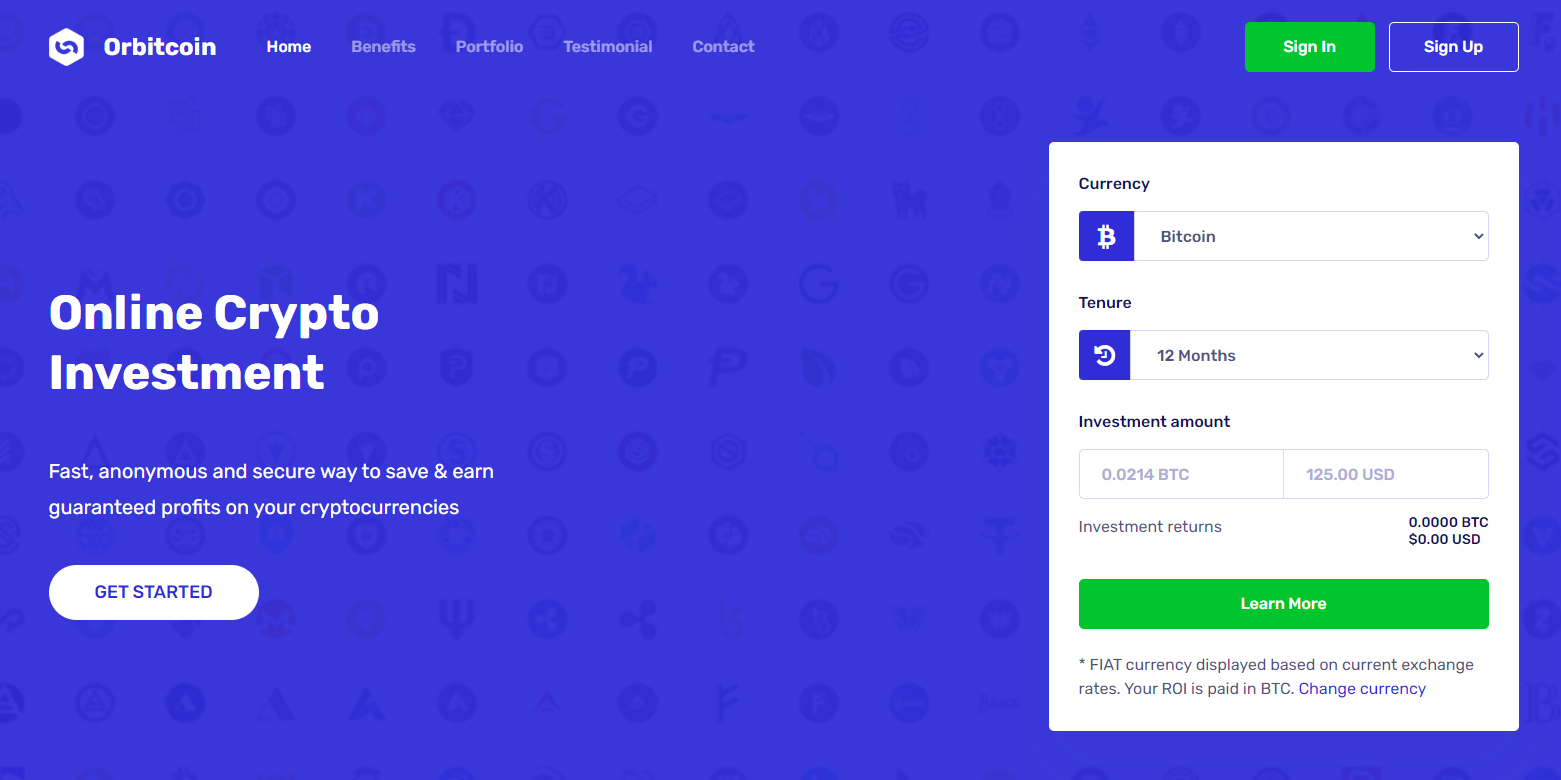
At the time of writing this, the scam site remains online, although some anti-virus tools with internet security functions flag it as malicious.
Kopriva decided to follow the steps and record his way into the scam to do a write-up on the ISC forums.
The scamming process
If the email recipient believes the message was sent to them by mistake and decides to access "Rob Hoffman's" money, they can use the sent credentials to log into the account on Orbitcoin.
