
The Google Threat Analysis Group (TAG) says more and more threat actors are now using Russia's war in Ukraine to target Eastern European and NATO countries, including Ukraine, in phishing and malware attacks.
The report's highlight are credential phishing attacks coordinated by a Russian-based threat group tracked as COLDRIVER against a NATO Centre of Excellence and Eastern European militaries.
The Russian hackers also targeted a Ukrainian defense contractor and several US-based non-governmental organizations (NGOs) and think tanks.
"Government-backed actors from China, Iran, North Korea and Russia, as well as various unattributed groups, have used various Ukraine war-related themes in an effort to get targets to open malicious emails or click malicious links," Google TAG Security Engineer Billy Leonard said.
As the Google threat analysts also observed, Curious Gorge, a hacking group linked to China's PLA SSF (People's Liberation Army Strategic Support Force), targeted government and military organizations from Ukraine, Russia, Kazakhstan, and Mongolia.
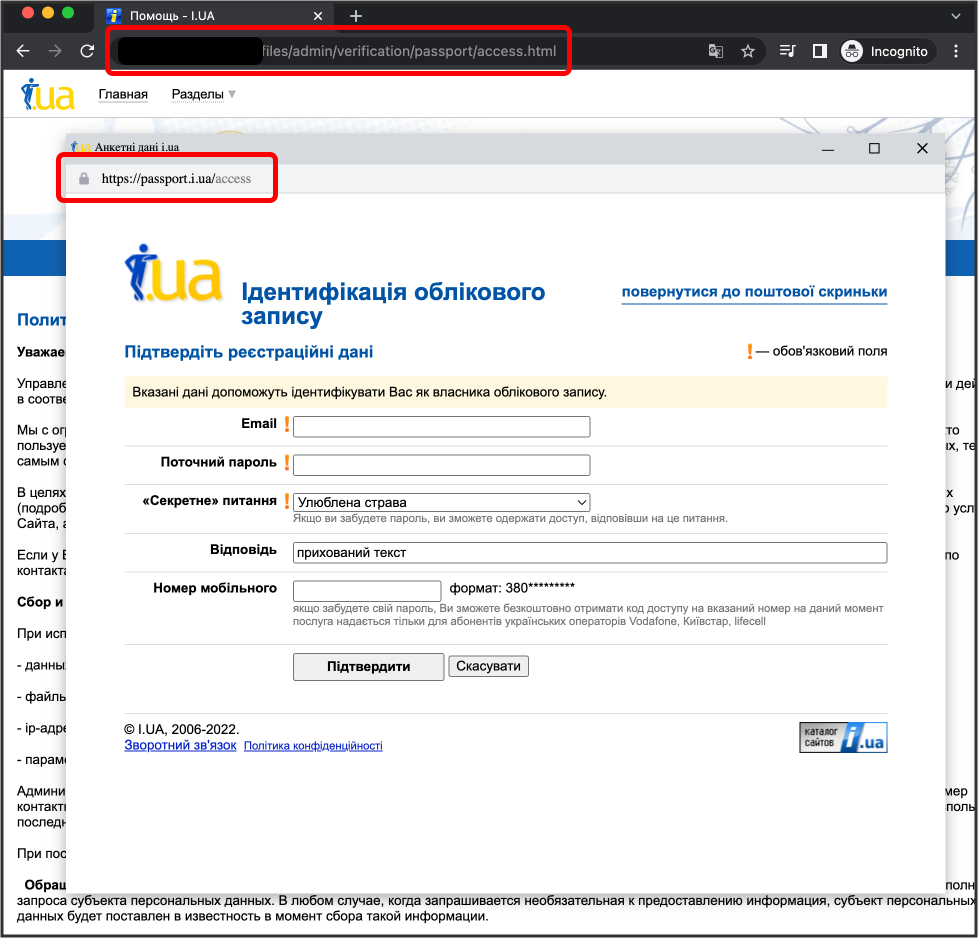
Ghostwriter, a Belarusian-backed threat actor, was seen using a relatively new phishing technique known as Browser in the Browser (BitB) phishing, publicly disclosed in mid-March and also adopted by other government-sponsored APTs.
The Belarusian state hackers' credential phishing campaigns have previously targeted Ukrainian officials and military personnel [1, 2] and European refugee aid officials.
"Financially motivated and criminal actors are also using current events as a means for targeting users. For example, one actor is impersonating military personnel to extort money for rescuing relatives in Ukraine," Leonard added.
"TAG has also continued to observe multiple ransomware brokers continuing to operate in a business as usual sense."
Previous malicious activity against Ukraine and other countries
Today's report follows another one Google TAG published regarding malicious activity linked to the Russian war in Ukraine from early March that exposed Russian, Chinese, and Belarus state hackers' efforts to compromise Ukrainian and European organizations and officials.
Google also revealed this month that it warned Gmail users affiliated with the US government they were targeted in phishing attacks coordinated by the Chinese-backed APT31 hacking group.
As we previously reported, this flood of attacks has also included distributed denial-of-service (DDoS) attacks targeting the Ukrainian government and state-owned banks, as well as multiple campaigns of destructive malware attacks [1, 2].
"DDoS attempts against numerous Ukraine sites, including the Ministry of Foreign Affairs, Ministry of Internal Affairs, as well as services like Liveuamap that are designed to help people find information" were also observed by Google since the start of the Russian war in Ukraine.
Google expanded eligibility for Project Shield, its free DDoS protection service to help the Ukrainian government, embassies worldwide, and other governments keep their websites online.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now