After going through a two-factor authentication step via SMS or automated phone call, which further raises the simulated legitimacy of Orbitcoin, the victim is allowed to access the account.
The fake trading platform indeed displays 30 BTC as the available amount on the account, but for the first withdrawal, it doesn't allow amounts over 0.0001 BTC, supposedly for security reasons.
Because bank account withdrawals aren't available, the victim makes the transfer to a Bitcoin wallet, and they are left with 29.9999 BTC.
The trick that comes into play here is that the account owner, supposedly Rob, had set a minimum withdrawal limit of 30.006 BTC upon creating the portfolio.
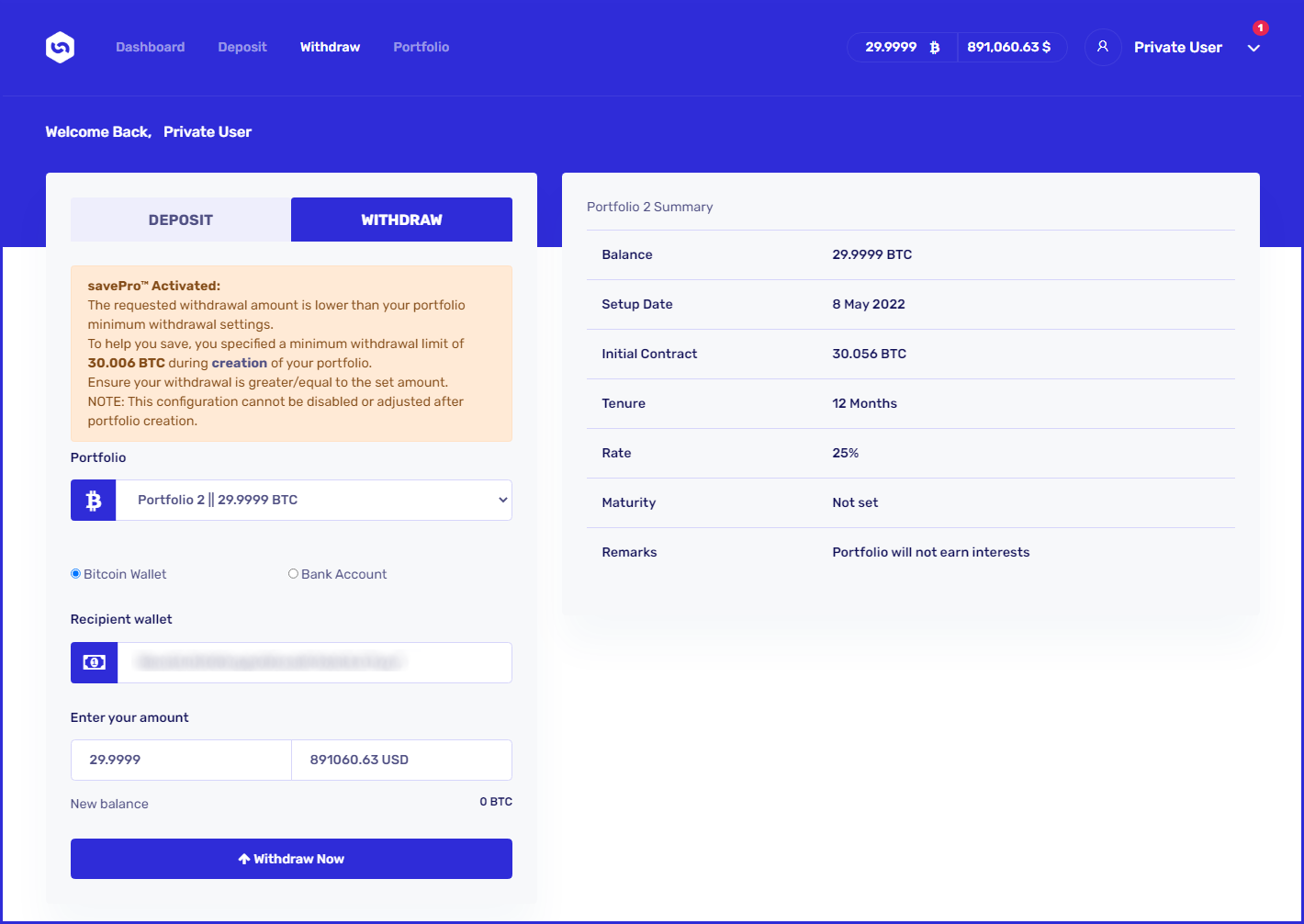
The victim believes that all they need to access the $900,000 would be to add the equivalent of roughly $180, which, of course, goes straight into the scammer's pocket.
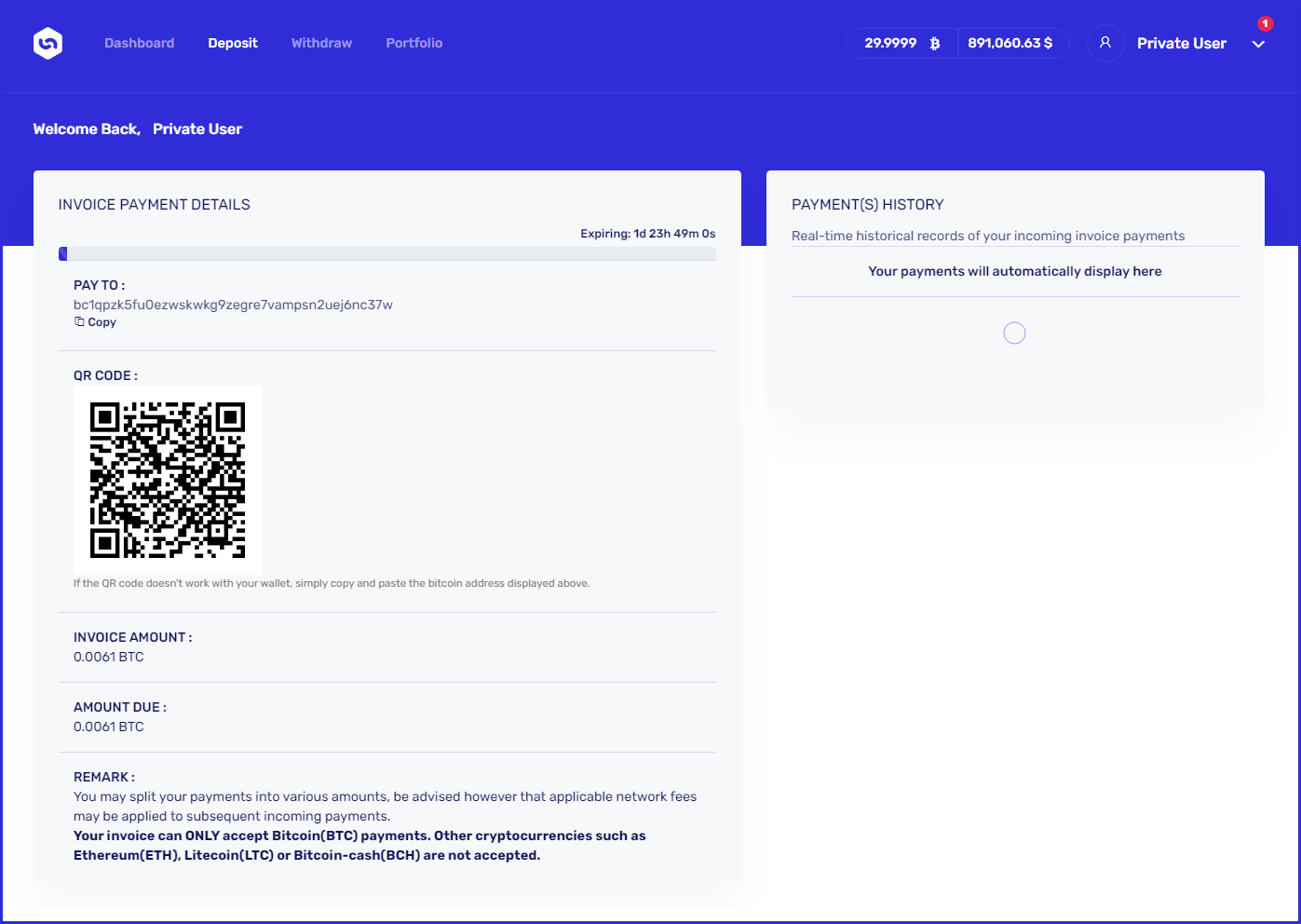
Kopriva noticed that the provided Bitcoin wallet address for depositing this amount is empty, but this could be just one of the many addresses the scammers are using, constantly rotating them to tackle reporting and evade tracing.
BleepingComputer is aware of threat actors using this scam with other cryptocurrencies, including Tether (USDT) and Ethereum.
Threat actors are also sending these scams via SMS text, with the most common website domains listed below:
usdtmnb.com
btc-banking.net
trcausdvip.com
Spotting the fraud
These campaigns are yet another example of how much effort threat actors put into their scams to look convincing, especially when they add 2FA validation, security withdrawal limits, etc.
Although users should never click on links embedded in emails, if you end up on a website this way, pay close attention to signs of fraud.
In this case, the contact section doesn't even list an email or a telephone number, making customer support agents only available from within the account dashboard.
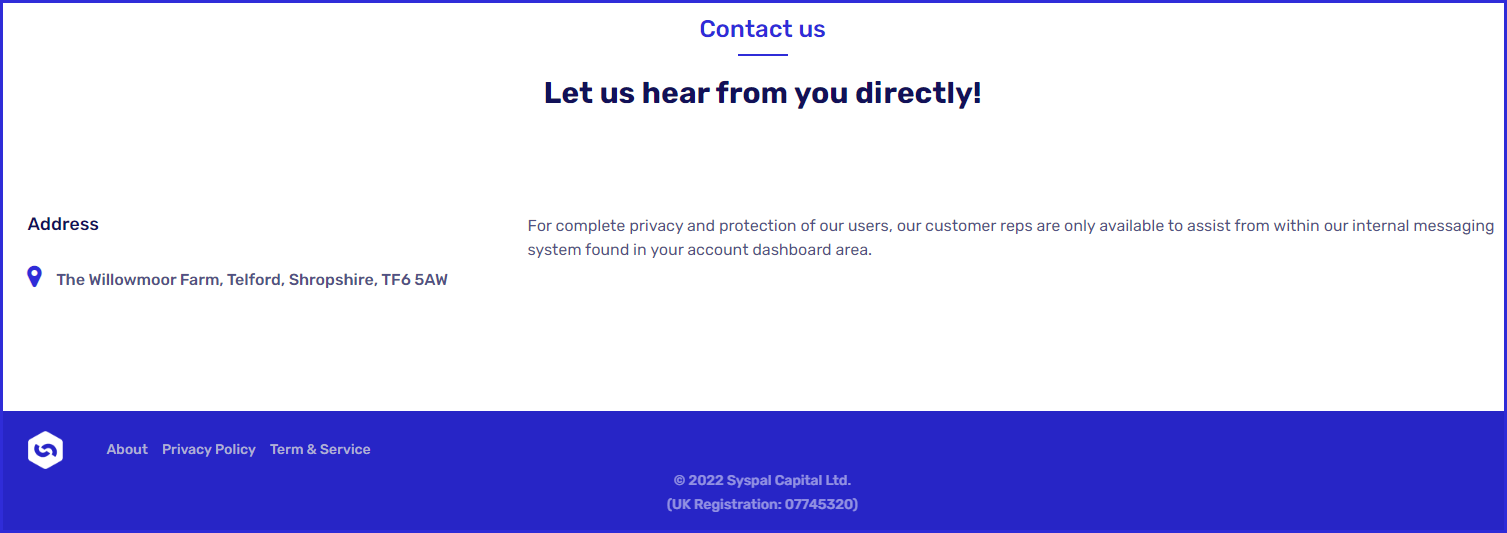
Additionally, the provided address corresponds to a horse farm in the UK, while the company registration details in the footer belong to a stainless steel product manufacturer.
Another sign of fraud would be using "Private User" as the account holder's name, which is also a potential indication that the scammers use more names besides Rob Hoffman.
The inclusion of credentials for a newly created account in the email is strange by itself, considering that Hoffman supposedly had already set a withdrawal limit, and hence, he already had access to the account.
Finally, and most important, while it may be tempting to login to the person's account and see if the funds exist, doing so could potentially be illegal, if not not ethically wrong, to do so.



Comments
scr-dev - 1 year ago
now they are using a new domain. i received a supposed email as mentioned above. sites that are being used: https://www.coinfist.net